Syslog stands for “System Logging Protocol,” Syslog used for system management and security auditing as well as general informational, analysis, and debugging messages. Syslog is a way for network devices to send event messages to a logging server. This protocol can be used to log different types of events. For example, a router might send messages about users logging on to console sessions. In fact, Syslog is a Message Logging Standard by which almost any device or application can send data about status, events, diagnostics, and more. Using the syslog protocol is certainly one of the most useful steps in network monitoring.
Syslog is now standardized by the IETF in RFC 5424 (since 2009), but has been around since the 80’s served as the de facto standard for logging without any authoritative published specification.
A wide variety of devices, such as printers, switches, wireless access points, routers, and message receivers across many platforms use the syslog standard and Implementations of syslog exist for many operating systems. It include almost all versions of Linux, UNIX, and MacOS platforms. On Microsoft Windows, Syslog can also be supported through a variety of open source and commercial third-party libraries.
Source: networkmanagementsoftware.com and blog.rapid7.com
How Does Syslog Work?
When operating over a network, syslog uses a client-server architecture where a syslog server listens for and logs messages coming from clients. Forwarding local log messages to a remote log analytics server/service via Syslog has been commonly adopted as a standard industrial logging solution.
Syslog traffic uses port UDP 514 by default. Why UDP Protocol? Because syslog messages are simply just sent regardless if there is a receiver configured on the other end or not. So, if a packet gets lost during transmission, it’s gone! Of course, some network devices will send Syslog data via TCP 1468 to ensure message delivery. Messages are usually text and usually no larger than 1024 bytes.
The Syslog standard defines three different layers:
- Syslog content: information contained in a Syslog event message.
- Syslog application: An application that generates, interprets, routes, and stores the message.
- Syslog transport: A layer that transmits the message via the network.
Source: blog.rapid7.com and pcwdld.com
Syslog Server
Syslog itself relies heavily upon having a Syslog server of some kind to receive, store, and interpret Syslog messages. So, most Syslog servers have a couple of components that make this possible.
Syslog servers come in all manner of shapes and sizes – some are physical appliances meant for exceptionally large-scale environments, while others are smaller software-based services or applications, while still others function as stand-alone VMs added into an environment to do the appropriate monitoring. . Syslog servers should be able to generate alerts, notifications, and alarms in response to select messages.
- A Syslog Listener: A Syslog server needs to receive messages sent over the network. A listener process gathers syslog data sent over UDP port 514 or TCP 1468.
- A Database: A proper Syslog servers will use a database to store syslog data for quick retrieval.
- Management and Filtering Software: It is better that we use a syslog server that both automates part of the work, and makes it easy to filter and view important log messages.
Source: ittsystems.com
Syslog Messages
Syslog messages often include information to help identify basic information about where, when, and why the log was sent. These messages include three part:
- PRI (Priority Value)
- Header
- MSG (Message portion of the Packet)
PRI
The Priority Value is the first part of the Syslog Message, spanning exactly either 3, 4 or 5 characters and bound by Angle Brackets. Priority Values are calculated as follows:
Facility Value * 8 + Severity Value = Priority Value
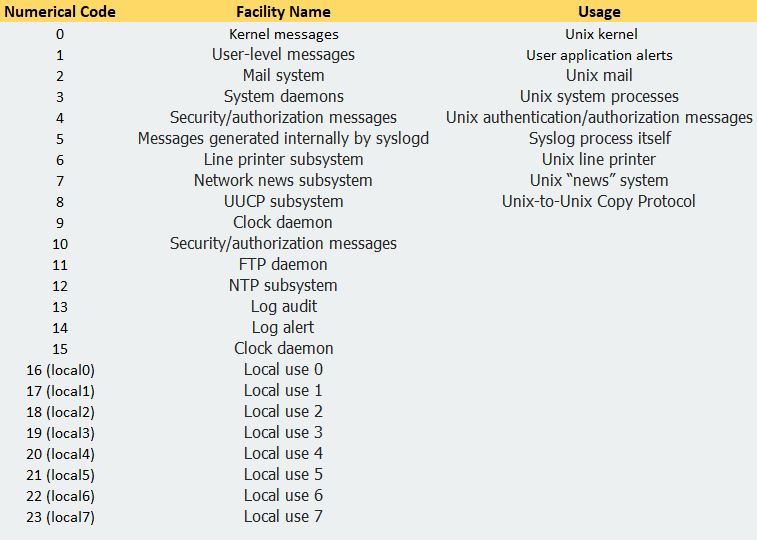
Syslog uses a concept called “facility” to identify the source of a message on any given machine. The server system used the facility code to sort related messages into the same file.
Facility codes are also numerical values, which are listed in the following table. Notice many of them are highly specific to systems that are, in many cases, not commonly used anymore. These are the facility codes defined in RFC 5424. Facility Codes is a component of either an application or operating system that generates a Log/Event Message from the table below:
Syslog messages have a severity level field. It includes a single number between 0 and 7 that indicates how important the message is. A severity of “0” is an emergency, “1” is an alert that needs immediate action, and the scale continues right down to “6” and “7” – informational and debug messages.
A list of Numerical Codes and its corresponding message are highlighted in the table below:
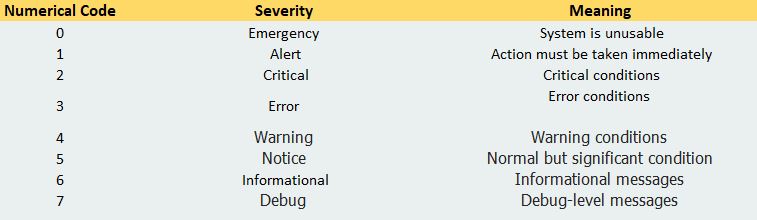
Source: en.wikipedia.org and auvik.com
Header
The header portion of a Syslog packet contains the following information:
- Timestamp: The Combination of the DATE and TIME that the message was initially generated
- Hostname or IP Address of the Network Device
MSG
The MSG will contain information generated by the device with information regarding the log or event.
The MSG contains two fields as well:
- TAG: indicates the Process or Program that has triggered or generated the message
- CONTENT: contains details of the message. The content field should be encoded in a UTF-8 character set and octet values in the traditional ASCII control character range should be avoided
———————————
Sources:
















