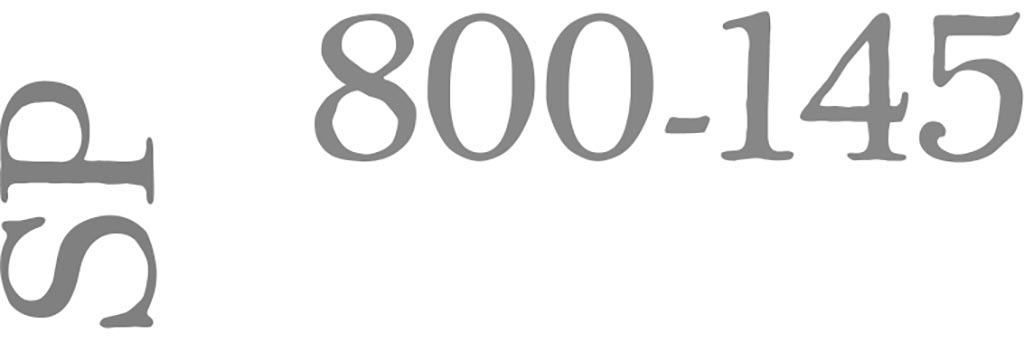Familiarity with Dell Servers
In this blog, we are going to have an overview of the most popular servers of the famous Dell Company. Dell is an American multinational computer technology company that develops, sells, repairs, and supports computers and related products and services, and It is one of the biggest PC product companies in [...]
HP Servers- Part 3: HPE Tower Servers, HPE SimpliVity, HPE Nimble Storage dHCI
Now we have to talk about HPE Tower Servers, HPE SimpliVity, and finally HPE Nimble Storage dHCI. To make you more familiar with the concepts of network physical servers and to get acquainted with the reputable vendors of network servers, we have prepared a number of blogs as a series, [...]
HP Servers – Part 2: HPE Proliant Servers Family, HPE Rack Servers
And HPE Proliant servers. To make you more familiar with the concepts of network physical servers and to get acquainted with the reputable vendors of network servers, we have prepared a number of blogs as a series, the different parts of which are as follows: Part 1: Concepts Part 2: [...]
HP Servers- Part 1: Concepts
To make you more familiar with the concepts of network physical servers and to get acquainted with the reputable vendors of network servers, we have prepared a number of blogs as a series, the different parts of which are as follows: Part 1: Concepts Part 2: HPE Proliant Servers Family, [...]
Network Routing: Part 5- HP Routers: Branch, Campus, Data Center, Virtual and Small Business
To make you more familiar with the concepts of network routing and to get acquainted with the reputable vendors of network routers, we have prepared a number of blogs as a series, the different parts of which are as follows: Part 1 - What is a Network Router? Routing Terms [...]
Network Routing: Part 4- Mikrotik Routers: RB Routers, CCR Routers, PowerBox Routers and hEX Routers
To make you more familiar with the concepts of network routing and to get acquainted with the reputable vendors of network routers, we have prepared a number of blogs as a series, the different parts of which are as follows: Part 1 - What is a Network Router? Routing Terms [...]
Network Routing: Part 3 – Other Cisco Routers: Service Provider, Small Business, Virtual, WAN
To make you more familiar with the concepts of network routing and to get acquainted with the reputable vendors of network routers, we have prepared a number of blogs as a series, the different parts of which are as follows: Part 1 - What is a Network Router? Routing Terms [...]
Network Routing- Part 2 – Cisco Routers: Branch Routers, Industrial Routers, and Network Functions Virtualization
To make you more familiar with the concepts of network routing and to get acquainted with the reputable vendors of network routers, we have prepared a number of blogs as a series, the different parts of which are as follows: Part 1 - What is a Network Router? Routing Terms [...]
Network Routing: Part 1 – What is a Network Router? Routing Terms (Such as Routing Protocols, and Types of Routers)
To make you more familiar with the concepts of network routing and to get acquainted with the reputable vendors of network routers, we have prepared a number of blogs as a series, the different parts of which are as follows: Part 1 - What is a Network Router? Routing Terms [...]
What’s HPE iLO?
Integrated Lights-Out, or iLO, is a proprietary embedded server management technology by HP (Hewlett-Packard) which provides out-of-band management facilities. HP iLO is combination of the iLO ASIC that is part of the server-board and the firmware that powers the ASIC. iLO is key to make the server operational and boot [...]
Network Switching: Part 11- Dell Switches: PowerSwitch Data Center Switches, and PowerEdge M-Series Blade Switches
To make you more familiar with the concepts of network switching and to get acquainted with the reputable vendors of network switches, we have prepared a number of blogs as a series, the different parts of which are as follows: Part 1 - What is a Network Switch? Switching Terms [...]
Network Switching: Part 10 – Dell Switches: Concepts and Technologies, and PowerSwitch Managed Campus
To make you more familiar with the concepts of network switching and to get acquainted with the reputable vendors of network switches, we have prepared a number of blogs as a series, the different parts of which are as follows: Part 1 - What is a Network Switch? Switching Terms [...]
Network Switching: Part 9 – HP Switches: Core & Data Center Switches ( Such as Aruba CX 8400 Series, and Aruba CX 8320 Series)
To make you more familiar with the concepts of network switching and to get acquainted with the reputable vendors of network switches, we have prepared a number of blogs as a series, the different parts of which are as follows: Part 1 - What is a Network Switch? Switching Terms [...]
Network Switching: Part 8 – HP Switches: Terms, and Access Switches ( Such as Aruba CX 6400 Series, and Aruba 5400R Series )
To make you more familiar with the concepts of network switching and to get acquainted with the reputable vendors of network switches, we have prepared a number of blogs as a series, the different parts of which are as follows: Part 1 - What is a Network Switch? Switching Terms [...]
Network Switching: Part 7 – Mikrotik Switches: Terms, and Also Switches such as RB260GSP, or CRS305-1G-4S+IN
To make you more familiar with the concepts of network switching and to get acquainted with the reputable vendors of network switches, we have prepared a number of blogs as a series, the different parts of which are as follows: Part 1 - What is a Network Switch? Switching Terms [...]
Network Switching: Part 6 – Cisco Switches: Other Switches (Industrial Ethernet, InfiniBand , Small Business, Service Provider (Aggregation, and Ethernet Access)
Network Switching To make you more familiar with the concepts of network switching and to get acquainted with the reputable vendors of network switches, we have prepared a number of blogs as a series, the different parts of which are as follows: Part 1 - What is a Network Switch? [...]
Network Switching: Part 5: Cisco Switches: Campus LAN Switches (Terms, Core and Distribution), and Data Center Switches
To make you more familiar with the concepts of network switching and to get acquainted with the reputable vendors of network switches, we have prepared a number of blogs as a series, the different parts of which are as follows: Part 1 - What is a Network Switch? Switching Terms [...]
Network Switching: Part 4: Cisco Switches: Concepts, Blade Switches, and Campus LAN Switches (Access)
To make you more familiar with the concepts of network switching and to get acquainted with the reputable vendors of network switches, we have prepared a number of blogs as a series, the different parts of which are as follows: Part 1 - What is a Network Switch? Switching Terms [...]
Network Switching: Part 3: Types of Categories of Switches, Such as Stackable Switches, or Access Layer Switches
Now, Categories of Switches. To make you more familiar with the concepts of network switching and to get acquainted with the reputable vendors of network switches, we have prepared a number of blogs as a series, the different parts of which are as follows: Part 1 - What is a [...]
Network Switching: Part 2: What is a Network Switch? Switching Terms (Such as PoE, VLAN, and STP)
To make you more familiar with the concepts of network switching and to get acquainted with the reputable vendors of network switches, we have prepared a number of blogs as a series, the different parts of which are as follows: Part 1 - What is a Network Switch? Switching Terms [...]
Network Switching: Part 1: What is a Network Switch? Switching Terms (Such as Blade Server, Half Duplex, and Full Duplex)
To make you more familiar with the concepts of network switching and to get acquainted with the reputable vendors of network switches, we have prepared a number of blogs as a series, the different parts of which are as follows: Part 1 - What is a Network Switch? Switching Terms [...]
TDoS Attack
In this post, we are going to talk about TDoS attack. First of all, we recommend that you read our other post, in which we describe the DoS and DDoS attacks: DoS and DDoS Attacks In its annual report "Internet Crime Report" for 2019, the U.S. Federal Bureau of Investigation [...]
What is John the Ripper and How Does it Work?
John the Ripper is a free password cracking software tool. It was designed to test password strength, brute-force encrypted (hashed) passwords, and crack passwords via dictionary attacks. John the Ripper is a part of the Rapid7 family of penetration testing/ hacking tools. Also, John is already installed on Kali Linux. [...]
What is Kali Linux?
Kali Linux is a Debian-derived Linux distribution designed for digital forensics and penetration testing. It is maintained and funded by Offensive Security,a leading information security training company. In fact, it’s a Debian-based rewrite of their previous Knoppix-based digital forensics and penetration testing distribution BackTrack. One of the biggest reasons cyber [...]
What is NESSUS and How Does it Work?
Nessus is a proprietary vulnerability scanner developed by Tenable, Inc. Tenable.io is a subscription-based service. Tenable also contains what was previously known as Nessus Cloud, which used to be Tenable’s Software-as-a-Service solution. Nessus is an open-source network vulnerability scanner that uses the Common Vulnerabilities and Exposures architecture for easy cross-linking [...]
Vulnerability Scanning Tools
We discussed vulnerability scanning in recent blog. Now in this blog we are going to introduce a number of vulnerability scanning tools. What is Network Vulnerability Scanning? Among the famous tools in this area are the following: SolarWinds MSP OpenVAS Nikto Retina products Solarwinds Network Configuration Manager Nexpose Community Edition [...]
What is Network Vulnerability Scanning?
Vulnerability management is a key responsibility of any IT security team or managed security service provider. This scanning is an inspection of the potential points of exploit on a computer or network to identify security holes. Vulnerability scanning is an integral component of vulnerability management. In fact, a scanner is [...]
The Best of NetFlow Tools
NetFlow is a network protocol that collects information about your network’s IP traffic and monitors network traffic activity. In this blog, we are going to review a number of NetFlow tools. We have already posted a blog about NetFlow on this site, which we recommend you read before continuing to [...]
Network Monitoring and Performance Management (NPM)Tools – Part 4
In these four blogs, we are going to talk about the main features of NPM tools and, as far as possible, compare some popular software in this area. In these four blogs, we are going to talk about the main features of a network management and monitoring software and, as [...]
Network Monitoring and Performance Management (NPM) Tools – Part 3
In these four blogs, we are going to talk about the main features of a performance management tools and monitoring software and, as far as possible, compare some popular software in this area. In these four blogs, we are going to talk about the main features of a network management [...]
Network Monitoring and Performance Management (NPM) Tools – Part 2
In these four blogs, we are going to talk about the main features of a network management and monitoring tools and, as far as possible, compare some popular software in this area. In these four blogs, we are going to talk about the main features of a network management and [...]
Network Monitoring and Performance Management (NPM) Tools – Part 1
Every network performance monitoring (NPM) solution allows companies to discover performance issues on a network as they occur. The more advanced network monitoring tools will be pumped with features that make performance tracking easier or more comprehensive. In these four blogs, we are going to talk about the main features of [...]
Auvik
In this post, we are going to introduce you to a powerful tool in the field of network monitoring. It is better to read this blog first of all: Network Monitoring. The tool we are going to discuss is called Auvik network management and monitoring. It is a cloud-based software. [...]
What is CVE?
The Common Vulnerabilities and Exposures (CVE) system identifies all vulnerabilities and threats related to the security of information systems. This system provides a reference-method for publicly known information-security vulnerabilities and exposures. The catalog is sponsored by the United States Department of Homeland Security (DHS). This system was officially launched for [...]
What’s SNMP?
Network admins generally manage the devices in a network and allocate and free up ports and interfaces to ensure continuous uptime and bandwidth-hog-free network operations. Closely monitoring SNMP devices is a major part of this. Simple Network Management Protocol (SNMP) is an Internet Standard protocol for collecting and organizing information [...]
Email Tracking
Email tracking is a method for monitoring the delivery of email messages to the intended recipient. Email tracking means monitoring opens and clicks of emails to follow up with leads, job applicants, and partners. In other words, email tracking is the process of tracking sent emails and using [...]
What is Footprinting? What is Reconnaissance?
Footprinting (also known as reconnaissance) commonly refers to one of the pre-attack phases; tasks performed before doing the actual attack. In other words, footprinting is the first step in the evaluation of the security posture of the target organization's IT infrastructure. During this phase, a hacker can collect the following [...]
All we should know about HIPAA Compliance
The Health Insurance Portability And Accountability Act (HIPAA) compliance a legislation which provides security provisions and data privacy, in order to keep patients’ medical information safe. The law has emerged into greater prominence in recent years with the proliferation of health data breaches caused by cyberattacks and ransomware attacks on [...]
DoS and DDoS Attacks
A denial-of-service attack (DoS attack) is a cyber-attack in which the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host connected to the network or Internet. Also, a Distributed Denial of Service (DDoS) attack is an [...]
Technical Support Scam
A technical support scam refers to any class of telephone fraud activities in which a scammer claims to offer a legitimate technical support service. The scammers may pretend to be from a well-known tech company, such as Microsoft. The scammer will typically attempt to get the victim to allow remote [...]
Features of a Powerful Anti-malware
There are small and large manufacturers that produce powerful anti-malware. So you have to choose one of the products of these manufacturers. There are not many differences between the products of these manufacturers in terms of quality. In fact, there is a very close competition between these products. In this [...]
Everything About Managing User Accounts in Windows 10
Creating and managing user accounts is one of the most important steps in securing a computer. You need to be able to create a work account on your PC and manage its various aspects (such as password and expiration time, access level). The subject of this post is creating and [...]
8-Steps to Secure Your Computer
8-Step to Secure Your Computer Whether you use your computer primarily for work tasks or personal use or both, it’s highly likely you want to keep it and its contents safe and secure. Keeping your computer secure helps you avoid malware and direct hacking attempts designed to steal your personal [...]
Introduction of Several Encryption Software
Encryption software is software that uses cryptography to prevent unauthorized access to digital information. We have already discussed the concepts of cryptography in detail in a separate post: Data Encryption. Software encryption uses a cipher to obscure the content into cipher-text. Ciphers are into two categories: Public key (Asymmetric) ciphers: [...]
BitLocker Drive Encryption
BitLocker Drive Encryption is a tool in the Windows operating system for encrypting the entire contents of a drive from a computer hard drive. In this post, we do not intend to discuss the concepts of cryptography. You can read this post to understand these concepts. This tool in Windows [...]
Properties of a Strong Password
One of the most important ways to ensure that your online interactions are safe and secure is to protect your passwords. Also, the more powerful your password, the harder it is for a hacker to invade your system. A strong password: Is at least 12 characters long Is a combination [...]
Privacy and Security Settings in Safari
The subject of this post is to review the privacy settings as well as security settings in the Apple Safari web browser. This browser does not offer many settings in these two areas, but this does not mean that this browser is not reliable in terms of security. In fact, [...]
Privacy and Security Settings in Internet Explorer
The subject of this post is to review the privacy settings as well as security settings in the Internet Explorer 11 web browser. This web browser provides many settings in these two areas for its users, the most important of which we examine. In Tools menu, click [...]
Privacy and Security Settings in Google Chrome
The subject of this post is to review the privacy settings as well as security settings in the popular google chrome web browser. This web browser provides many settings in these two areas for its users, the most important of which we examine. To enter the privacy settings as well [...]
Privacy and Security Settings in Firefox
The subject of this post is to review the privacy settings as well as security settings in the popular Firefox web browser. This web browser provides many settings in these two areas for its users, the most important of which we examine. Source: Mozilla Firefox official website These are the [...]
DMZ Networks
The subject of this post is DMZ networks. But what exactly are the DMZ networks? DMZ ((DeMilitarized Zone) is essentially a military and political term meaning a civilian area. The most famous example of a demilitarized zone right now is the demilitarized zone on the border between South Korea and [...]
5 Backup Software (for Home/Personal Computer)
In this post, we are going to introduce you to five powerful backup software. All of these applications are suitable for home and personal computers. Acronis True Image is one of best backup tools. Acronis official website This software has a good desktop interface and working with [...]
Create & Restore Backup in Windows 10
You need to be able to back up your sensitive data. You should also be able to restore that backup if necessary. The subject of this post is to teach you how to back up data in Windows 10 as well as recover it. Backup your PC with [...]
Watchguard Firewall
We have introduced several hardware firewalls on this website so far. In this post also, we intend to do the same. Watchguard is one of the well-known manufacturers of network security products. We have examined several well-known firewalls in the network world. Now it is time to check the firewalls [...]
Software Firewalls
You know that firewalls exist in both as software and as hardware devices. Each has its advantages and disadvantages. In general, the use of software firewalls for home use, personal use and small businesses is recommended, as well as the use of hardware firewalls for medium and large businesses. To [...]
Familiarity with Anti-malwares (Home solutions) – Part II
In the previous post, we reviewed the products of five manufacturers. We now intend to review the products of five other companies. See also: Familiarity with Anti-malwares (Home solutions) - Part I ESET is a Slovak internet security company that offers anti-virus and firewall products. ESET is [...]
Familiarity with Anti-malwares (Home solutions) – Part I
Another step to secure your personal computer (desktop or laptop) as well as your tablet and mobile phone is to use anti-malware. The anti-malware industry is a relatively old industry, and over the decades many anti-malware manufacturers have become very experienced and powerful. The good news for us end users [...]
Cisco ASA Firewalls
This post is about Cisco Firewalls. It aggregates available information from datasheets published by Cisco. The ASA in Cisco ASA stands for Adaptive Security Appliance. We suggest that you read the following two posts before continuing to read this post: All Things about Firewall Hardware Firewalls In fact, Cisco ASA is [...]
Network Inventory Tool: LANsweeper
Each network administrator wishes to be able to document the assets related to the computer network in such a way that this documentation always: Be up to date Be reliable Be available This can be done manually: someone examines the assets and records them on a piece of paper or [...]
Network Monitoring Tools: Veaam ONE
So far, we have introduced and reviewed several software packages for network monitoring in our posts. In this post, we are going to discuss another powerful software package: Veeam ONE. Veeam ONE, part of Veeam Availability Suite, provides comprehensive monitoring and analytics for your backup, virtual and physical environments. Veeam [...]
How to Comply with PCI DSS
This post presents How to comply with PCI DSS. This article is a summary from of the pcisecuritystandards.org website. With the following link: PCI DSS Quick Reference Guide For more info please refer to pcisecuritystandards.org We recommend you that before continuing, read this post. Each payment card brand maintains its [...]
Security Controls and Processes for PCI DSS Requirements
We already have a post called PCI-DSS that you can read it here. Now, in this post, we are going to get acquainted with the security controls and processes required for a PCI-DSS implementation. This post presents the objectives of PCI DSS and related 12 requirements. This article is a [...]
VPN
A virtual private network (VPN) extends a private network across a public network and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. In other words, A Virtual Private Network is a connection method used [...]
HIPAA Privacy Rule- Part 3
This post is a summary of key elements of the HIPAA Privacy Rule including who is covered, what information is protected, and how protected health information can be used and disclosed. This article is a summary from of the hhs.gov website. With the following link: Summary of the HIPAA Privacy Rule [...]
HIPAA Privacy Rule- Part 2
This post is a summary of key elements of the HIPAA Privacy Rule including who is covered, what information is protected, and how protected health information can be used and disclosed. This article is a summary from of the hhs.gov website. With the following link: Summary of the HIPAA Privacy Rule [...]
HIPAA Privacy Rule- Part 1
This post is a summary of key elements of the HIPAA Privacy Rule including who is covered, what information is protected, and how protected health information can be used and disclosed. This article is a summary from of the hhs.gov website. With the following link: Summary of the HIPAA Privacy Rule [...]
HIPAA Series Security Standards: Implementation for the Small Provider
In this post we are going to talk about Implementation for the Small Provider. This post is the seventh post in the HIPAA series. This series of posts is called the HIPAA Series. The series will contain seven post: Security 101 for Covered Entities Security Standards: Administrative Safeguards Security Standards: [...]
HIPAA Series – Basics of Risk Analysis and Risk Management
HIPAA Series - Basics of Risk Analysis and Risk Management In this post we are going to talk about Basics of Risk Analysis and Risk Management. This post is the sixth post in the HIPAA series. This series of posts is called the HIPAA Series. The series will contain seven [...]
HIPAA Series – Security Standards: Organizational, Policies and Procedures and Documentation Requirements
In this post we are going to talk about Organizational, Policies and Procedures and Documentation Requirements. This post is the Fifth post in the HIPAA series. This series of posts is called the HIPAA Series. The series will contain seven post: Security 101 for Covered Entities Security Standards: Administrative Safeguards [...]
HIPAA Series – Security Standards: Technical Safeguards
In this post we are going to talk about technical Safeguards. This post is the fourth post in the HIPAA series. This series of posts is called the HIPAA Series. The series will contain seven post: Security 101 for Covered Entities Security Standards: Administrative Safeguards Security Standards: Physical Safeguards Security [...]
HIPAA Series – Security Standards: Physical Safeguards
In this post we are going to talk about Physical Safeguards. This post is the third post in the HIPAA series. This series of posts is called the HIPAA Series. The series will contain seven post: Security 101 for Covered Entities Security Standards: Administrative Safeguards Security Standards: Physical Safeguards Security [...]
HIPAA Series – Security Standards: Administrative Safeguards
In this post we are going to talk about Administrative Safeguard. This post is the second post in the HIPAA series. This series of posts is called the HIPAA Series. The series will contain seven post: Security 101 for Covered Entities Security Standards: Administrative Safeguards Security Standards: Physical Safeguards Security [...]
HIPAA Series: Security 101 for Covered Entities
In this post we are going to talk about Security 101 for Covered Entities. We start a series of posts with this post. This series of posts is called the HIPAA Series. The series will contain seven post: Security 101 for Covered Entities Security Standards: Administrative Safeguards Security Standards: Physical [...]
HIPAA: Medical Security
HIPAA law was created to ensure that patient’s sensitive information is protected. Protected health information (PHI) must be secured in the form of administrative, physical, and technical safeguards. It's better that before continuing to read this post, first read our previous post about HIPAA. The Health Insurance Portability and Accountability Act [...]
Five Phases of Ethical Hacking
In this post, we talked about the types of hackers. One of them is ethical hacker. We discuss about the five steps of ethical hacking now. Of course, not necessarily a hacker has to follow these 5 steps in a sequential manner: Note: Hacking is illegal. The only purpose [...]
Hacking & Hackers
Hacking refers to activities that seek to compromise digital devices, such as computers, smartphones, tablets, and even entire networks. In other words, hacking is identifying weakness in computer systems or networks to exploit its weaknesses to gain access. Businesses need to protect themselves against such attacks. Hacking is typically technical [...]
Mobile Device Management (MDM) Solutions
Mobile devices come with their own set of problems, such as unauthorized data access and data leakage, which highlights the importance of managing these devices. Mobile device management (MDM) is a software application for the administration of mobile devices, such as smartphones, tablet computers and laptops. MDM includes storing essential [...]
Honeypot
A honeypot is a trap that an IT security professionals lays for a malicious hacker. A honeypot is a decoy computer system for trapping hackers or tracking unconventional or new hacking methods. It's a sacrificial computer system that’s intended to attract cyberattacks, like a decoy. The goal is to deceive [...]
Basics of Network Security
It is essential for all organizations to protect their networks. With hackers increasing and becoming smarter day by day, the need to utilize network security tool becomes more and more impotent. Network security is any activity designed to protect the usability and integrity of network and data. In fact, network [...]
Brute Force Attack
A brute force attack (exhaustive search) is a cryptographic hack that relies on guessing possible combinations of a targeted password until the correct password is discovered. This attack uses trial-and-error to guess login info, encryption keys, or find a hidden web page. Brute force attacks don’t employ an intellectual strategy. [...]
IT Security Baselines
All organizations are need to keep their apps and devices secure. These apps/ devices must be compliant with the security baselines defined by the organization. A security configuration checklist (lockdown or hardening guide or benchmark) is form a series of instructions for configuring a product to a particular security baseline. IT [...]
Trusted Platform Module (TPM)
TPM stands for trusted platform module. TPM also called is ISO/IEC 11889. TPM is an international standard for a secure cryptoprocessor, a dedicated microcontroller designed to secure hardware through integrated cryptographic keys. A TPM is actually a microchip on the motherboard of most servers and even today's clients. The main [...]
IPsec Protocol
Internet Protocol Security (IPsec) is a secure network protocol suite that authenticates and encrypts the packets of data to provide secure encrypted communication between two computers/networks. IPsec is usually used to set up VPNs, and it works by encrypting IP packets, along with authenticating the source where the packets come [...]
TOR Project
We recently had a post about the dark web that mentioned the Tor project. Tor is free and open-source software for enabling anonymous communication. The name derived from the acronym for the original software project name "The Onion Router". Tor was originally developed by the US Navy in the mid-1990s. [...]
NIST SP 800-50
The National Institute of Standards and Technology (NIST) is a non-regulatory agency of the United States Department of Commerce. This Institute develops technology, metrics, and standards to drive innovation and economic competitiveness at U.S.-based organizations in the science and technology industry. For example, one of NIST’s roles is to develop [...]
NIST SP 800-145 (Cloud Computing Definitions)
Recent our posts were about NIST SP 800-137 and NIST SP 800-53A. In this post, we are going to review NIST SP 800-145. The title of this article is: Evaluation of Cloud Computing Services. This publication published in 2010. The PDF file of this publication consists of 32 pages and 7 [...]
NIST SP 800–53A
Our previous post was about NIST SP 800-137. In this post, we are going to review NIST SP 800-53A. NIST SP 800-53 is shorthand for the National Institute of Standards and Technology Special Publication 800-53, Security and Privacy Controls for Federal Information Systems and Organization. NIST SP 800-53 is a [...]
What’s ISCM? (NIST SP 800-137)
First of all, it's better to talk about what NIST is and why the content published by NIST is important. The National Institute of Standards and Technology (NIST) is a non-regulatory agency of the United States Department of Commerce. This Institute develops technology, metrics, and standards to drive innovation and [...]
OS Fingerprinting
If a hacker can determine what type of operating system a targeted computer is running, he or she can work to exploit the vulnerabilities present in that operating system. OS Fingerprinting is used by security professionals and hackers for mapping remote networks and determining which vulnerabilities might be present to [...]
Buffer Overflow Attack
Buffers are memory storage regions that temporarily hold data while it is being transferred from one location to another. These buffers typically live in RAM memory. Most modern hard drives take advantage of buffering to efficiently access data. Buffer is also widely used in online video streaming and buffers are [...]
Macro Virus
What’s a macro? It’s a small program that runs within a bigger program to automate a task (usually a complex or time-consuming task) on a user’s behalf. Macros are written in a programming language designed to work within their broader environment. So, for example, macros for Microsoft Office are currently [...]
What’s DLP?
Data loss refers to an event in which important data is lost to the enterprise, such as in a ransomware attack. Data loss prevention (DLP) focuses on preventing illicit transfer of data outside organizational boundaries. Data loss prevention is a set of tools and processes used to ensure that sensitive [...]
Dark Web
The dark web is a part of the internet (or a small part of the deep web) that isn't indexed by search engines. The dark web contains a large amount of illegal and criminal content (from various aspects). Online marketplaces for drugs, exchanges for stolen data, and other illegal activities [...]
Microsoft Azure
Microsoft Azure is a cloud computing service created by Microsoft for building, testing, deploying, and managing applications and services through Microsoft-managed data centers. Of course, this platform isn't limited to Windows OS and even we can run Linux virtual machines on Azure. Microsoft Azure is an ever-expanding set of cloud [...]
Amazon VPC
Amazon Virtual Private Cloud (VPC) is a commercial cloud computing service that provides a virtual private cloud, by provisioning a logically isolated section of Amazon Web Services (AWS) Cloud. This service enables customer to launches AWS resources into a virtual network that he/she/it has defined. So, a customer has complete [...]
NetFlow
NetFlow is a feature that was introduced on Cisco routers around 1996 that provides the ability to collect IP network traffic as it enters or exits an interface. For example, NetFlow captures the timestamp of a flow’s first and last packets (and hence its duration), the total number of bytes [...]
Measuring Network Performance Tools
In this post, we'll take a look at measuring network performance to help you understand the different aspects of network performance. Network performance measurement is done by examining the values of several important factors. These factors include: Bandwidth and Throughput Delay Packet loss TTL Jitter Interference Network performance measurement is [...]
ITIL Framework
The IT Infrastructure Library (ITIL) is a library of volumes describing a framework of best practices for delivering IT services. ITIL’s systematic approach to IT service management can help businesses manage risk, strengthen customer relations, establish cost-effective practices, and build a stable IT environment that allows for growth, scale and [...]
Rapid7 Products
Rapid7 Nexpose is a vulnerability scanner which aims to support the entire vulnerability management lifecycle, including discovery, detection, verification, risk classification, impact analysis, reporting and mitigation. RAPID7 plays a very important and effective role in the penetration testing, and most pentesters use RAPID7. This paragraph is abbreviated from www.rapid7.com The [...]
Metasploit Framework
A kind of penetration testing aid is the Metasploit Project. This open-source framework allows testing via command line alterations or GUI. The Metasploit Framework is a Ruby-based, modular penetration testing platform that enables a pentester (hacker) to writes, tests, and executes exploit code. In other words, the Metasploit framework is a [...]
Zero-day Vulnerabilities and Zero-day Exploits
Zero-day is a flaw in software, hardware or firmware that it has the potential to be exploited by cybercriminals. In other words, zero-day is a vulnerability in a system or device that has been disclosed but is not yet patched. A zero day exploit is a cyber-attack that occurs on [...]
Penetration Testing
A penetration test (pen test or pentest and or ethical hacking) is a simulated cyber-attack against a computer system to check for exploitable vulnerabilities. You should not be confused it with a vulnerability assessment. Source: en.wikipedia.org In fact, this test simulates a real-world attack to determine how any defenses will [...]
ManageEngine ADAudit
In this post, we'll take a look at ManageEngine ADAudit to help you understand the different aspects of this network product. You can use ManageEngine ADAudit to ensure critical resources in the network like the Domain Controllers are audited, monitored and reported with the entire information on AD objects (like Users, [...]
Broadcast Storm
A broadcast storm is also known as a network storm. It is an abnormally high number of broadcast packets within a short period of time. The broadcast storm is one of the major deficiencies in computer network systems and it can shut down entire network in seconds. When different nodes [...]
Wireshark
Wireshark is a network packet analyzer. This software one of the best packet analyzers available today and is available for free, and it is open source. This software, formerly known as Ethereal but the project was renamed Wireshark in May 2006 due to trademark issues. Sources: wireshark.org and en.wikipedia.org Wireshark [...]
SSL and TLS
In this post, we'll take a look at SSL protocol and TLS protocol to help you understand the different aspects of these protocols. One of the most important topics in Cyber-security course is web secure. What’s SSL? SSL (Secure Sockets Layer) is a protocol for establishing authenticated and [...]
RADIUS
Remote Authentication Dial-In User Service (RADIUS) is a networking protocol, operating on ports UDP 1645 and UDP 1812 that provides centralized AAA (Authentication, Authorization, and Accounting) management for users who connect and use a NAS (network access server such as VPN concentrator, router, switch). This protocol is a client/server protocol [...]
Wireless Security Protocols
Wireless security is the prevention of unauthorized access or damage to computers or data using wireless networks, which include Wi-Fi networks. In this post, we'll take a look at wireless security protocols to help you understand the different aspects of these protocols. Source: en.wikipedia.org There are several types of wireless [...]
pfSense Firewall
We have already published posts about firewalls and also hardware firewalls. In this post, we'll take a look at pfsense firewalls to help you understand the different aspects of pfsense firewalls. pfSense is an open source firewall/router computer software distribution based on FreeBSD. This firewall developed by Rubicon Communications, LLC [...]
Windows Task Manager Window
Monitoring system resources is a necessary part of troubleshooting. Resources include memory, mass storage, network access, processor power, and so on. Computer hardware and software resources must be managed. Proper management is not possible without resources monitoring. In this post, we'll take a look at resources monitoring and also task [...]
Windows Task Manager’s Processes
The subject of this post is to examine the processes in the process tab in the windows task manager in Microsoft windows (Windows workstation family and windows server family). There are many processes, and as a result, we will discuss the most common ones. The Processes tab (in windows task [...]
What’s Cryptojacking?
Cryptojacking is an online threat that hides on a computer or mobile device and uses the machine’s resources to “mine” forms of online money known as cryptocurrencies. Cryptojacking also called malicious cryptomining. In fact, the core idea behind cryptojacking is that hackers use business and personal computer and device resources [...]
SonicWall Firewalls
We have already published posts about firewalls and also hardware firewalls. In this post, we'll take a look at sonicwall firewalls to help you understand the different aspects of sonicwall firewalls. SonicWall next-generation firewalls (NGFW) provide the security, control and visibility you need to maintain an effective cybersecurity posture. SonicWall [...]
Robocallers
In this post, we'll take a look at Robocallers to help you understand the all different aspects of robocallers. what's robocall? A robocall is an automated phone call that uses a computerized autodialer to deliver a pre-recorded message, as if from a robot. Some robocalls use personalized audio messages to [...]
Cryptolocker Attack
The CryptoLocker ransomware attack was a cyberattack using the CryptoLocker ransomware that occurred from 5 September 2013 to late May 2014. It is believed that the operators of CryptoLocker successfully extorted a total of around $3 million from victims of the trojan. It propagated via infected email attachments, and via [...]
Blackmail
Blackmail is an act of coercion using the threat of revealing or publicizing either substantially true or false information about a person or people unless certain demands are met. Blackmail is characterized as a crime and committing black mail can carry significant criminal and civil consequences. In this post, we'll [...]
Microsoft Windows Event Viewer
These days, one of the most important aspects of cyber security is network monitoring. We have already published a detailed post on the importance and how to monitor the network. We suggest you read it. Event Viewer is a component of Microsoft's windows operating system (Server family and Workstation family) [...]
Datadog
These days, one of the most important aspects of cyber security is network monitoring. We have already published a detailed post on the importance and how to monitor the network. We suggest you read it. In this post, we'll take a look at Datadog Network performance monitor to help you [...]
PRTG
PRTG Network Monitor is an agentless network monitoring software. This network monitor tool consists of two main system parts: Core server and Probe. ------------------------------------------------------------------------------------------------------------------------------------------------- These days, one of the most important aspects of cyber security is network monitoring. We have already published a detailed post on the importance and how [...]
Solarwinds Network Performance Monitor
In this post, we have explained why we should have network monitoring software in our network, and in this post, you have learned how these software work. Now we are going to examine one of the most popular network monitoring software: Solarwinds Network Performance Monitor. SolarWinds is one of the [...]
GLBA Compliance
GLBA provides limited privacy protections against the sale of your private financial information. Additionally, the GLBA codifies protections against pretexting, the practice of obtaining personal information through false pretenses. The primary concern of GLBA is to ensure the confidentiality of customers' personally identifiable information (PII) and financial information by following [...]
Free Port Scanner Tools
First of all, we recommend that you read our other post entitled "TCP/UDP Ports". But, what are free port scanner tools? A port scan learns which ports on a router or firewall are open, and can use this information to find a computer system’s potential weaknesses. A port-scanner tool asks [...]
Network Monitoring
Monitoring is one of the key components of network security. A network monitoring system (NMS) monitors the network for problems caused by overloaded or crashed servers, network connections or other devices. Network monitoring is a critical IT process where all networking components like routers, switches, firewalls, servers, and VMs are monitored [...]
TCP/UDP Ports
This post is dedicated to TCP/UDP ports. But what's port? In computer networking, a port is a communication endpoint. A computer port is a type of electronic, software (or programming) related docking point through which information flows from a program on your computer or to your computer from the Internet [...]
Authentication Methods
Authentication is the process of verifying the identity of a person or device. In fact, Authentication technology provides access control for systems by checking to see if a user's credentials match the credentials in a database of authorized users or in a data authentication server. The authentication process always runs [...]
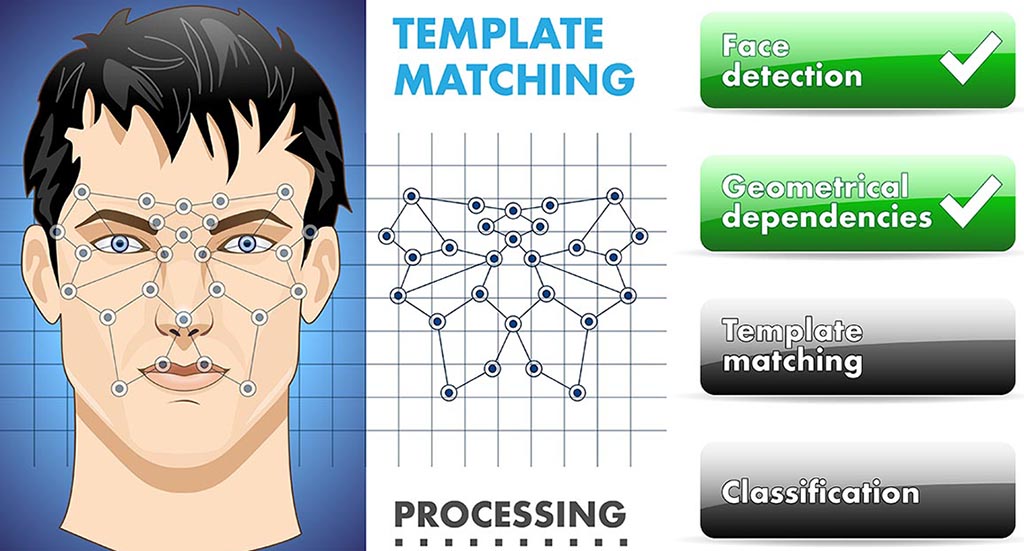
Biometric Authentication Methods
In recent years, issues such as Multi-Factor Authentication (MFA) and Biometric Authentication have become more common due to problems in traditional authentication methods. In fact, biometric methods can be considered a subset of MFA. In this post, we take a look at the most common methods used in biometric authentication. [...]
HIPAA Compliance
The Health Insurance Portability And Accountability Act (HIPAA) a legislation which provides security provisions and data privacy, in order to keep patients’ medical information safe. The law has emerged into greater prominence in recent years with the proliferation of health data breaches caused by cyberattacks and ransomware attacks on health [...]
E-mail Encryption
E-mail encryption is one of the most important aspects of security in organizational networks, personal use, and the Internet. By default, email messages are not secure. They are sent across the Internet in plain text. Hackers who gain unauthorized access to an email account can access attachments, content, and even [...]
Securely Transfer Files
We, as individuals or organizations, often need to securely transfer files over the Internet to another person or organization on the Internet. In this post, we will try to get acquainted with the common solutions for this purpose and examine these file transfer methods from a security point of view. [...]
What’s GDPR?
General Data Protection Regulation (GDPR) is a regulation that requires businesses to protect the personal data and privacy of EU citizens for transactions that occur within EU member states. This regulation aims to simplify the regulatory environment for business so both citizens and businesses in the European Union can fully [...]
Data Encryption
Data encryption translates data into another form, or code, so that only people with access to a decryption key or password can read it. Today, encryption is widely used on the internal networks and internet to ensure the sanctity of user information (such as payment data or personal information) that's sent [...]
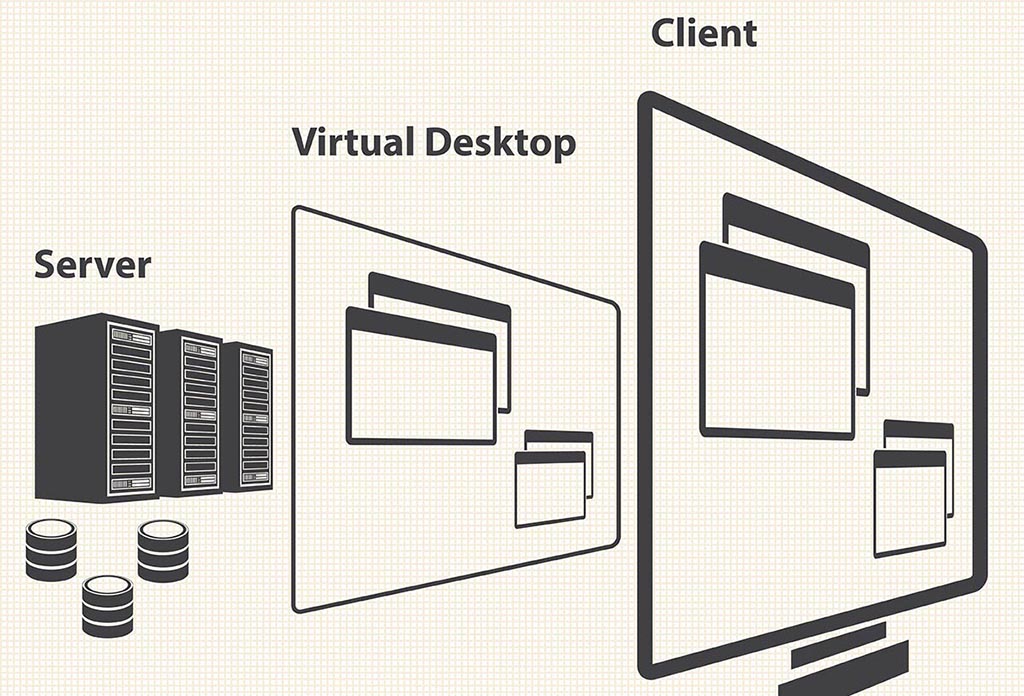
What’s VDI?
Virtual desktop infrastructure (VDI) is defined as the hosting of desktop environments on a central server. In fact, VDI is a desktop virtualization technology wherein a desktop operating system (OS) - typically Microsoft Windows - runs and is managed in an on-premises or cloud data center. The virtual desktop image [...]
IPS and IDS
Intrusion detection is the process of monitoring the events occurring in network and analyzing them for signs of possible incidents, violations, or imminent threats to security policies. These security measures are available as intrusion detection systems (IDS) and intrusion prevention systems (IPS). At result, IDS and IPS are both parts [...]
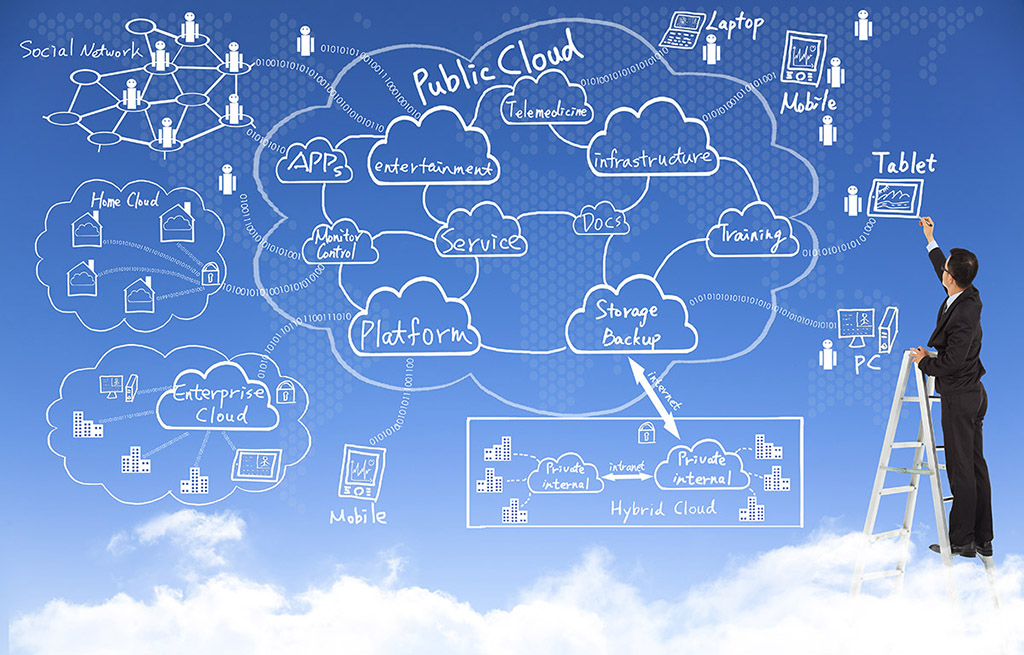
All Things About Public Cloud Services
First of all, we need to know a little bit about the concept of "public cloud services" or "as s service". The term "cloud services" refers to a wide range of services delivered on demand to companies and customers over the internet and in fact, it refers to a broad category [...]
Offsite Backup
No matter how efficient a computer system appears to be, there is always the possibility of a malfunction wiping out valuable data. For this reason, many companies have set up backup systems, designed to recover lost data. It is very important that an organization have at least two backup. a [...]
Step by Step Malware Removal
This post is dedicated to malware removal. In this post we are going to tell you how you can find out that your computer has been the victim of malware. Then learn what to do if malware is on your computer. Finally, we have some important security solutions for you [...]
Cloud Backup Solutions
In this post, we'll talk a little bit about cloud backup solution. About how cloud backup works? How to restore data from cloud backup? What methods can cloud backup be used for? What are the benefits of using cloud backup? Also we'll talk a little bit about cloud backup solutions. [...]
How To Document BCP?
It is a good idea to read this post first about resuscitation as well as job continuity. As you can see, the process of business continuity involves several steps. In the fifth stage, called "BCP Implementation", one of important things that needs to be done is to document the business [...]
Hardware Firewalls
Previously; We wrote an article as “All Things about Firewalls" earlier. Now, we want to discuss more about hardware firewalls. A hardware firewall is a physical device similar to a server that filters traffic to a computer. Hardware firewall has processor, memory, and sophisticated software, powerful networking components (hardware and [...]
What’s PCI DSS?
The Payment Card Industry Data Security Standard (PCI DSS) is a set of security standards for organizations that handle branded credit cards. The PCI DSS applies to ANY organization that accepts, transmits or stores any cardholder data. The PCI Standard is administered by the Payment Card Industry Security Standards Council. This [...]
Server virtualization
Computer network administrators usually dedicate each server to a specific application or task. In most cases each application / task needs its own dedicated machine. There are a couple of problems with this approach, though. One is that it doesn't take advantage of modern server computers' processing power. Many of these [...]
Microsoft 365
First of all, it should be noted that in preparing this article, we have used a lot of contents from the microsoft.com website. Sometimes we have copied and pasted the contents, in most cases we have summarized the contents, and sometimes, of course, we have written our own interpretation of [...]
Password Managers
Why is it recommended to use password managers? These days, every new website and application we sign up for is another password we have to remember. In fact, the number of passwords we need to remember is so high that we may forget all or part of them. If we [...]
Veeam Backup & Replication
First of all, it should be noted that in preparing this post, we have used a lot of contents from the veeam website help center. Sometimes we have copied and pasted the article, in most cases we have summarized the article, and sometimes, of course, we have written our own [...]
Secure Remote Access
Remote access is the ability to access your computer from a remote location. In fact, Remote access is simply the ability to access a computer or network, at home or in an office, from a remote location. Remote access connection allows users to access a network or computer remotely via [...]
Social Engineering Attacks
Social engineering attacks are more prevalent than most people think. The reason for their prevalence is that they are relatively easy to implement. Social engineering is the term used for a broad range of malicious activities accomplished through human interactions. People are weakest link in the security chain, and in [...]
Information Security Concepts
This post provides some information on the concept of security, the concept of security in the network, the concept of security threats and their types. Security Risk A computer security risk is the potential for loss, damage or destruction of an asset as a result of a threat [...]
Phishing Attacks
Phishing is a type of social engineering attack often used to steal user data, including login credentials and credit card numbers. There is another definition for this attack. We can say Phishing is the fraudulent use of electronic communications to deceive and take advantage of users. Phishing attacks attempt to gain sensitive, [...]
All Things About Firewall
A network firewall is a network security device that monitors incoming and outgoing network traffic. Firewalls are a first line of defense in network security. Firewall purpose is to establish a barrier between your internal network and incoming traffic from external sources (such as the internet) in order to block [...]
Malware and its variants
In this article, we want to introduce you to different types of malware. First we need to see what the word malware itself means. Malware is actually abbreviated to "malicious software", and it's actually a name used to refer to all viruses, all worms, all spyware, all Trojans, and any malicious [...]
Disaster Recovery and Business Continuity
How an organization responds to a cyber security incident or any other event that causes the loss of operations or data. We have provided detailed training on these two topics in the CISSP Training Course. In recent years, Disaster Recovery, and business continuity have more important role in enterprise computing [...]
Cyber Security
Cyber security is the practice of protecting systems, networks, and programs from digital attacks. It's also known as information technology security or electronic information security. Cyber-attacks are often aimed at accessing, changing, or destroying sensitive information. Final goal of these attacks is extorting money from users, or interrupting normal business [...]
Confidence Attacks and Romance Fraud Attacks
These days, confidence attacks and romance fraud attacks are very common. An attacker deceives a victim into believing the attacker and the victim have a trust relationship, whether family, friendly or romantic. So, victim will trust to attacker. At this time, the attacker asks the victim to send money to the [...]
Pharming Attacks
Pharming is a type of cyber crime. It is very similar to phishing attacks. The Pharming attacks to name resolution process. However, There is a DNS server in each network. In fact, each computer has its local DNS service. A pharming attack uses two way for attack to this process: [...]