We discussed vulnerability scanning in recent blog. Now in this blog we are going to introduce a number of vulnerability scanning tools.
What is Network Vulnerability Scanning?
Among the famous tools in this area are the following:
- SolarWinds MSP
- OpenVAS
- Nikto
- Retina products
- Solarwinds Network Configuration Manager
- Nexpose Community Edition
- ManageEngine Vulnerability Manager Plus
- ImmuniWeb
SolarWinds MSP
Vulnerability scan tools like the multi-layered security solutions available from SolarWinds MSP are very useful.
SolarWinds MSP delivers the only 100% SaaS, fully cloud-based IT service management (ITSM) platform. This solution is include many powerful products, such as Risk Intelligence, Remote Management, Backup & Disaster Recovery, Mail and Service Desk.
This software enables companies and managed service providers for:
- Minimizing the risk of a data breach
- Assigning a dollar value to the risk of each potential breach to provide visibility
- Remaining in constant compliance with HIPAA, PCI DSS, FINRA and any other regulations
- Gaining a more objective and data-driven evaluation
OpenVAS
OpenVAS is an open source vulnerability assessment tool that was originally based on the Nessus network scanning tool. The framework behind OpenVAS is part of Greenbone Networks’ vulnerability management solution from which developments have been contributed to the community. Its capabilities include unauthenticated testing, authenticated testing, various high level and low level Internet, and a powerful internal programming language to implement any type of vulnerability test.
OpenVAS scanner comes with over fifty thousand Network Vulnerability Tests which are updated on a regular basis. Also, OpenVAS can identify anonymous FTP access, ProFTPD security issues, null sessions, and weak authentication.
OpenVAS is available as a virtual appliance on Windows virtual machines or source code on Linux distributions.
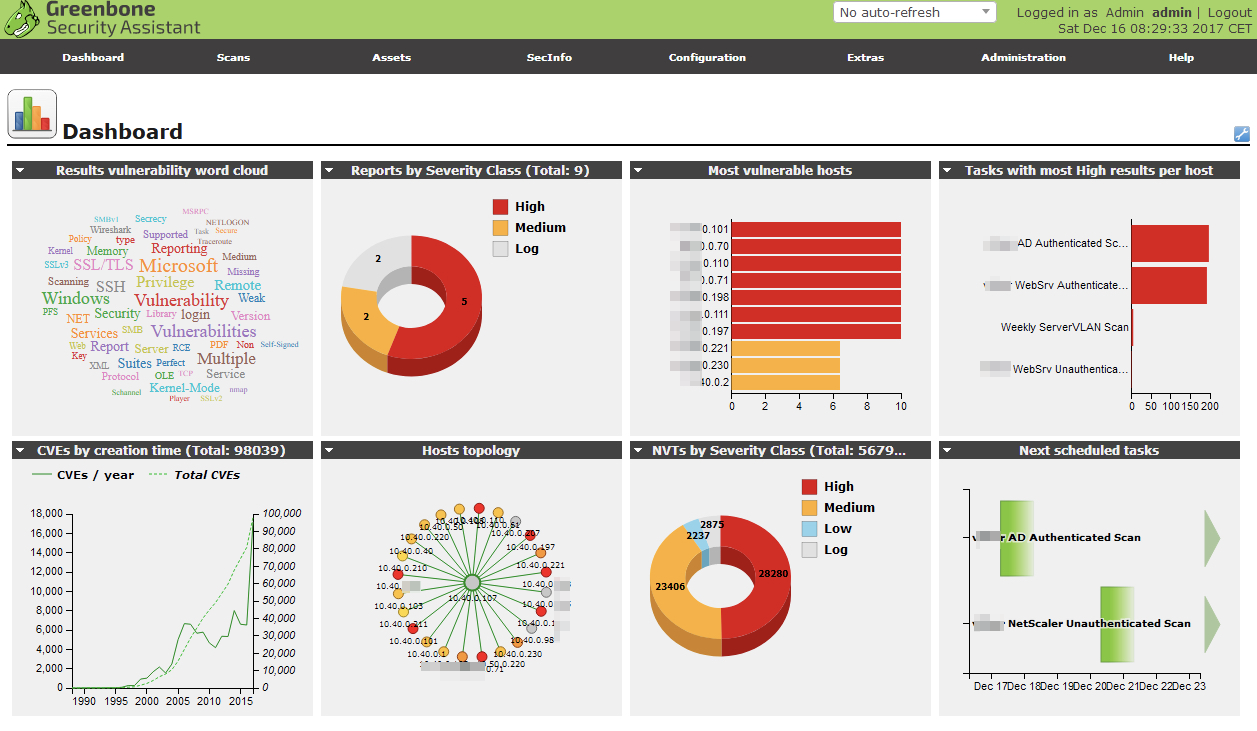
Source: offsec.vchur.dk
OpenVAS has two main components:
- OpenVAS scanner: It is responsible for the actual scanning of target computers
- OpenVAS manager: It controls the scanner, consolidates results, and stores them in a central SQL database along with the system’s configuration.
Nikto
Nikto is a free software command-line vulnerability scanner that scans webservers for dangerous files/CGIs, outdated server software and other problems. Nikto also checks for server configuration items such as the presence of multiple index files and HTTP server options, and will attempt to identify installed web servers and software.
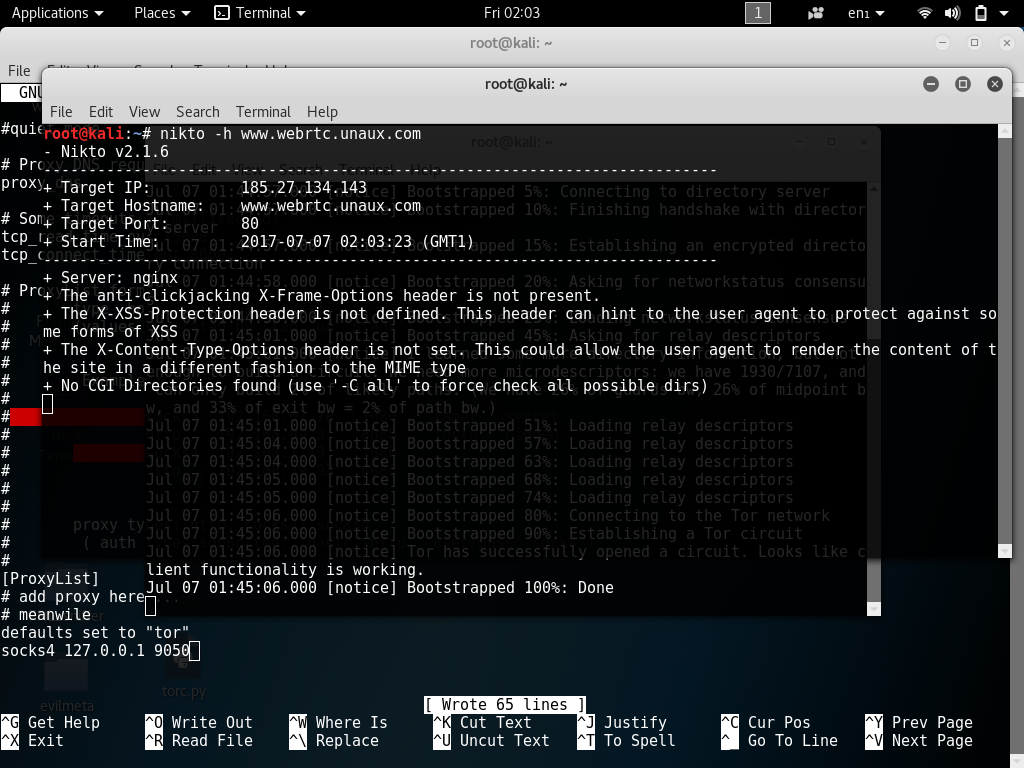
Source: hackingvision.com
Here are some of the major features of Nikto:
- Host authentication with Basic and NTLM
- SSL Support
- Full HTTP proxy support
- Logging to Metasploit
- Save reports in plain text, XML, HTML, NBE or CSV
- Scan multiple ports on a server, or multiple servers
- Identifying installed software via headers, favicons and files
- Thorough documentation
Retina Products
Retina Network Community is the free version of the Retina Network Security Scanner. The tool can perform a free vulnerability assessment of missing patches, zero-day vulnerabilities, and non-secure configurations.
Retina Network Community is automatically updated and covers a wide range of operating systems, devices, applications, and virtual environments.
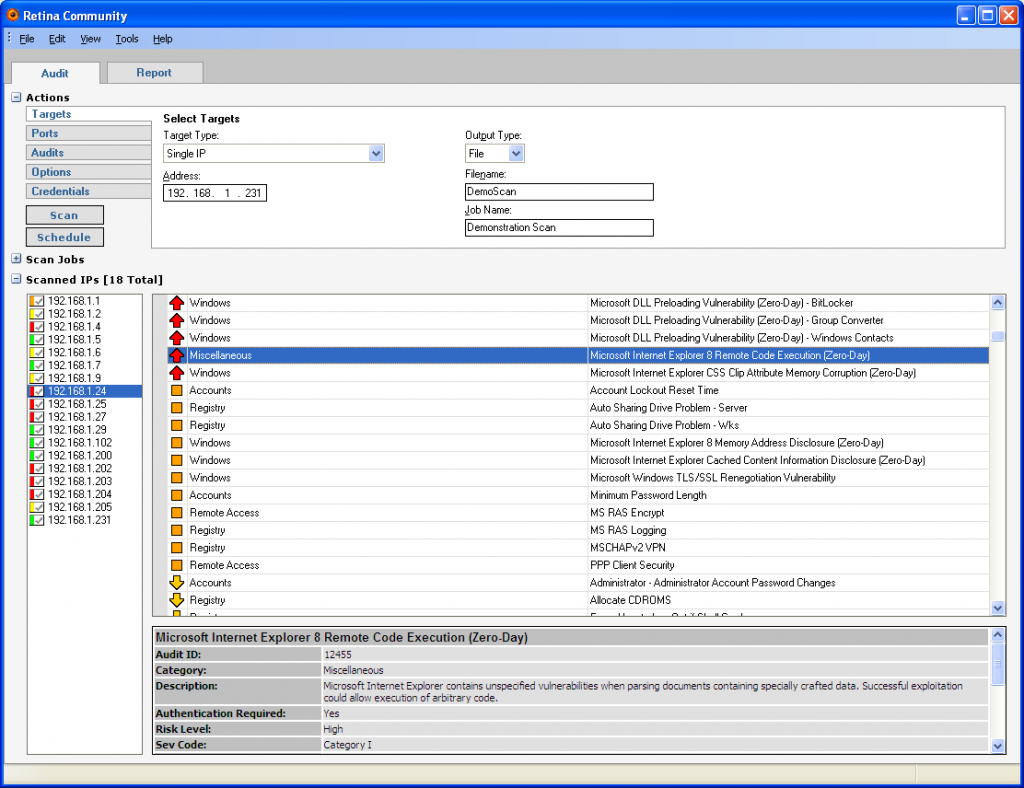
Source: ehacking.net
Retina Network Community fully supports VMware environments and includes online and offline virtual image scanning, virtual application scanning, and integration with vCenter. This tool is limited to scanning 256 IP addresses.
There is another product is retina that is named Retina Network Security Scanner. it is available in Standard and Unlimited editions. Use it for large networks.
Solarwinds Network Configuration Manager
This tool’s primary purpose as a vulnerability scanner is validating network equipment for configurations errors and omissions. With SolarWinds Network Configuration Manager you can look for security vulnerabilities across multi-vendor networks and scan your current network configurations for vulnerabilities.
NCM handles both vulnerability scanning and management for the domain of vulnerabilities arising from the router and switch misconfiguration. NCM is only free during a fully-functional trial of 30 days.
This tool can help you with network compliance with its automated network configuration tools that can deploy standardized configs, detect out-of-process changes, audit configurations, and even correct violations.
Vulnerability management takes place through one view. The user interface allows you to change configurations and identify when changes are taking place within your network.
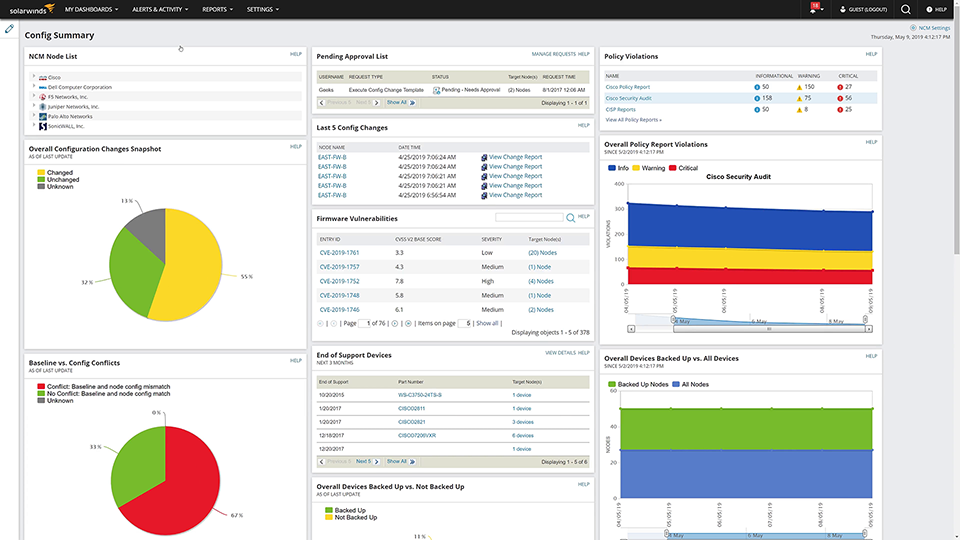
Source: solarwinds.com
To address unauthorized changes including regressions, it provides configuration change monitoring and alerting. It can continuously audit routers and switches for compliance. The software integrates with the National Vulnerability Database and has access to the most current CVE’s to identify vulnerabilities in your Cisco devices. It will work with any Cisco device running ASA, IOS, or Nexus OS. Network Insight is the main feature that helps you to manage vulnerabilities for Cisco ASA and Cisco Nexus.
Overall SolarWinds Network Configuration Manager is highly recommended to companies who want to mix vulnerability scanning with configuration management.
Key Features:
- Spots malicious activity
- Protects device configurations
- Standardizes network setup
- Vulnerability assessment
- Integration with Network Performance Monitor
- Rolls back unauthorized set up changes
Nexpose Community Edition
Nexpose Community Edition is a comprehensive vulnerability scanner by Rapid7, the owners of the Metasploit exploit framework. In fact, Nexpose Community Edition is a limited version of Rapid7’s comprehensive vulnerability scanner. The Community Edition comes with a trial of Rapid7’s web-based console.
Nexpose can run on physical machines running either Windows or Linux. It is also available as a VM appliance.
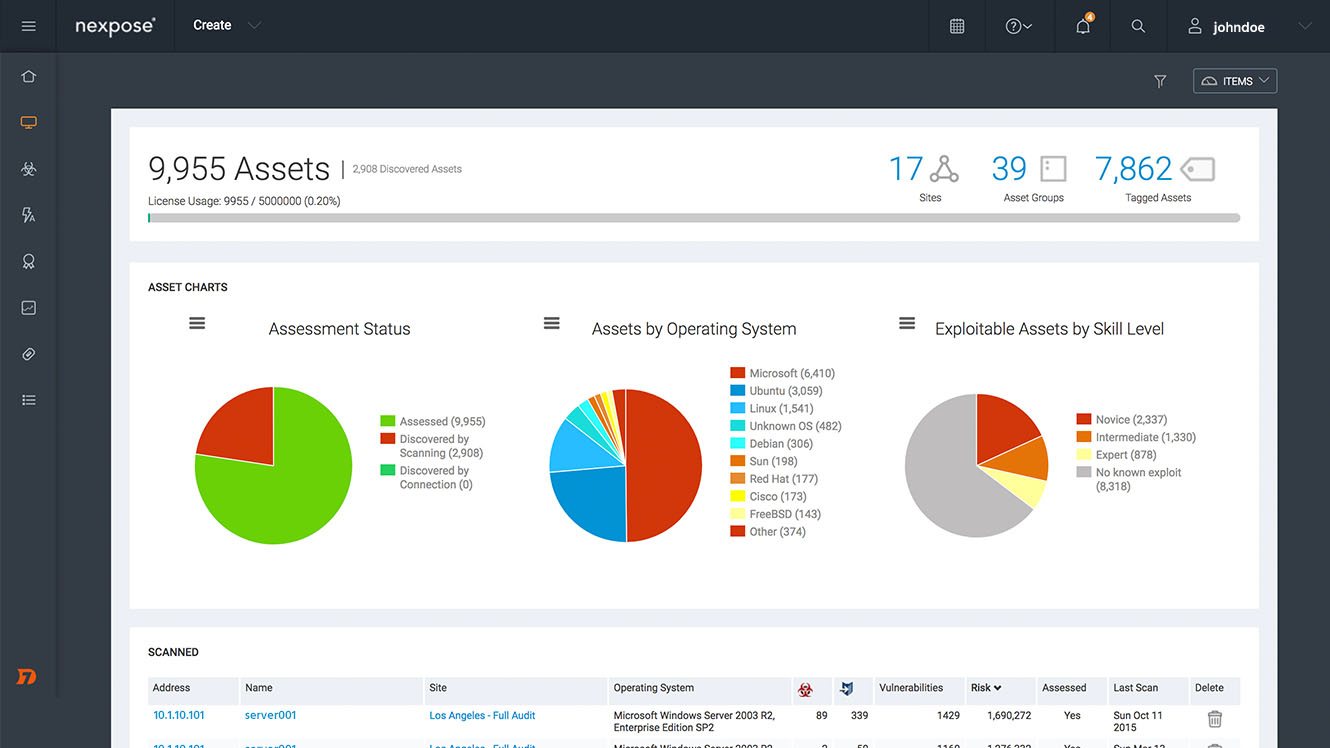
Source: rapid7.com
This product has some limitations: The free version of Nexpose is limited to 32 IP addresses at a time, and you must reapply after a year.
Nexpose uses what it calls Adaptive Security which can automatically detect and assess new devices and new vulnerabilities the moment they access your network. A Discovery Scan identifies all the devices and hosts in your specified address range.
The tool’s Intuitive remediation reports give step-by-step instructions on remediation actions to quickly improve compliance.
You can also set up scheduled scans, enable compliance policies, and track the history of the site’s exposure to vulnerabilities.
ManageEngine Vulnerability Manager Plus
On this website, we have written a lot about ManageEngine products. Now it is time to introduce another product from this well-known manufacturer. Vulnerability Manager Plus is prioritization-focused vulnerability management tool for enterprises offering built-in patch management. ManageEngine Vulnerability Manager Plus include three version: paid versions (Professional and Enterprise), and free version. Free version is suitable for small and middle-sized enterprises and it will protect up to 25 devices.
The advanced technology deployed in the scanner can detect anomalous behavior. This strategy is more effective at identifying zero-day vulnerabilities than conventional rule-based threat database-driven detection systems.
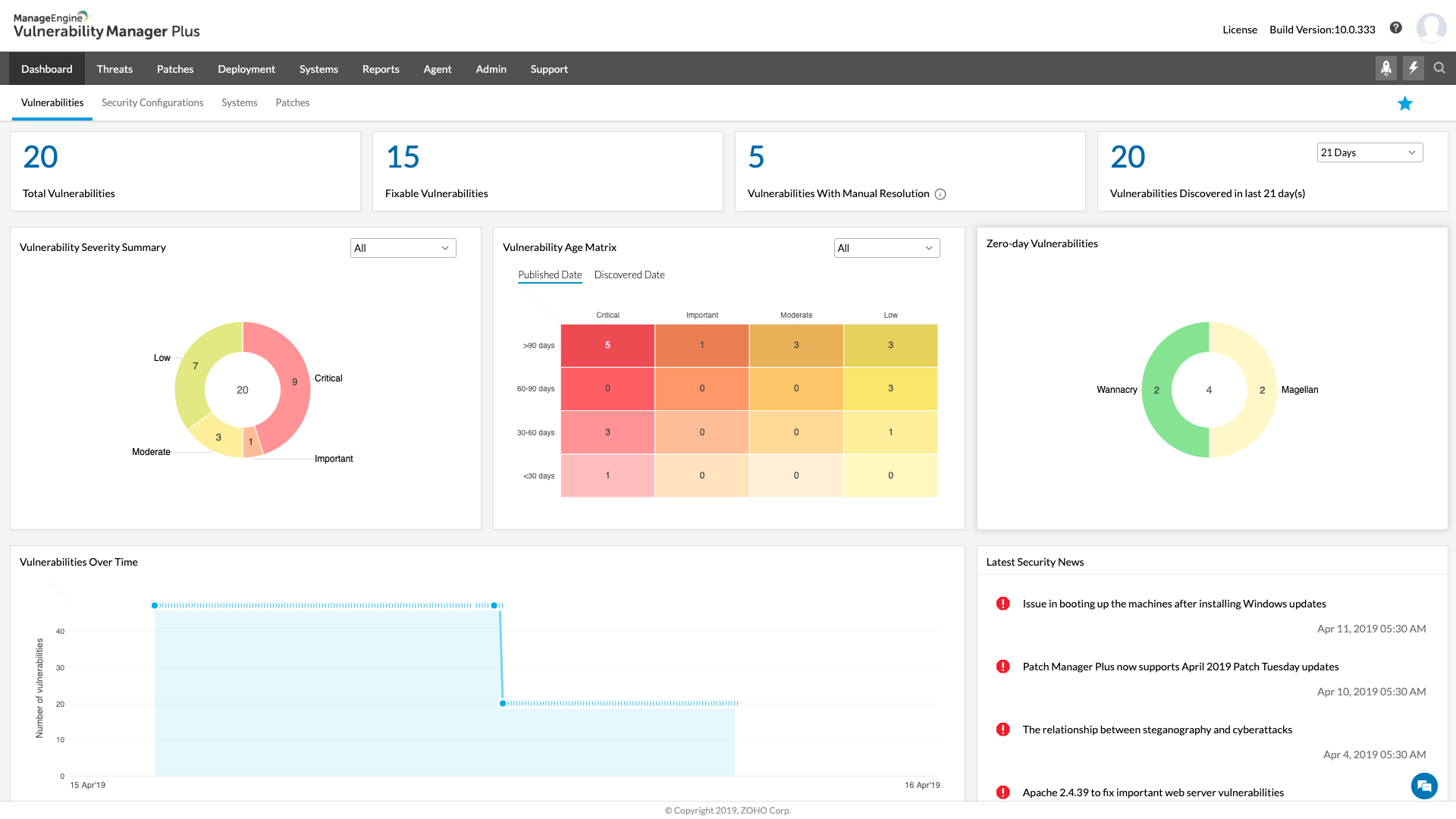
Source: manageengine.com
This tool scans and discovers exposed areas of all your local and remote office endpoints as well as roaming devices. The scan also checks on software versions and lets you automate patch installations. The scanner will identify risky software installed on your equipment and automatically remove unauthorized or unadvised installs.
This tool Leverages attacker-based analytics, and prioritizes areas that are more likely to be exploited by an attacker.
System administrators get special tools in a dashboard that enable them to extend the basic capabilities of the vulnerability manager.
ImmuniWeb
ImmuniWeb is one of the most advanced web-based vulnerability scanners on the market. This is a very sophisticated AI-based system that can be used as a one-time service or contracted in on an SLA for continuous monitoring, consultancy, and advice.
ImuniWeb Discovery applies machine learning techniques to verify any detected weakness and this reduces the incidences of false positive reporting.
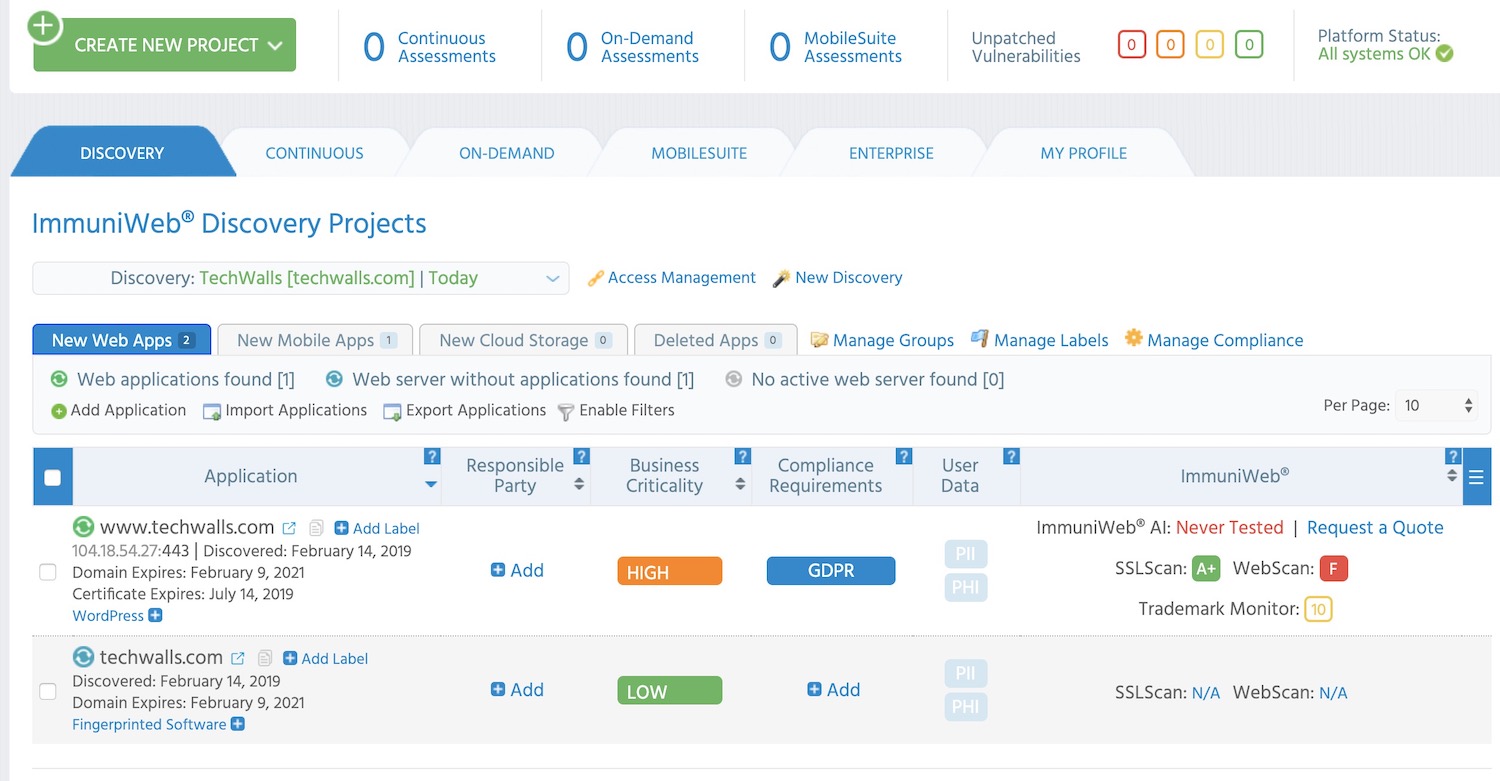
Source: techwalls.com
This tool has a proven track record of identifying security risks like injection, broken authentication, and misconfiguration.
ImmuniWeb specialize in vulnerability scanning and pen testing. The key difference between vulnerability scanning and pen testing is that vulnerability scanning is performed by software automatically and pen testing is a human endeavor.
Key Features:
- Dark Web Monitoring
- Asset Discovery
- Security Monitoring
- Security Ratings
——————————
Sources:
















