In recent years, issues such as Multi-Factor Authentication (MFA) and Biometric Authentication have become more common due to problems in traditional authentication methods. In fact, biometric methods can be considered a subset of MFA. In this post, we take a look at the most common methods used in biometric authentication.
There are a number of advantages to this technology:
- Biometric identification can provide extremely accurate, secured access to information.
- Current methods like password verification have many problems.
- Automated biometric identification can be done rapidly and with a minimum of training.
- Person’s identity can be verified without resort to documents that may be stolen, lost or altered.
Face Recognition
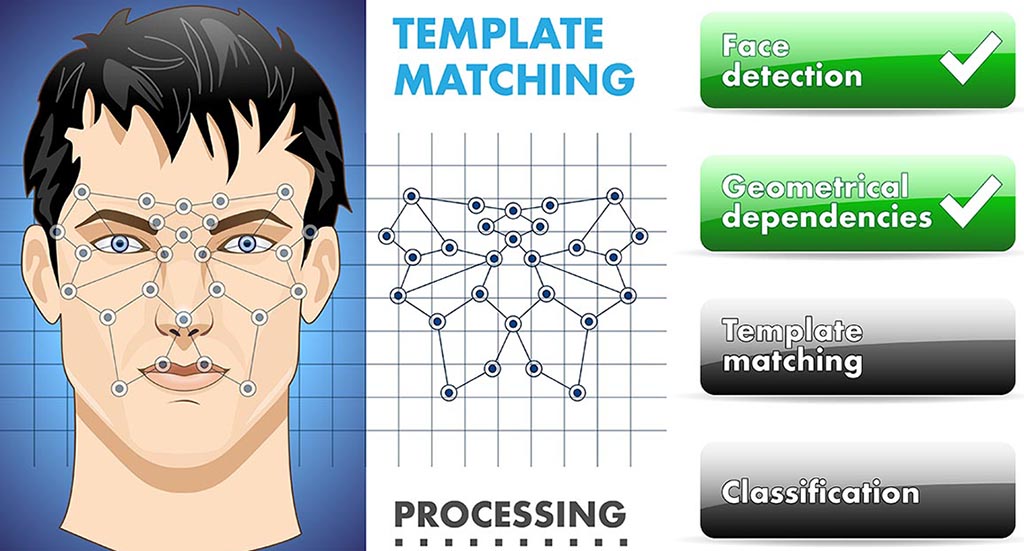
Face recognition is a method of identifying or verifying the identity of an individual using their face. Face recognition systems can be used to identify people in photos, video, or in real-time. Face recognition is one of the most flexible, working even when the subject is unaware of being scanned.
Face recognition systems use computer algorithms to pick out specific, distinctive details about a person’s face. The data about a particular face is often called a face template
First off, the computer has to learn what a face is. This can be done by training an algorithm, usually a deep neural network, on a vast number of photos that have faces in known positions. Each time the algorithm is presented with an image, it estimates where the face is. This is the face detection step.
Next up is the recognition part. Some algorithms explicitly map the face. These algorithms measure the distance between the eyes, width of the nose, position of cheekbones, jaw line, chin and so forth. These numerical quantities are then combined in a single code that uniquely identifies each person.
Here are some examples of common uses for facial recognition technology:
- Mobile phone manufacturers for consumer security.
- Social media to tag individuals in photographs.
- Business security, as businesses can use facial recognition for entry to their buildings.
- Governments at airports to identify individuals who may overstay their visas.
- Law enforcement through collecting mugshots to compare against databases.
- Marketing, where marketers can use facial recognition to determine age, gender and ethnicity to target specific audiences.
Read more about face recognition here.
Source: thalesgroup.com and eff.org
Fingerprint Identification
Fingerprint identification is one of the most well-known and publicized biometric methods. Because of their uniqueness and consistency over time. Fingerprints remain constant throughout life. In over 140 years of fingerprint comparison worldwide, no two fingerprints have ever been found to be alike, not even those of identical twins.
Fingerprint identification is popular because of the inherent ease in acquisition, the numerous sources (10 fingers) available for collection, and their established use and collections by law enforcement and immigration. Fingerprints can be recorded on a standard fingerprint card or can be recorded digitally and transmitted electronically for comparison. At result, a variety of sensor types — optical, capacitive, ultrasound, and thermal — are used for collecting the digital image of a fingerprint surface. Optical sensors take an image of the fingerprint, and are the most common sensor today.
Fingerprint recognition allows a person to be verified or identified through the analysis and comparison of his or her finger dermal ridges. Of course, fingerprint identification might not work in industrial applications since it requires clean hands.
A fingerprint usually appears as a series of dark lines that represent the high, peaking portion of the friction ridge skin, while the valley between these ridges appears as white space and are the low, shallow portion of the friction ridge skin. Fingerprint identification is based primarily on the minutiae, or the location and direction of the ridge endings and bifurcations along a ridge path.
Read more about fingerprint identification here.
Sources:
Hand Geometry Biometrics
Hand geometry readers work in harsh environments, do not require clean conditions (Unlike Fingerprint Detectors), and forms a very small dataset. It is not regarded as an intrusive kind of test. At result, Hand geometry biometric is often the authentication method of choice in industrial environments.
Hand geometry systems use a camera to capture a silhouette image of the hand. The hand of the subject is placed on the plate, palm down, and guided by five pegs that sense when the hand is in place. Hand geometry is based on the palm and fingers structure, including width of the fingers in different places, length of the fingers, thickness of the palm area, etc.
The enrollment process of a hand geometry system typically requires the capture of three sequential images of the hand. The resulting data capture by a Charge-Coupled Device (CCD) camera of the top view of the hand including example distance measurements.
Advantages of Hand Geometry Biometrics:
- Simple, relatively easy to use and inexpensive
- Environmental factors is not an issue
- Usually considered less intrusive than fingerprints, retinal, etc
Disadvantages of Hand Geometry Biometrics:
- The hand geometry is not unique and cannot be used in identification systems.
- Jewelry, limited dexterity and etc may pose a challenge in extracting the hand geometry information.
- The data size of hand geometry biometrics is large and is not ideal for using it in embedded systems.
Learn more about hand geometry biometrics here.
Source: 360biometrics.com and technovelgy.com and biometricupdate.com
Retina Scan
There is no known way to replicate a retina. As far as anyone knows, the pattern of the blood vessels at the back of the eye is unique and stays the same for a lifetime. The blood vessels within the retina absorb light more readily than the surrounding tissue and are easily identified with appropriate lighting. However, it requires about 15 seconds of careful concentration to take a good scan.
Retinal imaging takes a digital picture of the back of eye (unique patterns of a person’s retina). It shows the retina (where light and images hit), the optic disk (a spot on the retina that holds the optic nerve, which sends information to the brain), and blood vessels.
Once the scanner device captures a retinal image, specialized software compiles the unique features of the network of retinal blood vessels into a template. Retinal scan algorithms require a high-quality image and will not let a user enroll or verify until the system is able to capture an image of sufficient quality.
Retinal scan is a highly dependable technology because it is highly accurate and difficult to spoof, in terms of identification. The technology, however, has notable disadvantages including difficult image acquisition and limited user applications. Often enrollment in a retinal scan biometric system is lengthy due to requirement of multiple image capture, which can cause user discomfort.
Retinal scan technology has robust matching capabilities and is typically configured to do one-to-many identification against a database of users. While the algorithms themselves are robust, it can be a difficult process to provide sufficient data for matching to take place. As with fingerprints and iris patterns, genetic factors do not determine the exact pattern of blood vessels in the retina. This allows retinal scan technology to differentiate between identical twins and provide robust identification. Certain eye-related medical conditions and diseases, such as cataracts and glaucoma, can render a person unable to use retina-scan technology, as the blood vessels can be obscured.
In recently years, retina scan remains a standard in military and government installations.
Read more about retina scan here.
Source:
Iris Scan
Like a retina scan, an iris scan also provides unique biometric data that is very difficult to duplicate and remains the same for a lifetime. Iris scanning biometrics measure the unique patterns in the colored circle of eye to verify and authenticate identity.
Iris recognition or iris scanning is the process of using visible and near-infrared light to take a high-contrast photograph of a person’s iris. It is a form of biometric technology in the same category as face recognition and fingerprinting.
Iris scanning raises significant civil liberties and privacy concerns. It may be possible to scan irises from a distance or even on the move, which means that data could be collected surreptitiously, without individuals’ knowledge. Even some solutions requiring only a glance from a person.
We’re already seeing iris scanning adopted in several scenarios:
- Smartphones
- Banking
- Borders
Learn more about iris scan here.
Source: findbiometrics.com and eff.org
———————————
Sources: