Threat Modeling
A categorization model, which describes the threats to an organization, and why and how these threats become vulnerable. Threat modeling, is attack-centric. Threat modeling is usually applied to software applications, but it can be used for operating systems, and devices.
Threat modeling also helps design architects to identify the threats, potential security issues, and vulnerabilities. This optimization is cost-effective.
While there are different approaches to threat modeling, the typical steps are:
- Objective identification & assessment scope
- Identify threat agents and possible attacks
- Understand existing countermeasures
- Identify exploitable vulnerabilities
- Prioritized identified risks
- Remediation of threats
There are several methodologies in threat modeling:
- STRIDE
- PASTA
- Trike
STRIDE Methodology
A methodology of threat modeling developed by Microsoft for security threats of six categories:
- Spoofing
- Tampering
- Repudiation
- Information disclosure
- Denial of service (DoS)
- Elevation of privilege
Process for Attack Simulation and Threat Analysis
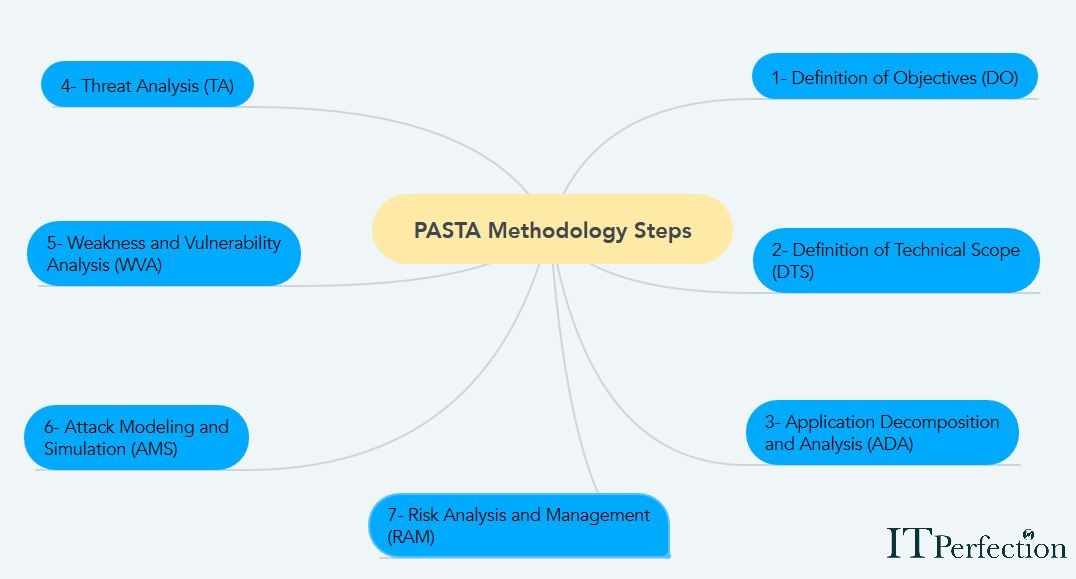
PASTA is a risk-centric methodology. Once the process of threat modeling, PASTA brings a detailed analysis of identified threats. The following figure lists the seven-steps of PASTA methodology:
Trike Methodology
An open source threat modeling methodology and tool. Threat models are based on a “requirements model” that yields a threat model form, and threats are enumerated and then assigned risk values.
Visual, Agile, & Simple Threat (VSAT)
There are two types of threat models:
- Application threat models
- Operational threat models
This Methodology is very useful and powerful for organizations that need thousands of threat models.
The pillars of a scalable process, automation, integration, and collaboration are foundational to VAST.
Minimum Security Requirements
Before accessing services, agreeing or initiating any process with a third party, the organization must evaluate he/ she in every way. The three main ones are:
- The third-party assessor must be certified in Information Security Management System (in accordance to ISO/IEC 27001: 2005).
- Third parties should be willing to comply with the organization’s security policies & procedures.
- Third parties should have certified personnel in information security areas.
Following are the key components of Third-Party Risk Management (TPRM) Framework:
- Planning & processes definition
- Segmentation & Screening
- Qualification
- Security & Permissions
- Workflows
- Risk Mitigation
- Continuous Monitoring
- Reports & Dashboard
- Centralized Repository
- Alert & Notification
Security Awareness, Education & Training
Security awareness is usually an unnoticed factor in an information security program so users can become the weakest link in an information security program.
The three main components of a good security awareness program are:
- A general awareness program
- Formal training
- Education
General Awareness Program
Awareness programs may include the following elements:
- Indoctrination and orientation: At this stage, employees and contractors are formally informed about the organization’s security policies, must read and sign the agreement on non-disclosure of information, and must finally attend a briefing with employees of the Security and IT Team.
- Presentations: Lectures, video presentations, and interactive Computer-Based Training (CBTs).
- Printed materials: Security posters, corporate newsletters, and periodic bulletins.
Formal Training
Formal training programs may include:
- Classroom training: Instructor-led.
- On-the-job training: Usually one-on-one mentoring with a peer or immediate supervisor.
- Technical or vendor training: Training on a specific product or technology provided by a third party.
Apprenticeship or qualification programs: Formal probationary status or qualification standards.
Education
An education program may include:
- Continuing education requirements: Continuing Education Units (CEUs) are becoming popular for maintaining high-level technical or professional certifications such as the CISSP.
- Formal education or degree requirements: Many companies offer tuition assistance or scholarships.
- Certificate programs: Many colleges and universities offer adult education programs that have classes about current and relevant subjects for working professionals.
