The Health Insurance Portability And Accountability Act (HIPAA) compliance a legislation which provides security provisions and data privacy, in order to keep patients’ medical information safe.
The law has emerged into greater prominence in recent years with the proliferation of health data breaches caused by cyberattacks and ransomware attacks on health insurers and providers.

Section 1: About HIPAA Compliance
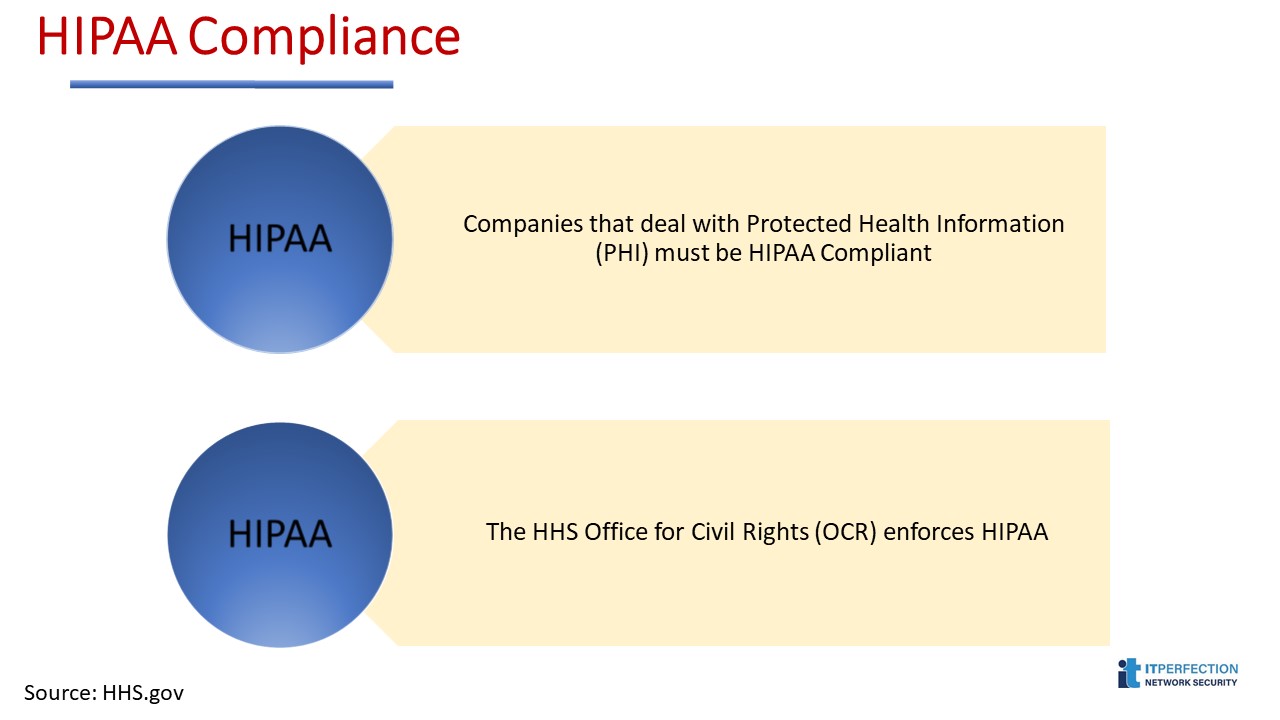
Companies that deal with protected health information (PHI) must have physical, network, and process security measures in place and follow them to ensure HIPAA Compliance.
Other entities, such as subcontractors and any other related business associates must also be in compliance.
Titles
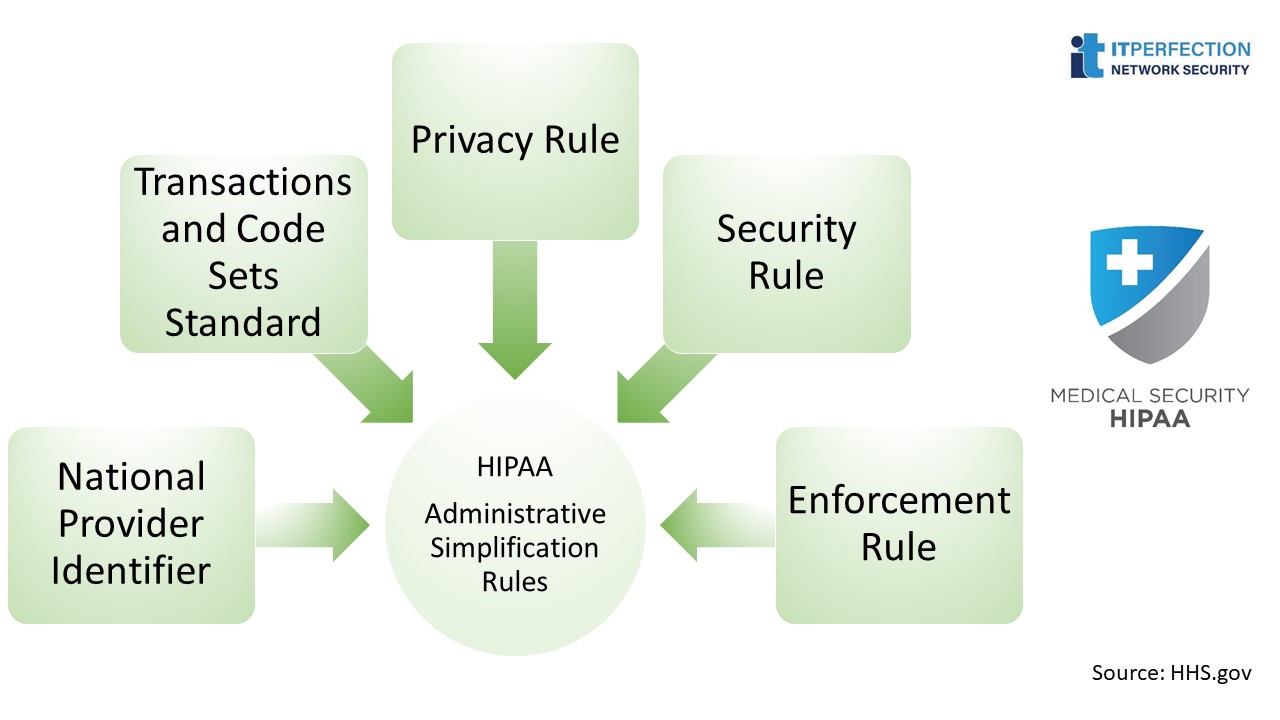
HIPAA is divided into 5 titles, of which title II “Administrative Simplification Rules” is the one related to IT and information security. It title contains the following topics:
- National Provider Identifier Standard
- Transactions and Code Sets Standard
- Privacy Rule
- Security Rule
- Enforcement Rule
National Provider Identifier Standard
Each healthcare entity, including individuals, employers, health plans and healthcare providers, must have a unique 10-digit national provider identifier number, or NPI.

Transactions and Code Sets Standard
This standard orders organizations to follow a standard mechanisms for EDI when processing or submitting insurance claims.

Privacy Rules
Privacy rule requires covered entities and business associates to protect the privacy of any kind of patient health information that can identify an individual, whether it is electronic or not, and gives standards related to Protected Health Information (PHI) uses and disclosures and whether they need patient consent/authorization or not.

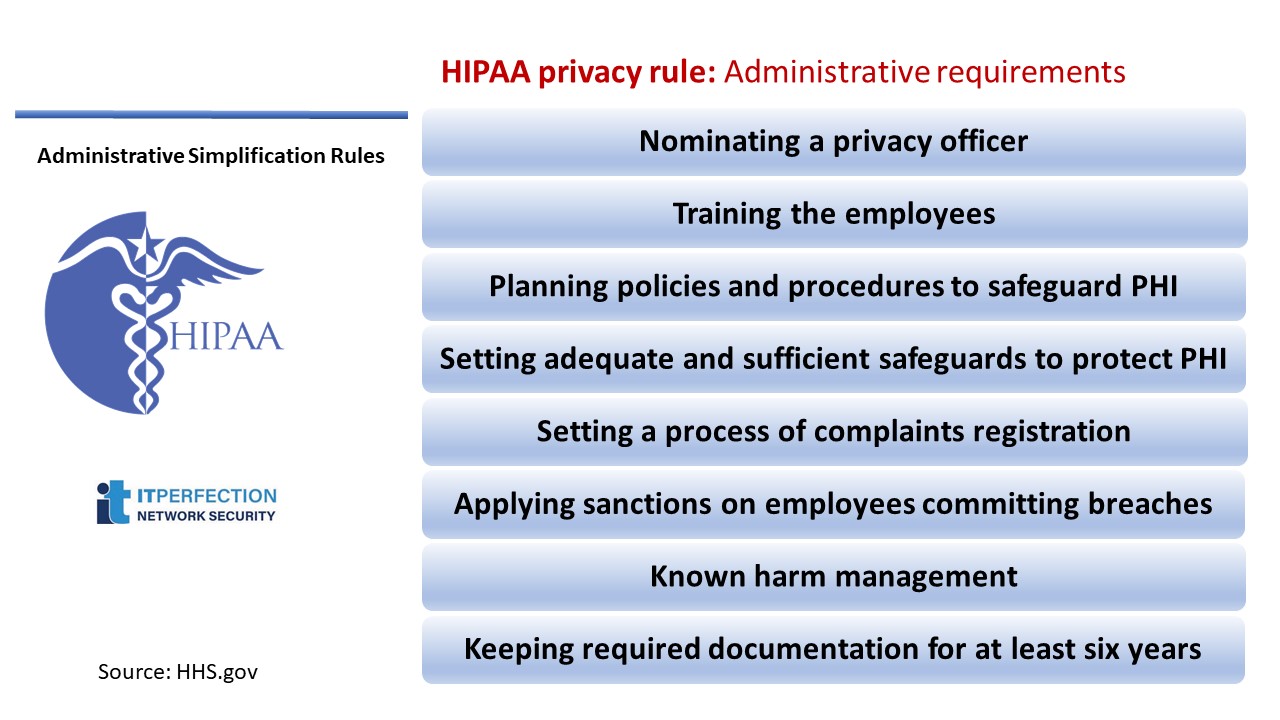
Administrative requirements
The privacy rule covers administrative requirements that are applicable to most of the covered entities.
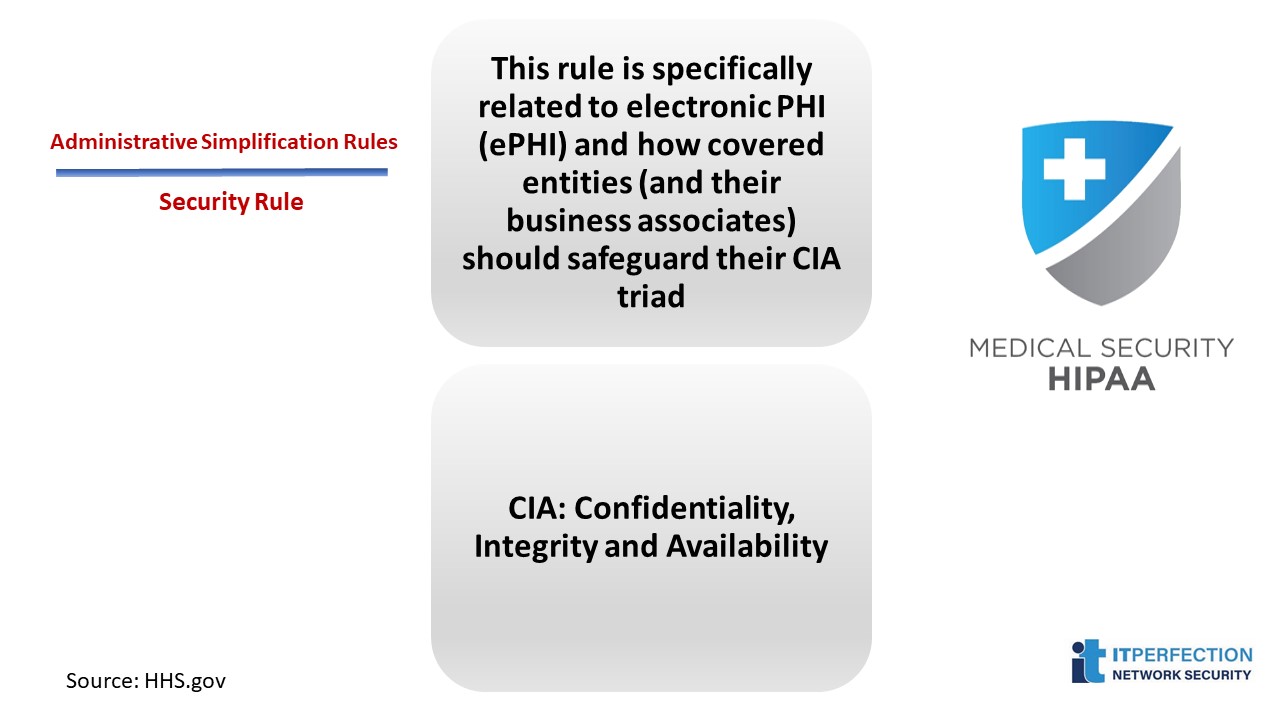
Security Rule
The security rule is specifically related to electronic protected health information (ePHI) and how covered entities should safeguard their CIA triad.
Security Rule- Safeguards
The security rule requires covered entities to use three types of safeguards:
- Administrative
- Physical
- Technical

Enforcement Rule
Enforcement rule establishes the guidelines for investigating violations of HIPAA.

IT Security
HIPAA privacy and HIPAA security rules are the most important to train for in IT security.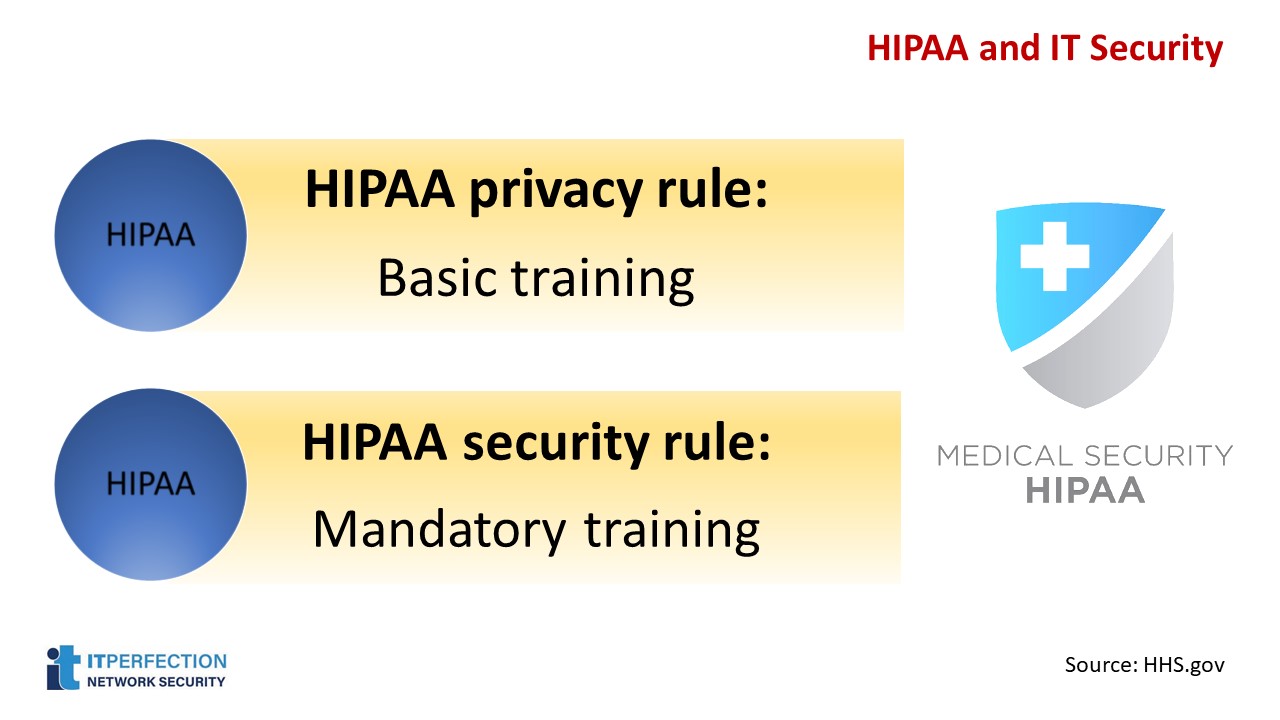
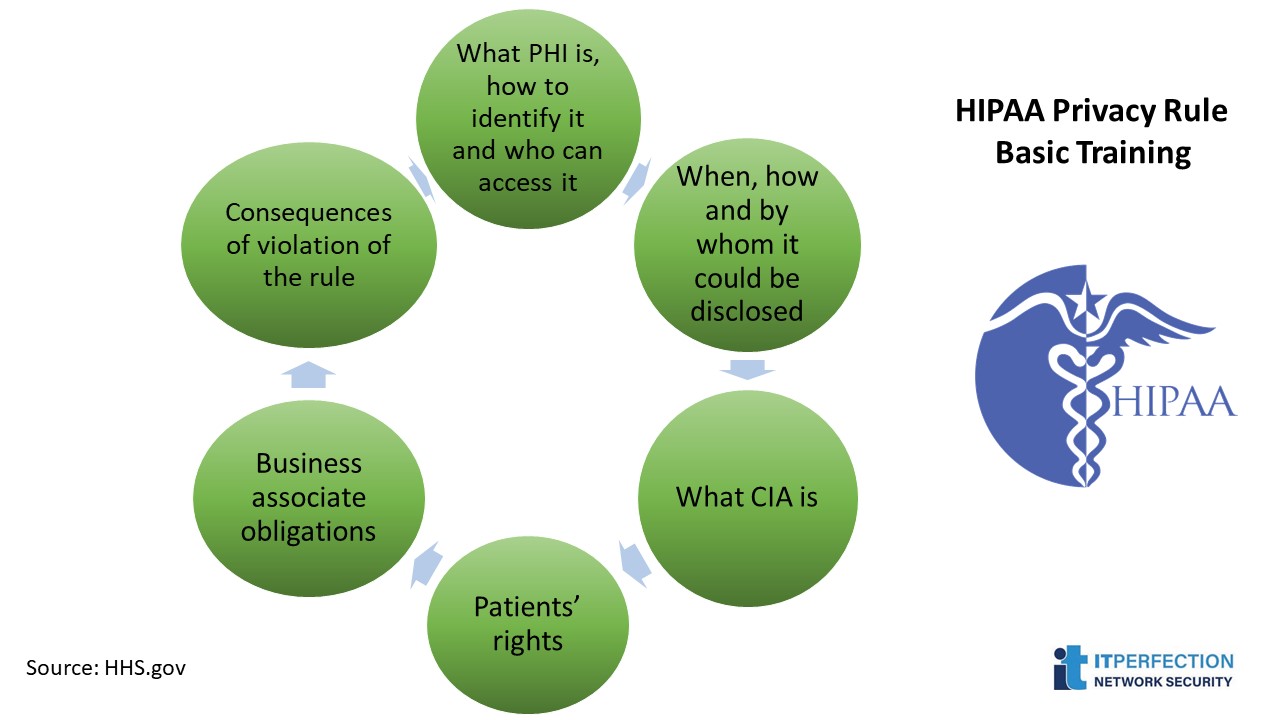
HIPAA Privacy Rule: Basic Training
- What PHI is, how to identify it and who can access it
- When, how and by whom it could be disclosed
- What CIA is
- Patients’ rights
- Business associate obligations
- Consequences of violation of the rule
HIPAA Security Rule: Mandatory Training
- Potential threats to information security related to the use of internal information systems (password shared to other people), social media, websites, emails, and devices
- How to protect from those threats (encryption, e-signatures, etc.)
- Actions to take when something goes wrong or is not normal
- Any other information security policy, guideline or procedure
- Security updates (i.e. new internal policy)
- Audits Consequences of not following the security rule

You can read more details in this post: HIPAA Compliance
Section 2: Administrative Safeguards
EPHI is to implement reasonable and appropriate administrative safeguards that establish the foundation for a covered entity’s security program. The objectives of this paper are to:
- Reviewing each Administrative Safeguards standard and implementation specification listed in the Security Rule.
- Discussing the purpose for each standard.
- Providing sample questions that covered entities may want to consider when implementing the Administrative Safeguards.
The Security Rule defines administrative safeguards as, “administrative actions, and policies and procedures, to manage the selection, development, implementation, and maintenance of security measures to protect electronic protected health information and to manage the conduct of the covered entity’s workforce in relation to the protection of that information.”

Nine Standards
Administrative Safeguards includes nine standards
- Security Risk Management – STANDARD § 164.308(a) (1)
- Assigned Security Responsibility- STANDARD § 164.308(a) (2)
- Workforce Security- STANDARD § 164.308(a) (3)
- Information Access Management- STANDARD § 164.308(a) (4)
- Security Awareness and Training – STANDARD § 164.308(a) (5)
- Security Incident Procedures- STANDARD § 164.308(a) (6)
- Contingency Plan- STANDARD § 164.308(a) (7)
- Evaluation- STANDARD § 164.308(a) (8)
- Business Associate Contracts and Other Arrangements- STANDARD § 164.308(b) (1)

Security Risk Management – STANDARD § 164.308(a) (1)
The first standard under Administrative Safeguards section is the Security Management Process.

Assigned Security Responsibility- STANDARD § 164.308(a) (2)
The purpose of this standard is to identify who will be operationally responsible for assuring that the covered entity complies with the Security Rule.

Workforce Security- STANDARD § 164.308(a) (3)
For each workforce member, or job function, the covered entity must identify the EPHI that is needed, when it is needed, and make reasonable efforts to control access to the EPHI.

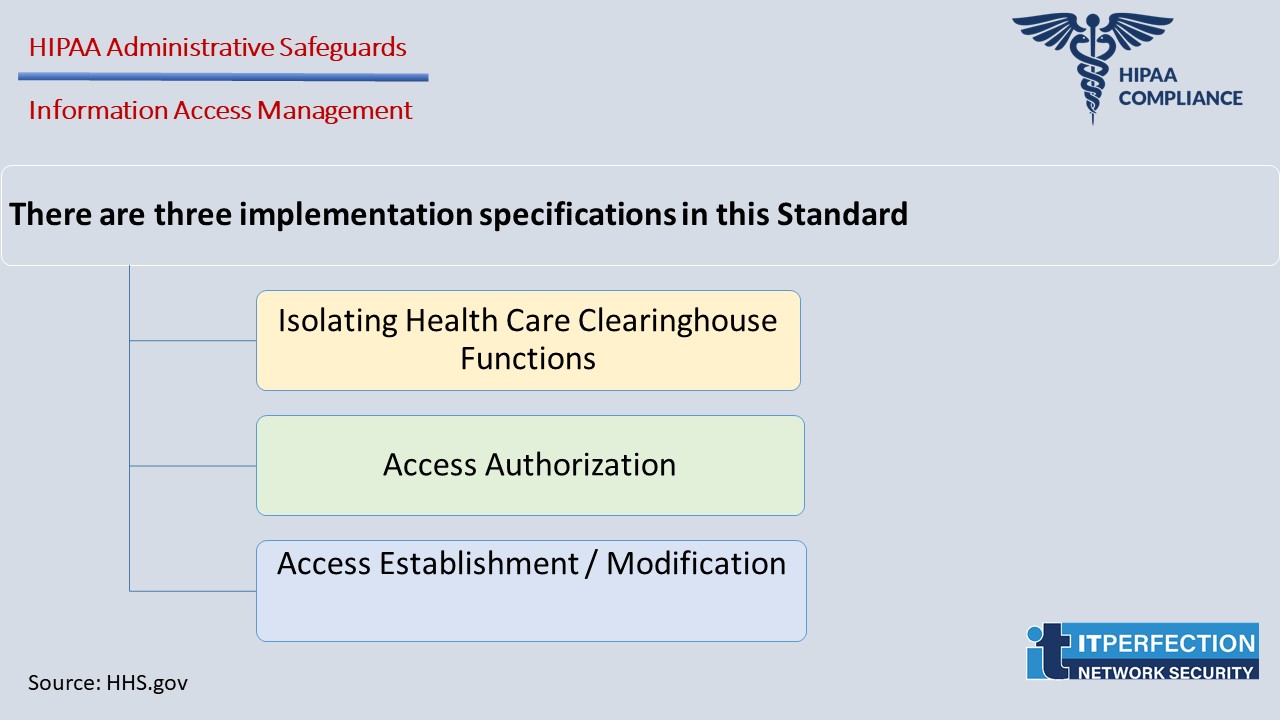
Information Access Management- STANDARD § 164.308(a)(4)
By implementing this standard, the risk of inappropriate disclosure, alteration, or destruction of EPHI is minimized.
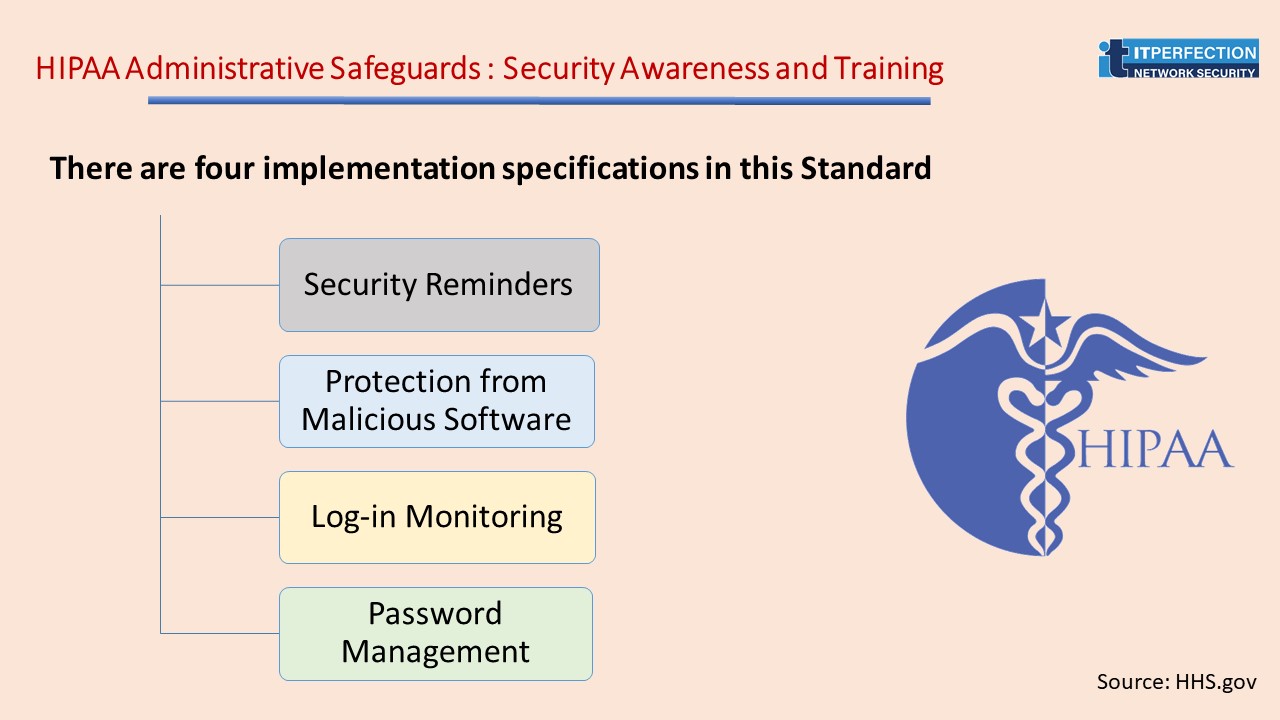
Security Awareness and Training – STANDARD § 164.308(a) (5)
Many security risks and vulnerabilities within covered entities are internal. This is why the next standard, Security Awareness and Training, is so important.
Security Incident Procedures- STANDARD § 164.308(a) (6)
The Security Rule defines a security incident as, “the attempted or successful unauthorized access, use, disclosure, modification, or destruction of information or interference with system operations in an information system.”

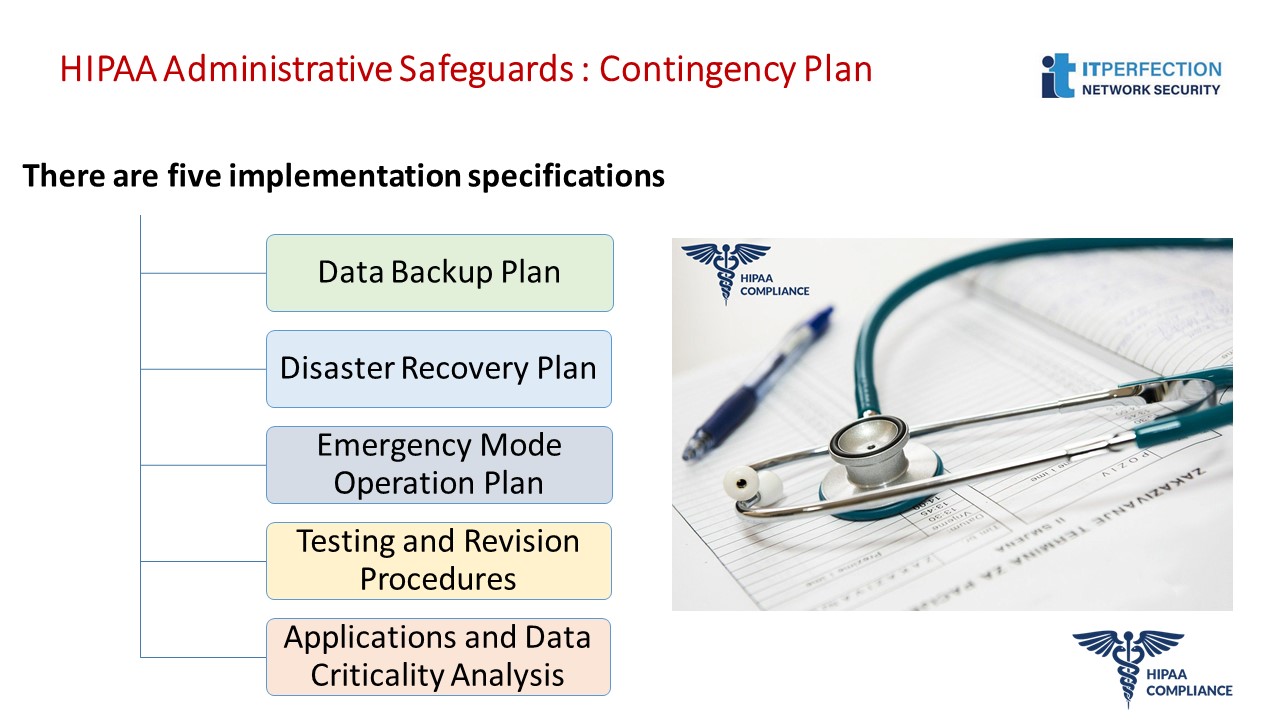
Contingency Plan- STANDARD § 164.308(a) (7)
The purpose of contingency planning is to establish strategies for recovering access to EPHI should the organization experience an emergency or other occurrence, such as a power outage and/or disruption of critical business operations.
Evaluation- STANDARD § 164.308(a) (8)
Covered entities must implement ongoing monitoring and evaluation plans. Covered entities must periodically evaluate their strategy and systems to ensure that the security requirements continue to meet their organizations’ operating environments.

Business Associate Contracts and Other Arrangements- STANDARD § 164.308(b) (1)
This standard is comparable to the Business Associate Contract standard in the Privacy Rule, but is specific to business associates that create, receive, maintain or transmit EPHI.

Read more about administrative safeguards
Section 3: Physical Safeguards
A covered entity must consider all physical access to EPHI. This may extend outside of an actual office, and could include workforce members’ homes or other physical locations where they access EPHI.
Physical Safeguards: Standards
These standards include:
1. Facility Access Controls – STANDARD § 164.310(a)(1)
2. Workstation Use – STANDARD § 164.310 ( b )
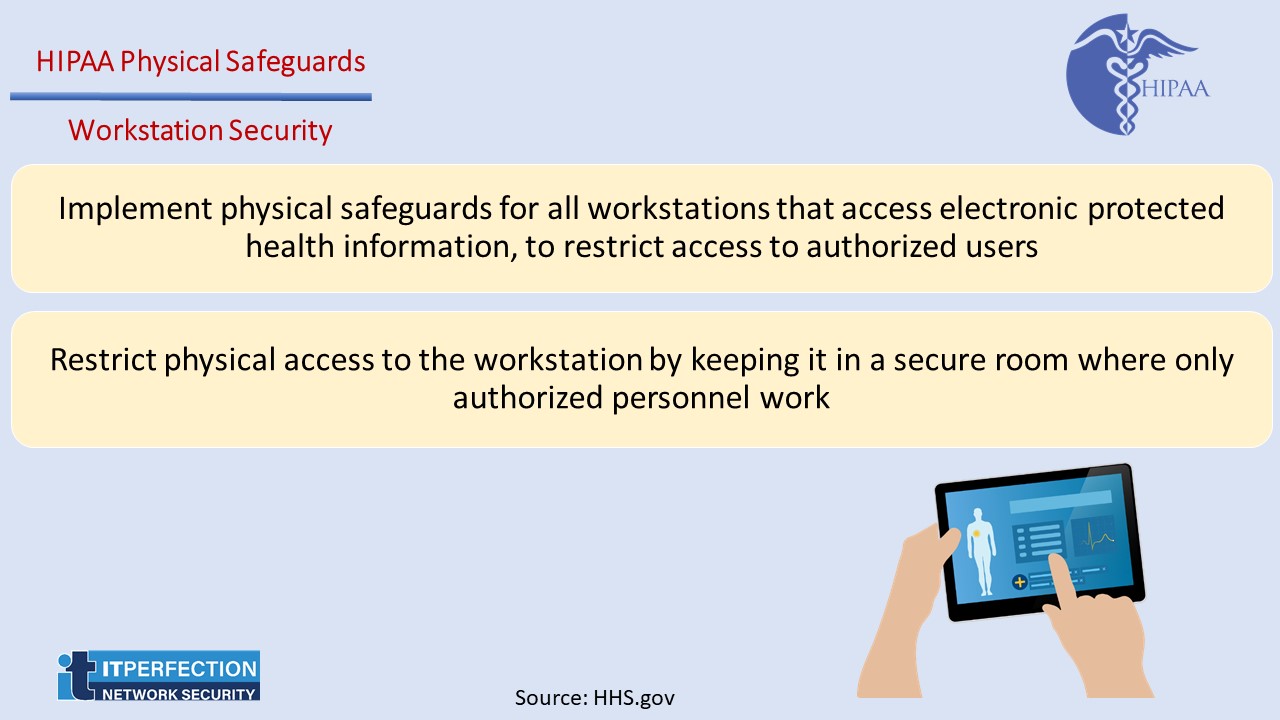
3. Workstation Security – STANDARD § 164.310(c)
4. Device and Media Controls – STANDARD § 164.310(d) (1)
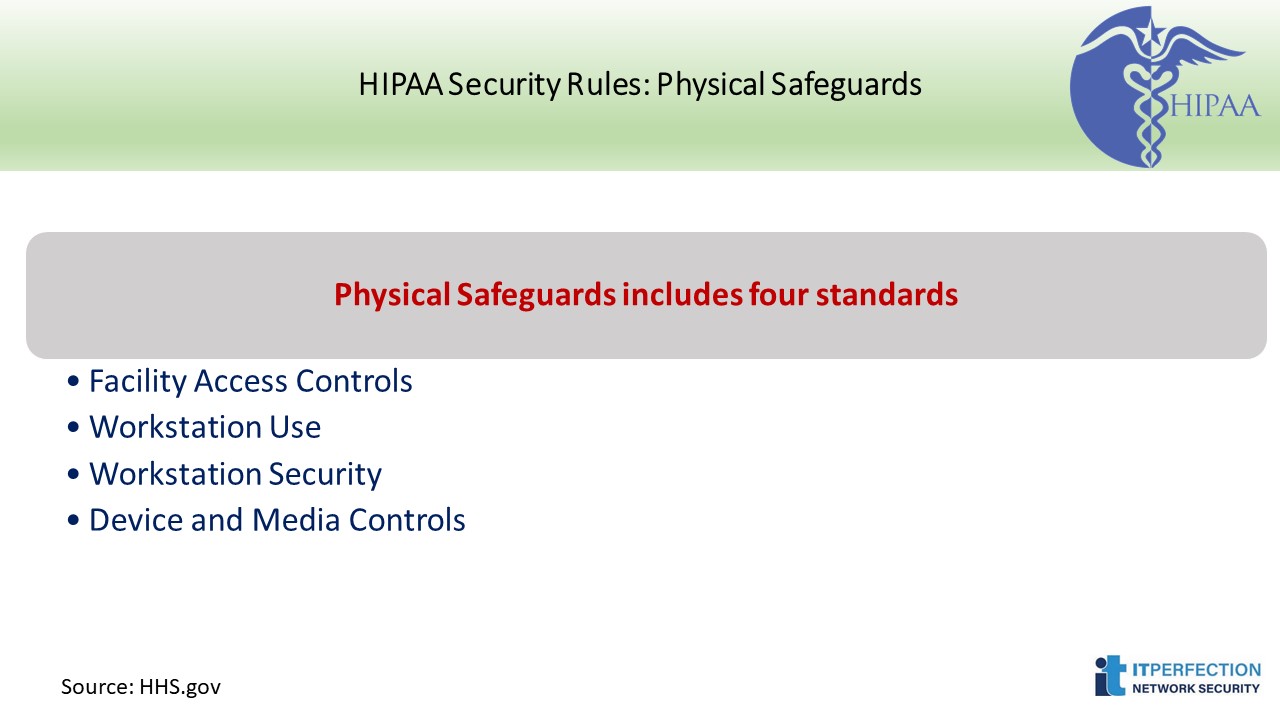
Facility Access Controls- STANDARD § 164.310(a)(1)
This standard requires covered entities to: “Implement policies and procedures to limit physical access to its electronic information systems and the facility or facilities in which they are housed, while ensuring that properly authorized access is allowed.”
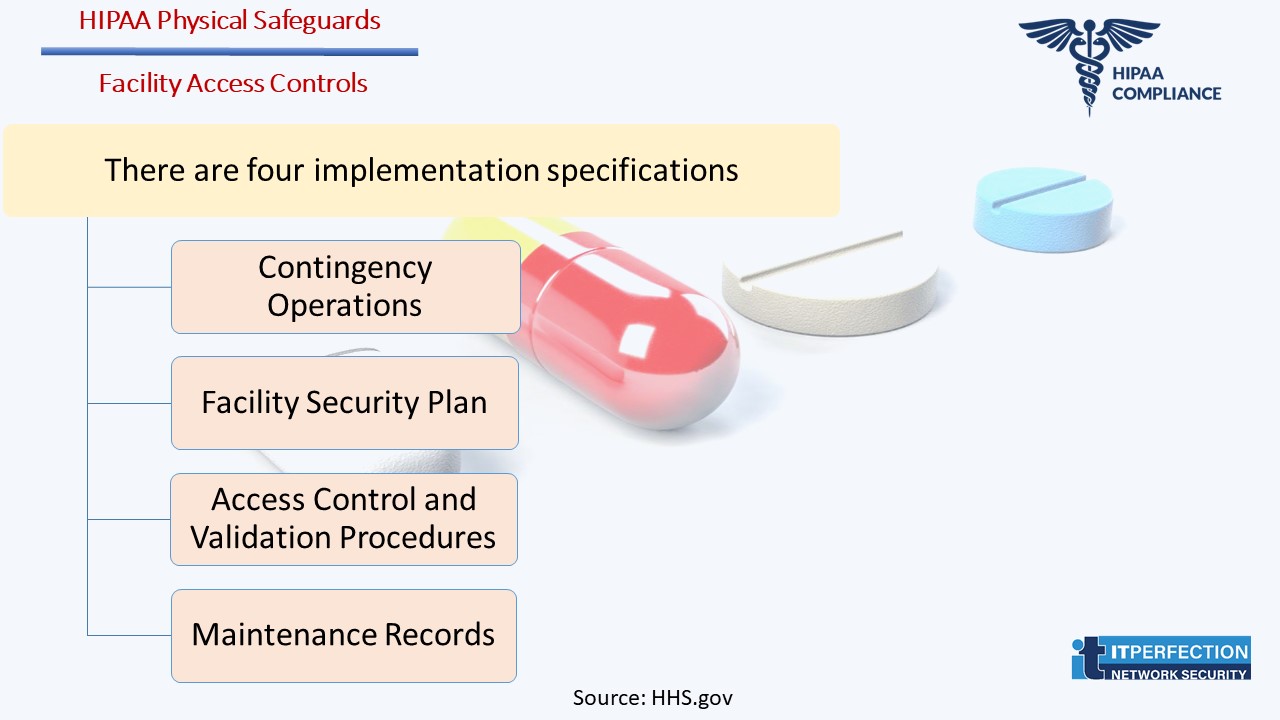
Workstation Security – STANDARD § 164.310(c)
It is a standard with no implementation specifications. Workstation Security standard addresses how workstations are to be physically protected from unauthorized users. This standard requires that covered entities: “Implement physical safeguards for all workstations that access electronic protected health information, to restrict access to authorized users.”
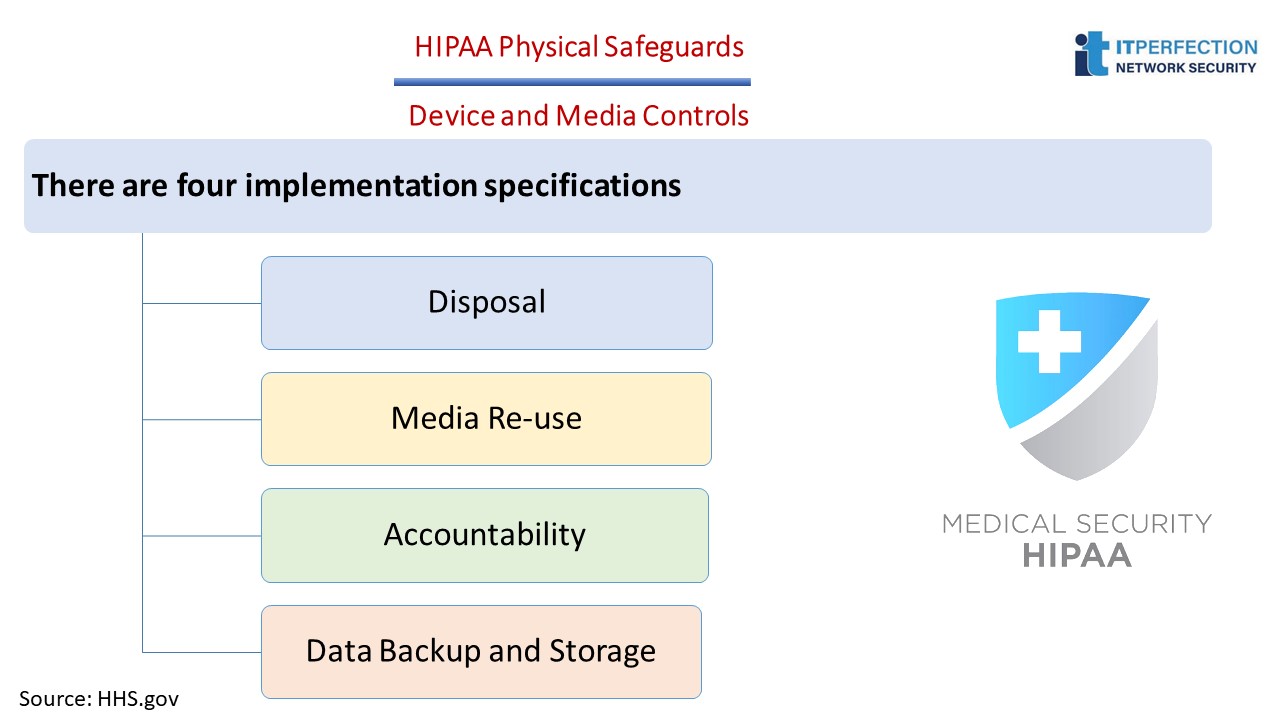
Device and Media Controls – STANDARD § 164.310(d) (1)
The Device and Media Controls standard requires covered entities to: “Implement policies and procedures that govern the receipt and removal of hardware and electronic media that contain electronic protected health information, into and out of a facility, and the movement of these items within the facility.”
Read more about physical safeguards
Section 4: Technical Safeguards
The Security Rule defines technical safeguards in “the technology and the policy and procedures for its use that protect electronic protected health information and control access to it.”
Technical Safeguard: Standards
This Safeguard includes nine standards, all of which we will discuss. These standards include:
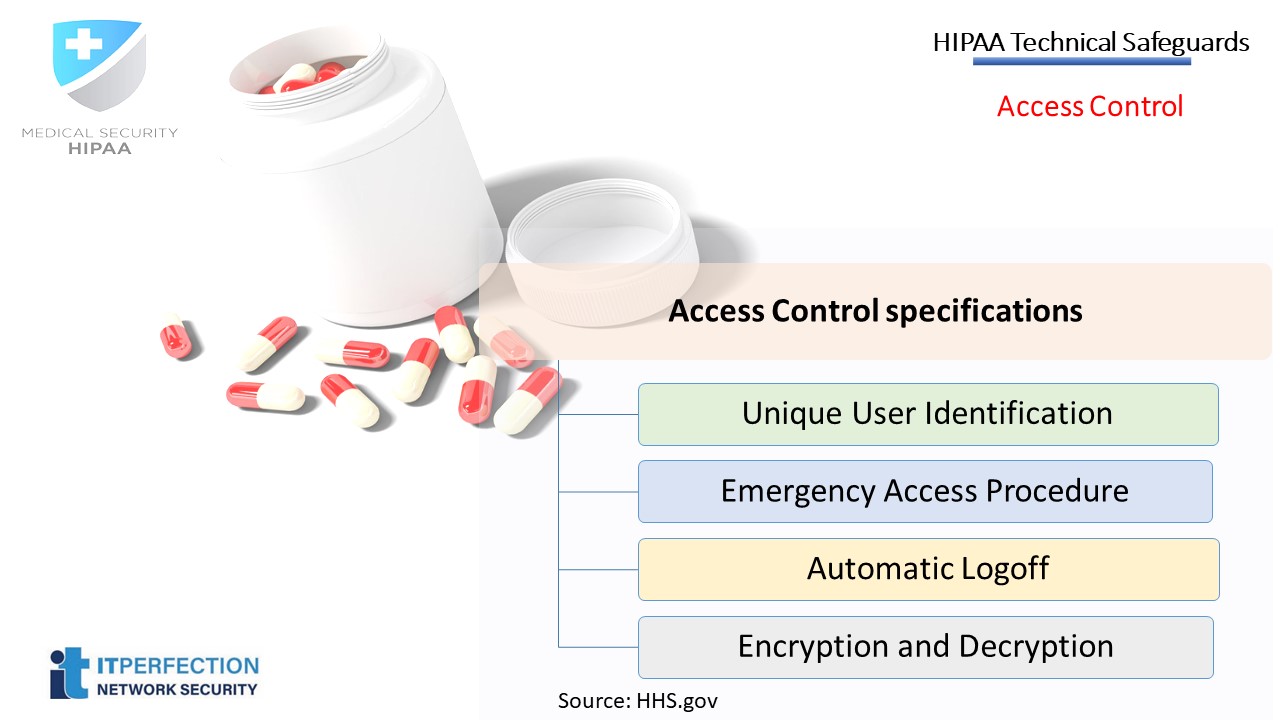
1. Access Control – STANDARD § 164.312(a ) (1)
2. Audit Controls – STANDARD § 164.312 (b)
3. Integrity- STANDARD § 164.312(c) (1)
4. Person or Entity Authentication – STANDARD § 164.312(d)
5. Transmission Security – STANDARD § 164.312(e) (1)

Access Control – STANDARD § 164.312(a ) (1)
Access controls provide users with rights and/or privileges to access and perform functions using information systems, applications, programs, or files.
Audit Controls – STANDARD § 164.312 (b)
A covered entity must consider its risk analysis and organizational factors, such as current technical infrastructure, hardware and software security capabilities, to determine reasonable and appropriate audit controls for information systems that contain or use EPHI.

Integrity – STANDARD § 164.312(c) (1)
The integrity of data can be compromised by both technical and non-technical sources. Workforce members or business associates may make accidental or intentional changes that improperly alter or destroy EPHI. Data can also be altered or destroyed without human intervention, such as by electronic media errors or failures.
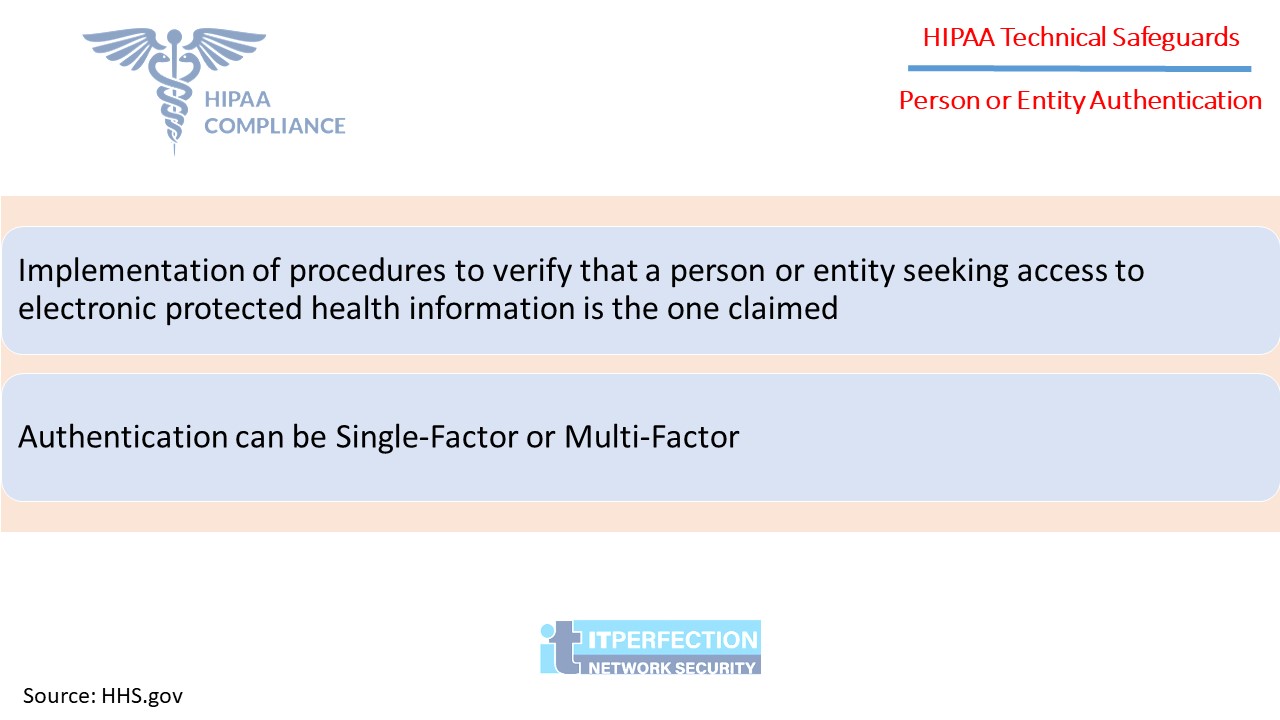
Person or Entity Authentication – STANDARD § 164.312(d)
This standard has no implementation specifications. This standard requires a covered entity to: “Implement procedures to verify that a person or entity seeking access to electronic protected health information is the one claimed.”
Transmission Security – STANDARD § 164.312(e) (1)
A covered entity must identify the available and appropriate means to protect EPHI as it is transmitted, select appropriate solutions, and document its decisions.
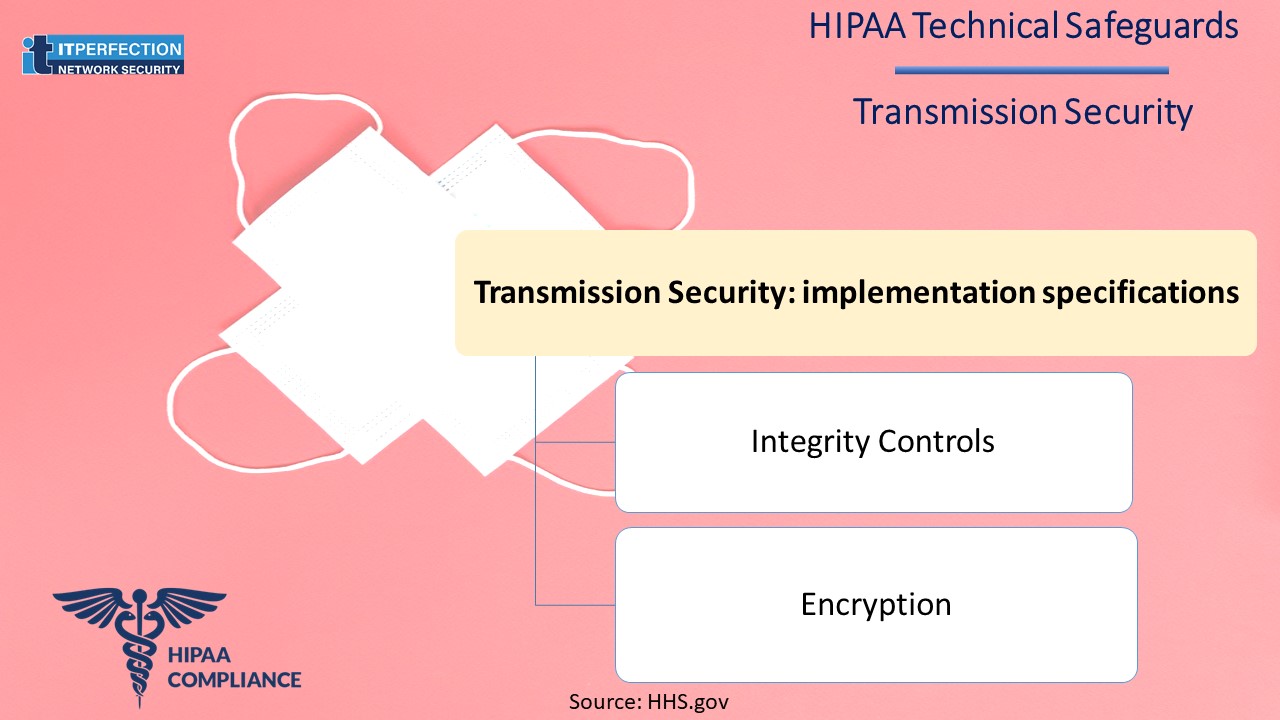
Read more about technical safeguards
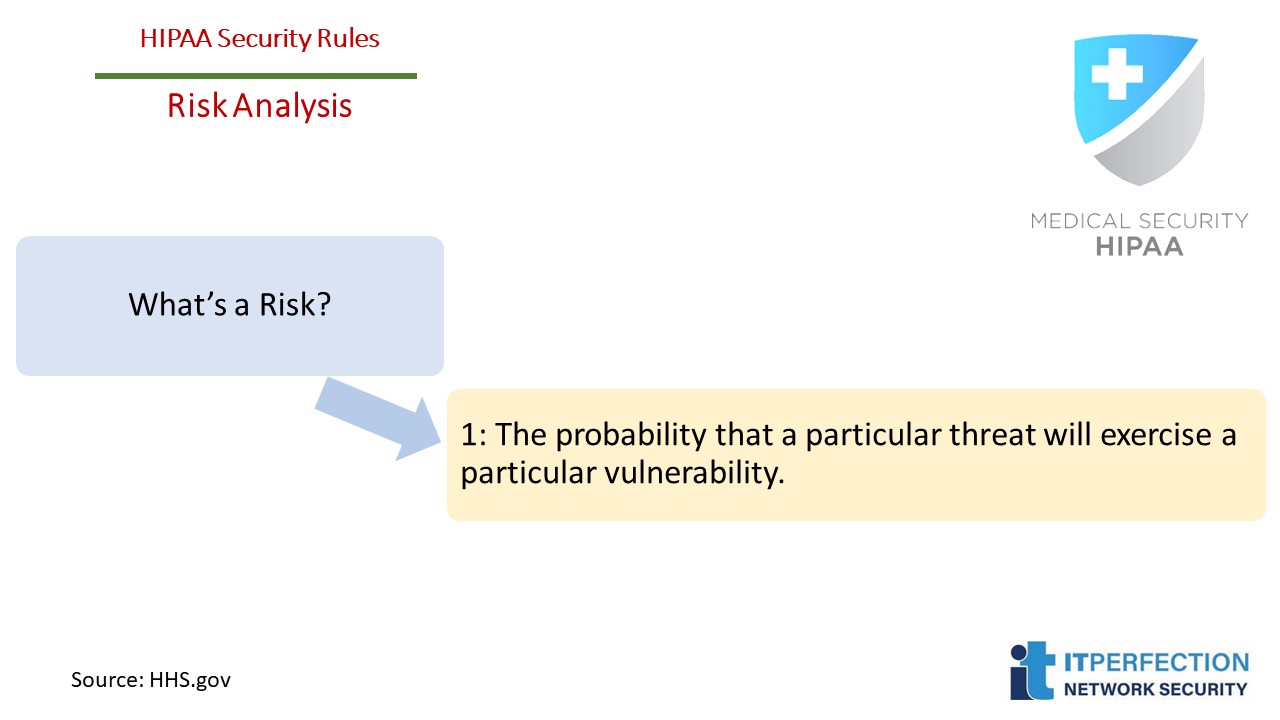
Section 5: Risk Analysis
Risks arise from legal liability or mission loss due to:
- Unauthorized (malicious or accidental) disclosure, modification, or destruction of information
- Unintentional errors and omissions
- IT disruptions due to natural or man-made disasters
- Failure to exercise due care and diligence in the implementation and operation of the IT system.”
Risk Analysis: Typical Steps
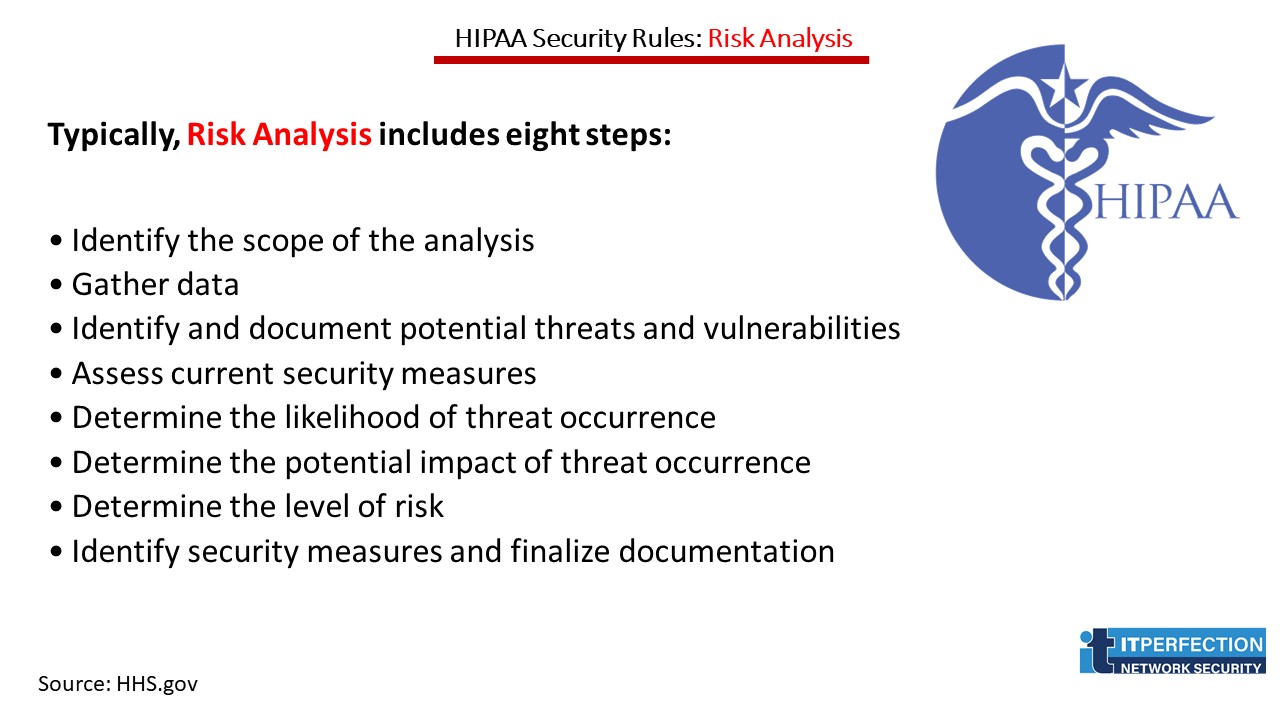
Identify the Scope of the Analysis
The risk analysis scope that the Security Rule requires is the potential risks and vulnerabilities to the confidentiality, availability and integrity of all EPHI that a covered entity creates, receives, maintains, or transmits. This includes EPHI in all forms of electronic media.

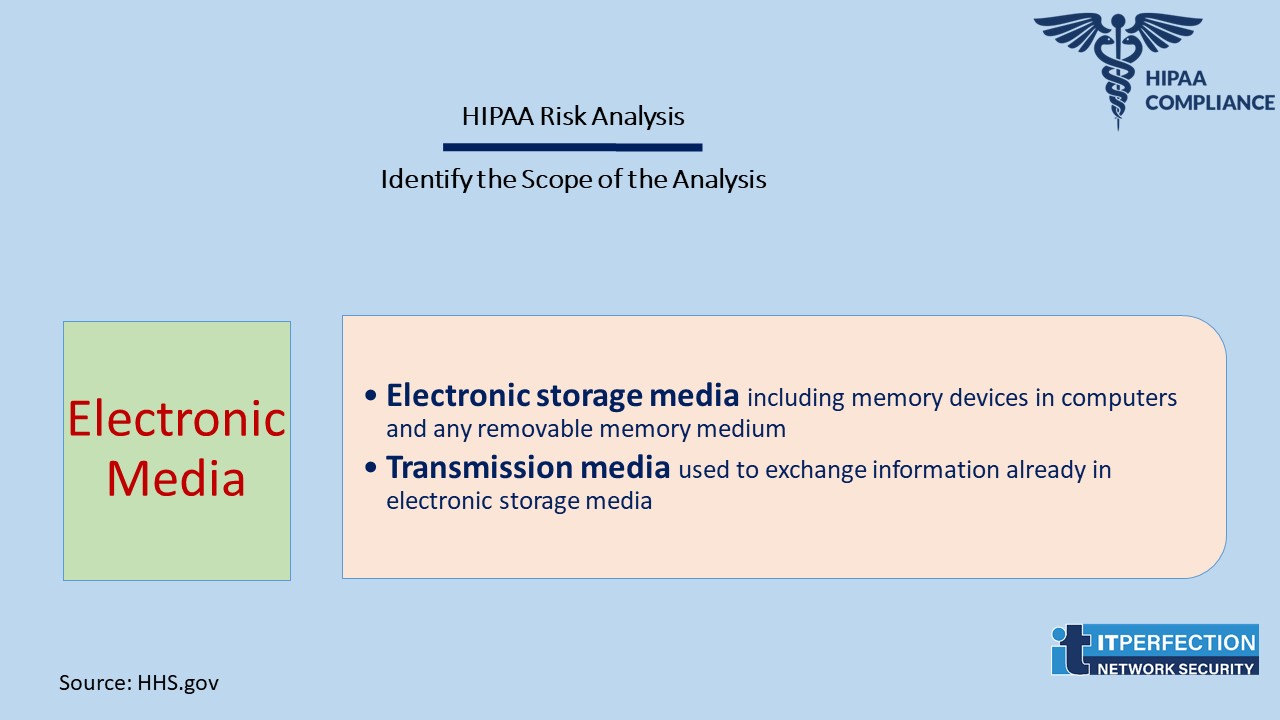
Identify the Scope of the Analysis
Electronic media is defined:
- Electronic storage media including memory devices in computers (hard drives) and any removable/transportable digital memory medium, such as magnetic tape or disk, optical disk, or digital memory card; or
- Transmission media used to exchange information already in electronic storage media. This media include for example, the internet, extranet, leased lines, dial-up lines, private networks, and the physical movement of removable/transportable electronic storage media.
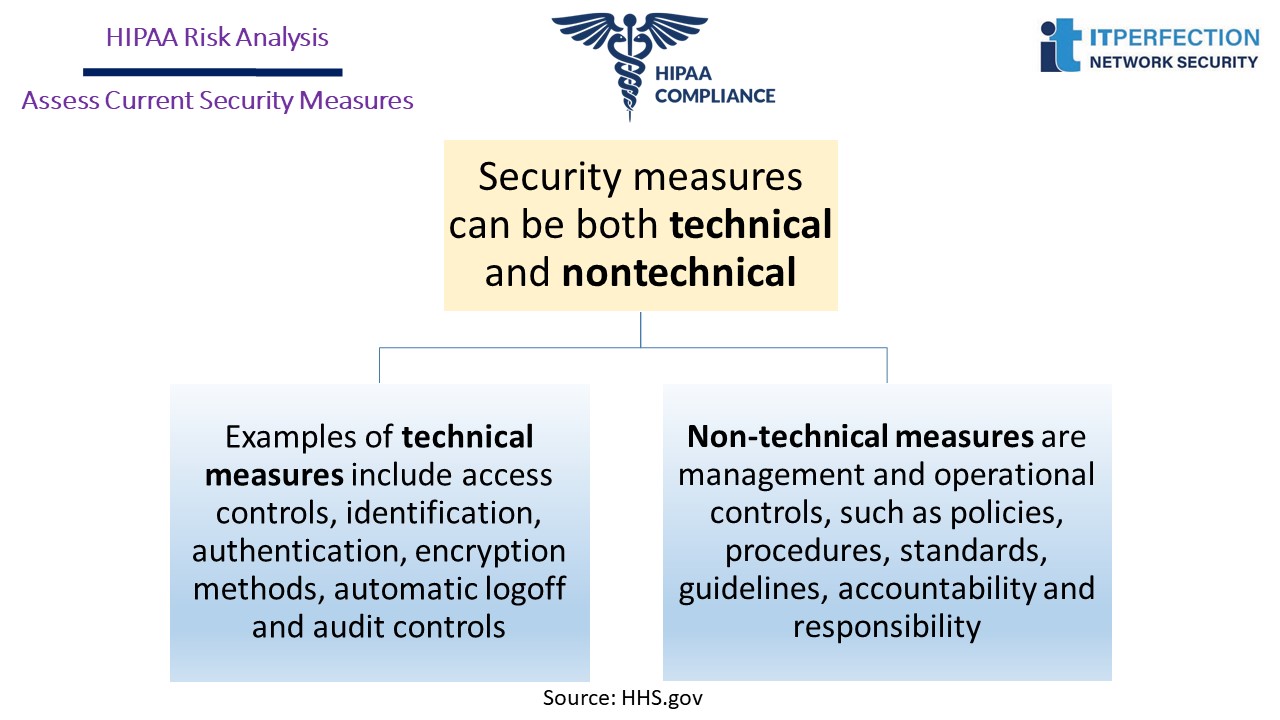
Assess Current Security Measures
The goal of this step is to analyze current security measures implemented to minimize or eliminate risks to EPHI.
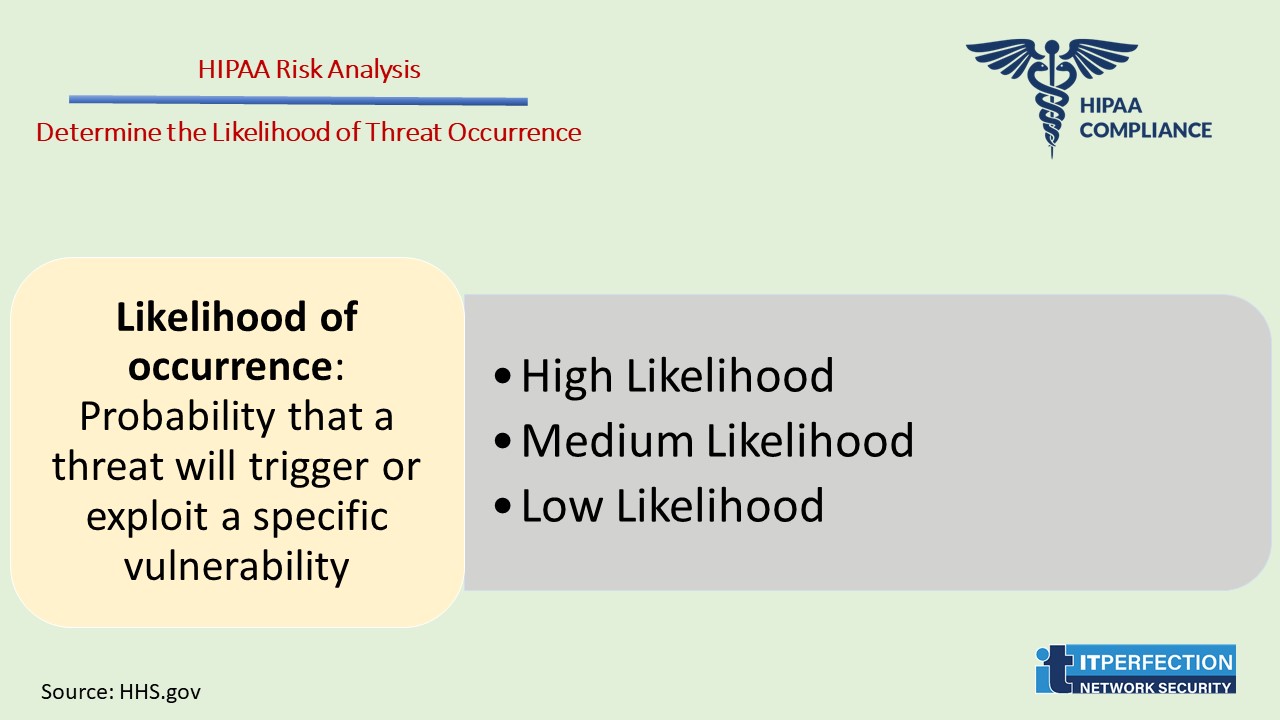
Determine the Likelihood of Threat Occurrence
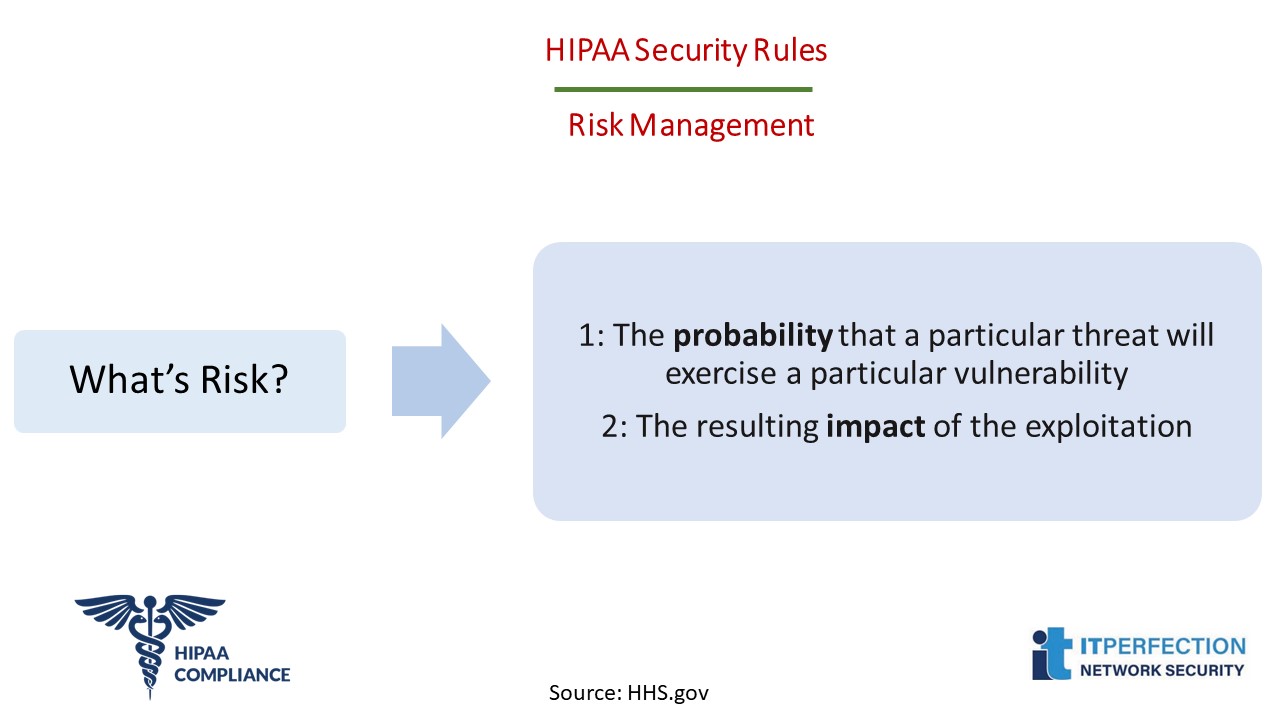
Likelihood of occurrence: Probability that a threat will trigger or exploit a specific vulnerability.
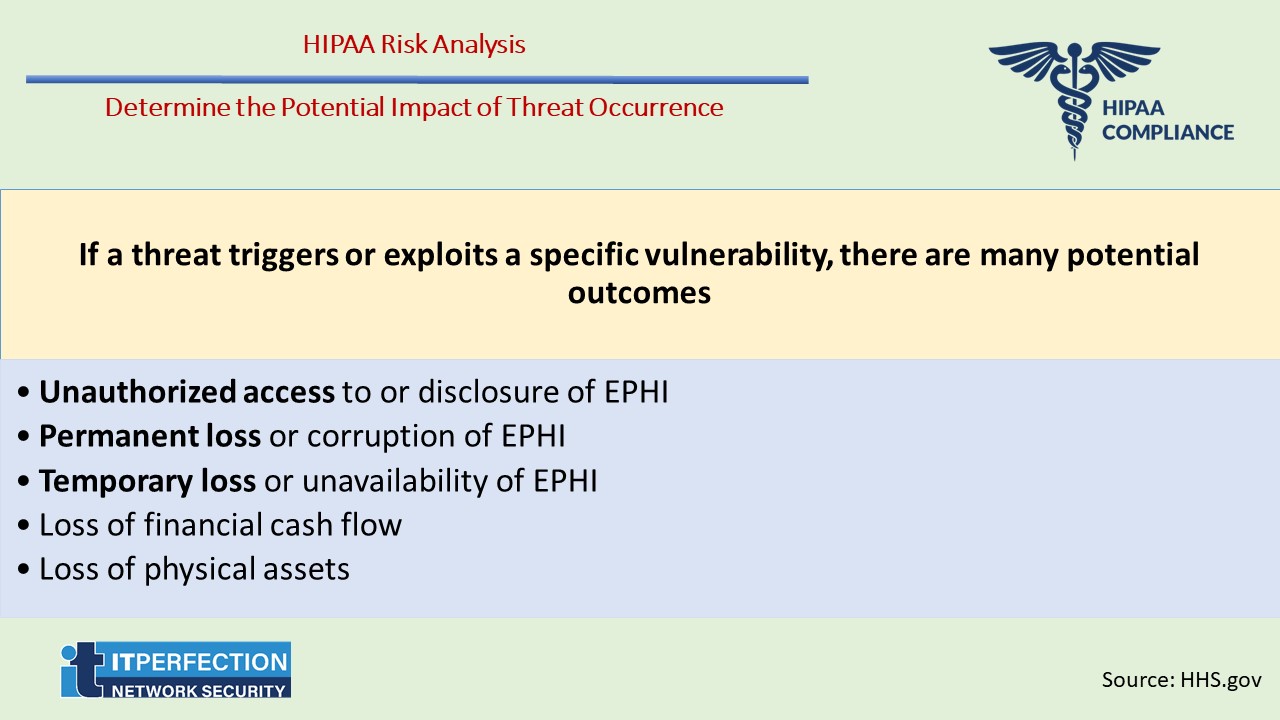
Determine the Potential Impact of Threat Occurrence
If a threat triggers or exploits a specific vulnerability, there are many potential outcomes. For covered entities, the most common outcomes include, but are not limited to:
1. Unauthorized access to or disclosure of EPHI
2. Permanent loss or corruption of EPHI
3. Temporary loss or unavailability of EPHI
4. Loss of financial cash flow
5. Loss of physical assets
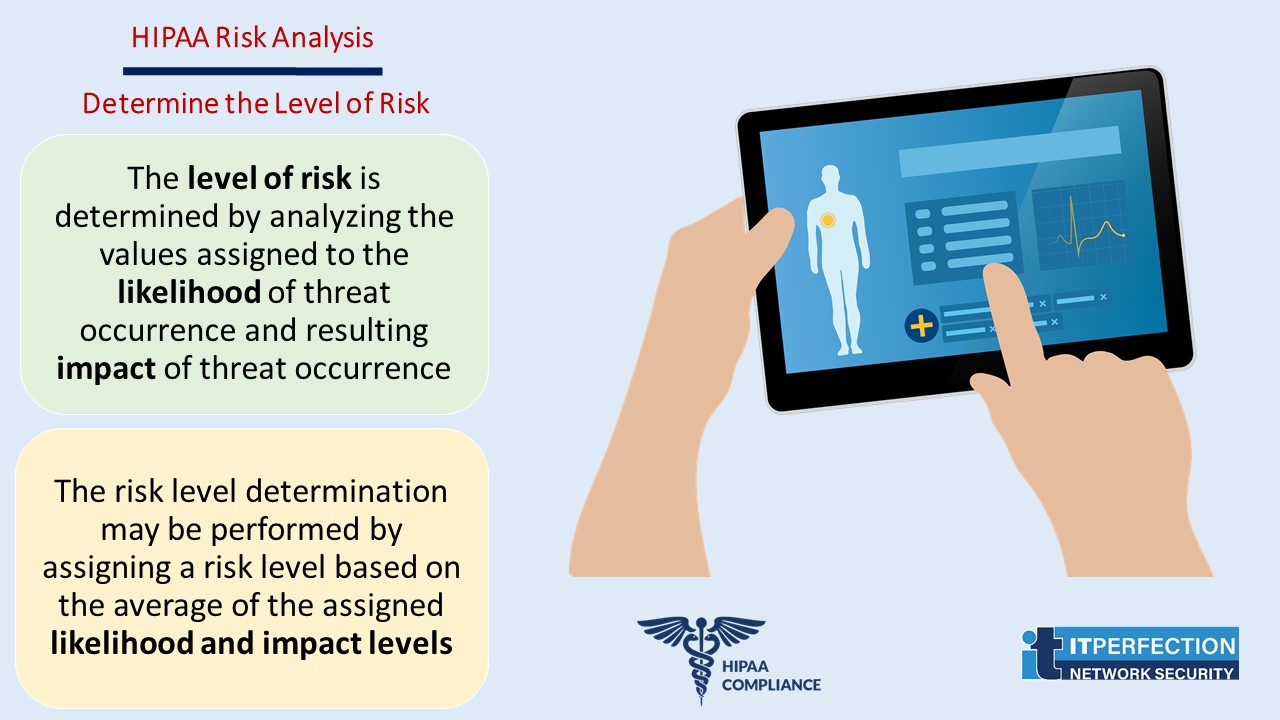
Determine the Level of Risk
The level of risk is determined by analyzing the values assigned to the likelihood of threat occurrence and resulting impact of threat occurrence. The risk level determination may be performed by assigning a risk level based on the average of the assigned likelihood and impact levels.
Identify Security Measures and Finalize Documentation
When identifying security measures that can be used, it is important to consider factors such as: the effectiveness of the security measure; legislative or regulatory requirements that require certain security measures to be implemented; and requirements of the organization’s policies and procedures. Any potential security measures that can be used to reduce risks to EPHI should be included in documentation.

Section 6: Risk Management
Implement security measures sufficient to reduce risks and vulnerabilities to a reasonable and appropriate level to comply with the General Requirements of the Security Rule.
Risk Management- Steps
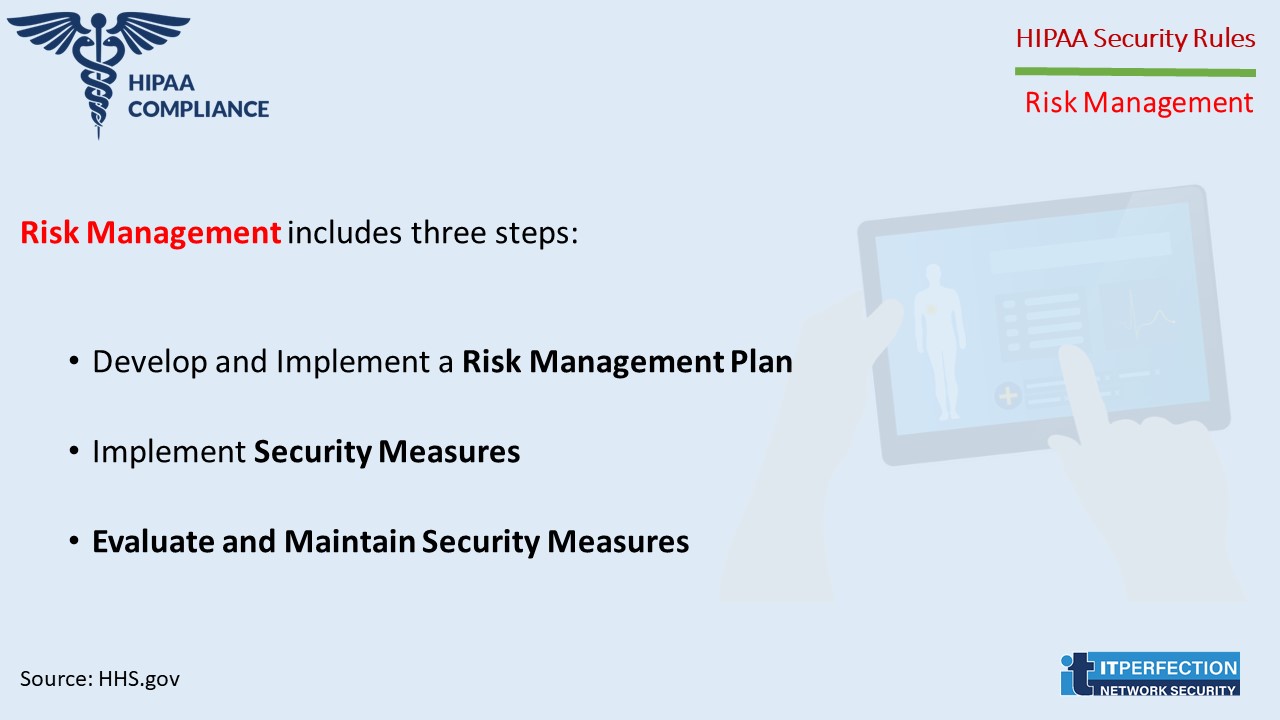
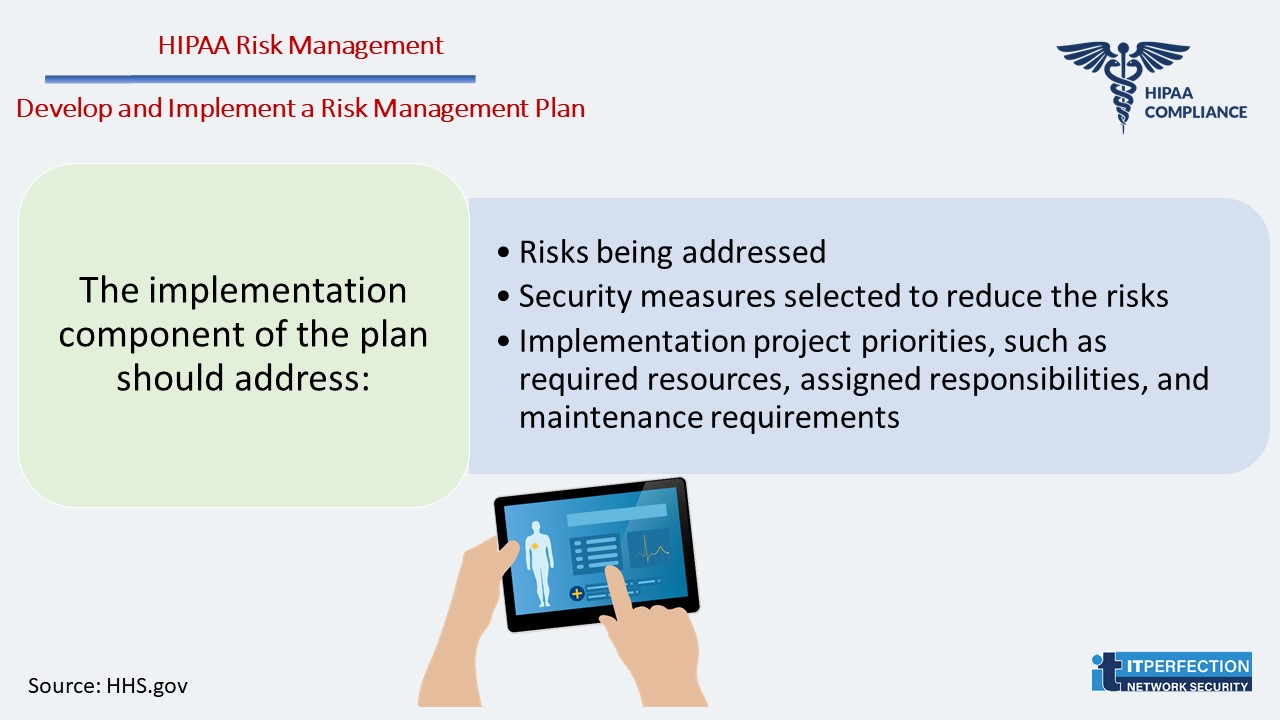
Develop and Implement a Risk Management Plan
For the risk management plan to be successful, key members of the covered entity’s workforce, including senior management and other key decision makers, must be involved.

Develop and Implement a Risk Management Plan
An important component of the risk management plan is the plan for implementation of the selected security measures.
Evaluate and Maintain Security Measures
Risk management is not one-time activity. Risk management is ongoing, dynamic process that must be periodically reviewed and updated in response to changes in the environment.

Read more about risk management
Section 7: Security Standards Organizational, Policies and Procedures and Documentation Requirements
The objective of this post is reviewing each Organizational Requirements and Policies and Procedures and Documentation Requirements standard and implementation specification listed in the Security Rule. This topic includes four standards, all of which we will discuss. These standards include:
1. Business Associate Contracts or Other Arrangements – STANDARD§ 164.314(a) (1)
2. Requirements for Group Health Plans – STANDARD § 164.314(b) (1)
3. Policies and Procedures – STANDARD§ 164.316(a)
4. Documentation – STANDARD§ 164.316(b) (1)

Business Associate Contracts or Other Arrangements Standard
For example, a health care clearinghouse may be a business associate and is also a covered entity under HIPAA. A software vendor may be a business associate as well; however, it is not, in that capacity, a covered entity. In both cases, the organizations could perform certain functions, activities or services on behalf of the covered entity and would therefore be business associates.

Requirements for Group Health Plans Standard
The health plan has access to EPHI beyond summary information and enrollment information or to EPHI other than that which has been authorized under § 164.508, the plan documents must contain language similar to that already required by the Privacy Rule.

Policies and Procedures Standard
Policies and Procedures standard is not to be construed to permit or excuse an action that violates any other standard, implementation specification, or other requirements of this subpart.

Documentation Standard
The Time Limit implementation specification requires covered entities to: “Retain the documentation required of this section for 6 years from the date of its creation or the date when it last was in effect, whichever is later.”
Organizations often make documentation available in printed manuals and/or on Intranet websites. The Updates implementation specification requires covered entities to: “Review documentation periodically, and update as needed, in response to environmental or operational changes affecting the security of the electronic protected health information.”

Section 8: Implementation for the Small Providers
Small providers that are covered entities have unique business and technical environments that provide both opportunities and challenges related to compliance with the Security Rule.

Many of the standards contain implementation specifications but where there is no implementation specification for a particular standard, compliance with the standard itself is required.
- A required implementation specification is similar to a standard, in that a covered entity must comply with it. For example, all covered entities including small providers must conduct a “Risk Analysis”.
- For addressable implementation specifications, covered entities must perform an assessment to determine whether the specification is a reasonable and appropriate safeguard in the covered entity’s environment. After performing the assessment, a covered entity decides if it will implement the addressable implementation specification;
- Factors that determine what is “reasonable” and “appropriate” include cost, size, technical infrastructure and resources. While cost is one factor entities must consider in determining whether to implement a particular security measure, some appropriate measure must be implemented. An addressable implementation specification is not optional.
- Administrative Safeguards: These provisions are defined in the Security Rule as the “administrative actions, policies, and procedures to manage the selection, development, implementation, and maintenance of security measures to protect electronic protected health information and to manage the conduct of the covered entity’s workforce in relation to the protection of that information.”
11 Standard
Standards Implementation for the Small Provider includes eleven standards.
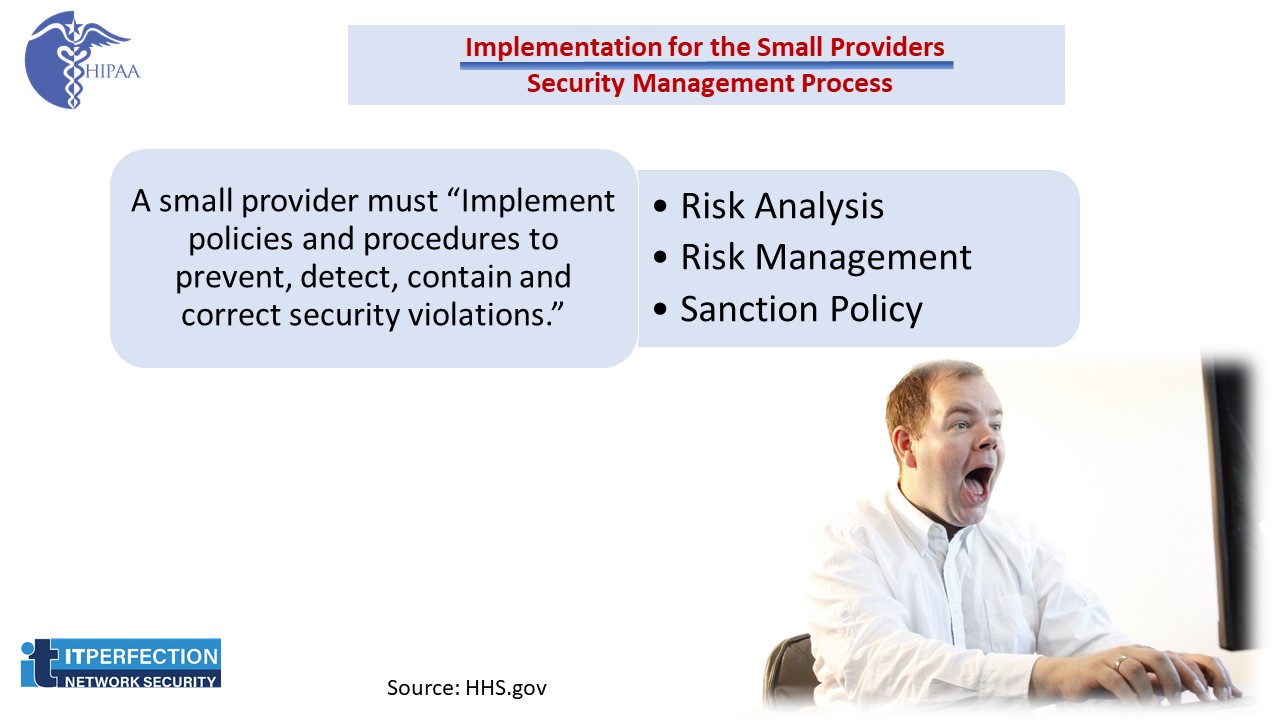
Security Management Process
- Risk Analysis: A small provider must “Conduct an accurate and thorough assessment of the potential risks and vulnerabilities to the confidentiality, integrity, and availability of electronic protected health information held by the covered entity.”
- Risk Management: A small provider must “Implement security measures sufficient to reduce risks and vulnerabilities to a reasonable and appropriate level to comply with §164.306(a).”
- Sanction Policy: The small provider must “Apply appropriate sanctions against workforce members who fail to comply with the security policies and procedures of the covered entity.”
Workface Security
A small provider must “Implement policies and procedures to ensure that all members of its workforce have appropriate access to electronic protected health information, and to prevent those workforce members who do not have access from obtaining access to electronic protected health information.”

Security Awareness and Training
A small provider must “Implement a security awareness and training program for all members of its workforce (including management).”

Contingency Plan
Data Backup Plan: The small provider must “Establish and implement procedures to create and maintain retrievable exact copies of electronic protected health information.”

Business Associate Contracts and Other Arrangements
The small provider “A covered entity may permit a business associate to create, receive, maintain, or transmit electronic protected health information on the covered entity’s behalf only if the covered entity obtains satisfactory assurances that the business associate will appropriately safeguard the information.”
Facility Access Controls
The small provider must “Implement policies and procedures to limit physical access to its electronic information systems and the facility or facilities in which they are housed, while ensuring that properly authorized access is allowed.”

Facility Access Controls: Facility Security Plan
A small provider “Implement policies and procedures to safeguard the facility and the equipment therein from unauthorized physical access, tampering, and theft.”

Facility Access Controls: Maintenance Records
A small provider must “Implement policies and procedures to document repairs and modifications to the physical components of a facility which are related to security.”
Workstation Use
The small provider must “Implement policies and procedures that specify the proper functions to be performed, the manner in which those functions are to be performed, and the physical attributes of the surroundings of a specific workstation or class of workstation that can access electronic protected health information.”

Device and Media Controls
A small provider must “Implement policies and procedures to address the final disposition of electronic protected health information, and/or the hardware or electronic media on which it is stored.”
Device and Media Controls: Data Backup and Storage
A small provider must “Create a retrievable, exact copy of electronic protected health information, when needed, before movement of equipment.”
Access Control
The small provider must “Implement technical policies and procedures for electronic information systems that maintain electronic protected health information to allow access only to those persons or software programs that have been granted access rights as specified in § 164.308(a)(4)) [(Information Access Management)].”
Person or Entity Authentication
The small provider must “Implement procedures to verify that a person or entity seeking access to electronic protected health information is the one claimed.”

Transmission Security
The small provider must “Implement technical security measures to guard against unauthorized access to electronic protected health information that is being transmitted over an electronic communications network.”
Read more about implementation for the Small provider
———–
Source: HHS.gov