In this post we are going to talk about technical Safeguards. This post is the fourth post in the HIPAA series. This series of posts is called the HIPAA Series.
The series will contain seven post:
- Security 101 for Covered Entities
- Security Standards: Administrative Safeguards
- Security Standards: Physical Safeguards
- Security Standards: technical Safeguards
- Security Standards- Organizational, Policies and Procedures and Documentation Requirements
- Basics of Risk Analysis and Risk Management
- Implementation for the Small Provider
But this series also has two spin offs. We suggest that if you do not have basic information about HIPAA, before starting this series, first read the following two posts:
Note, In across of this post:
(R)= Required, (A)= Addressable
—————————–
Source:
This article is a summary from of the hhs.gov website. With the following link:
Security Standards: Technical Safeguards
For more info please refer to hhs.gov
Technical Safeguards
The Security Rule defines technical safeguards in “the technology and the policy and procedures for its use that protect electronic protected health information and control access to it.”
The Security Rule does not require specific technology solutions. In this post, some security measures and technical solutions are provided as examples to illustrate the standards and implementation specifications.
Some solutions may be costly, especially for smaller covered entities. While cost is one factor a covered entity may consider when deciding on the implementation of a particular security measure, it is not the only factor.
Technical Safeguards includes five standards, all of which we will discuss. These standards include:
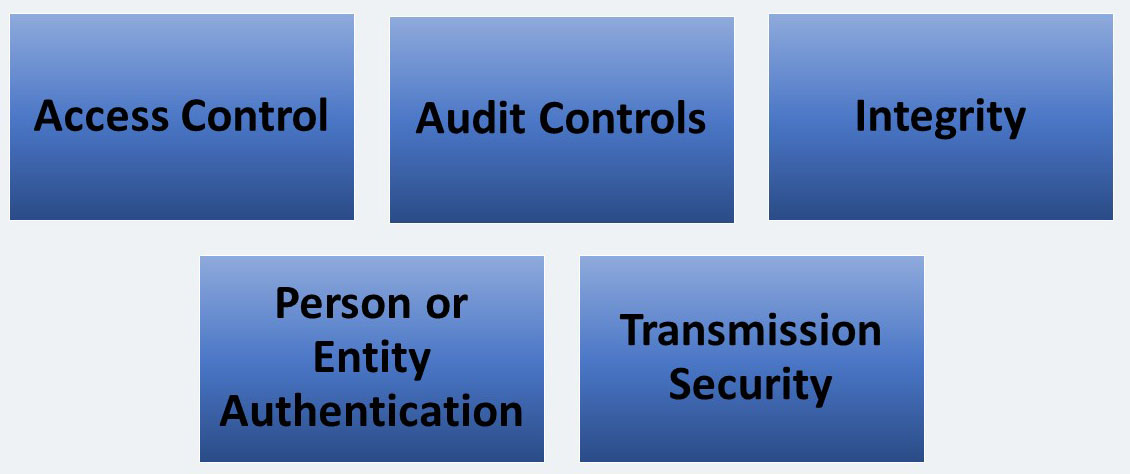
Access Control – STANDARD § 164.312(a) (1)
The Security Rule defines access “the ability or the means necessary to read, write, modify, or communicate data/information or otherwise use any system resource”. Access controls provide users with rights and/or privileges to access and perform functions using information systems, applications, programs, or files.
- Access controls should enable authorized users to access the minimum necessary information needed to perform job functions.
- Rights and/or privileges should be granted to authorize users based on a set of access rules that the covered entity is required to implement.
The Access Control standard requires a covered entity to: “Implement technical policies and procedures for electronic information systems that maintain electronic protected health information to allow access only to those persons or software programs that have been granted access rights as specified.
There are a variety of access control methods and technical controls that are available within most information systems. A covered entity can comply with this standard through a combination of access control methods and technical controls.
The Security Rule does not identify a specific type of access control method or technology to implement.
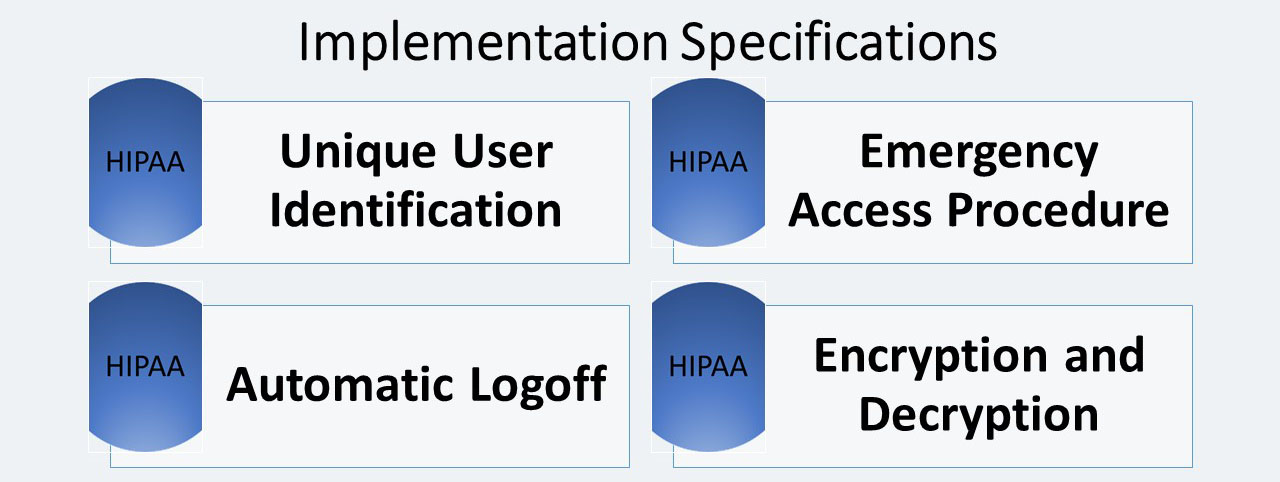
Unique User Identification (R)
A covered entity must: “Assign a unique name and/or number for identifying and tracking user identity.”
User identification is a way to identify a specific user of an information system, typically by name and/or number. A unique user identifier allows an entity to track specific user activity when that user is logged into an information system..
There is not a single format for user identification:
- Some organizations may use the employee name or a variation of the name.
- Other organizations may choose an alternative such as assignment of a set of random numbers and characters.
A randomly assigned user identifier is more difficult for an unauthorized user (e.g., a hacker) to guess, but may also be more difficult for authorized users to remember and management to recognize.
Emergency Access Procedure (R)
This implementation specification requires a covered entity to: “Establish (and implement as needed) procedures for obtaining necessary electronic protected health information during an emergency.”
Procedures must be established beforehand to instruct workforce members on possible ways to gain access to needed EPHI in, for example, a situation in which normal environmental systems, such as electrical power, have been severely damaged or rendered inoperative due to a natural or man-made disaster.

Automatic Logoff (A)
A covered entity, the covered entity must: “Implement electronic procedures that terminate an electronic session after a predetermined time of inactivity.”
As a general practice, users should logoff the system they are working on when their workstation is unattended. There will be times when workers may not have the time, or will not remember, to log off a workstation.
- Automatic logoff is an effective way to prevent unauthorized users from accessing EPHI on a workstation when it is left unattended for a period of time.
- Many applications have configuration settings for automatic logoff. After a predetermined period of inactivity the application will automatically logoff the user.
- Some systems that may have more limited capabilities may activate an operating system screen saver that is password protected after a period of system inactivity.
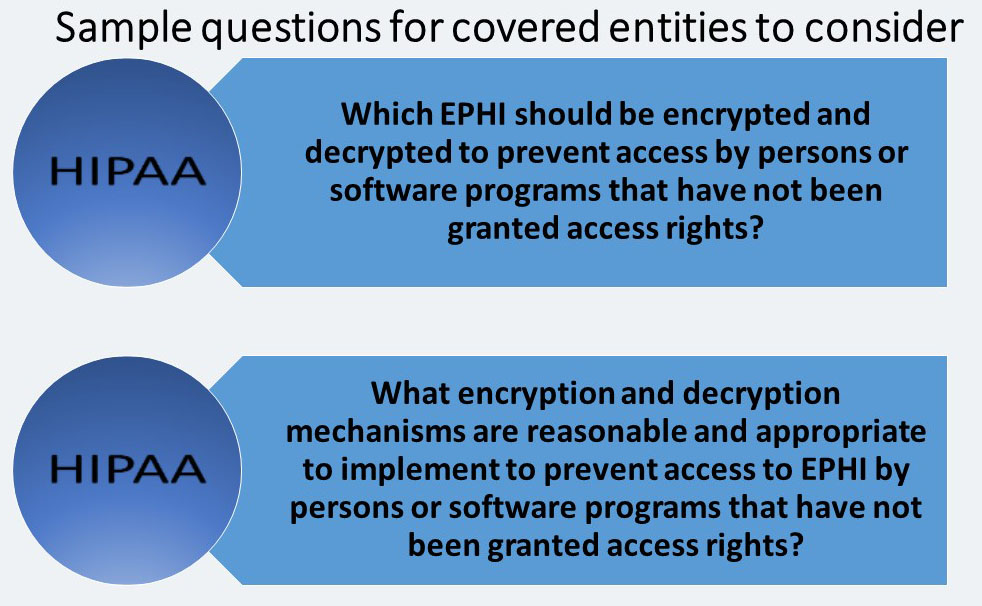
Encryption and Decryption (A)
A covered entity must: “Implement a mechanism to encrypt and decrypt electronic protected health information.”
Read this post about Data Encryption / Decryption.
Also, Read this post about E-mail Encryption / Decryption.
Audit Controls – STANDARD § 164.312 (b)
This standard has no implementation specifications.
The Audit Controls standard requires a covered entity to: “Implement hardware, software, and/or procedural mechanisms that record and examine activity in information systems that contain or use electronic protected health information.”
Most information systems provide some level of audit controls with a reporting method, such as audit reports. These controls are useful for recording and examining information system activity, especially when determining if a security violation occurred. A covered entity must consider its risk analysis and organizational factors, such as current technical infrastructure, hardware and software security capabilities, to determine reasonable and appropriate audit controls for information systems that contain or use EPHI.

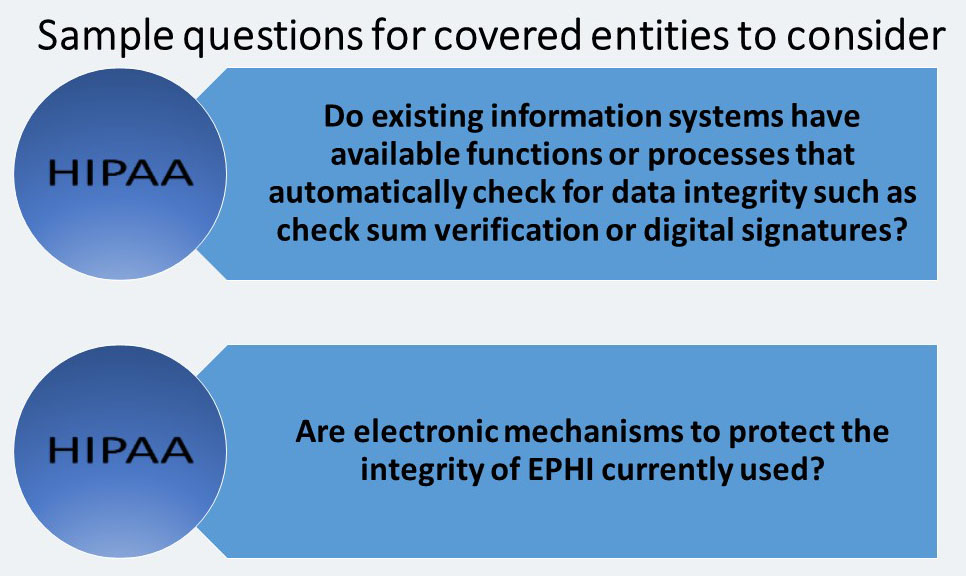
Integrity- STANDARD § 164.312(c) (1)
The next standard in the Technical Safeguards section is Integrity. Integrity is defined in the Security Rule: The property that data or information have not been altered or destroyed in an unauthorized manner.”
The integrity of data can be compromised by both technical and non-technical sources. Workforce members or business associates may make accidental or intentional changes that improperly alter or destroy EPHI. Data can also be altered or destroyed without human intervention, such as by electronic media errors or failures.
The Integrity standard requires a covered entity to: “Implement policies and procedures to protect electronic protected health information from improper alteration or destruction.” EPHI that is improperly altered or destroyed can result in clinical quality problems for a covered entity, including patient safety issues.

Mechanism to Authenticate Electronic Protected Health Information (A)
A covered entity must: “Implement electronic mechanisms to corroborate that electronic protected health information has not been altered or destroyed in an unauthorized manner.” Once covered entities have identified risks to the integrity of their data, they must identify security measures that will reduce the risks.
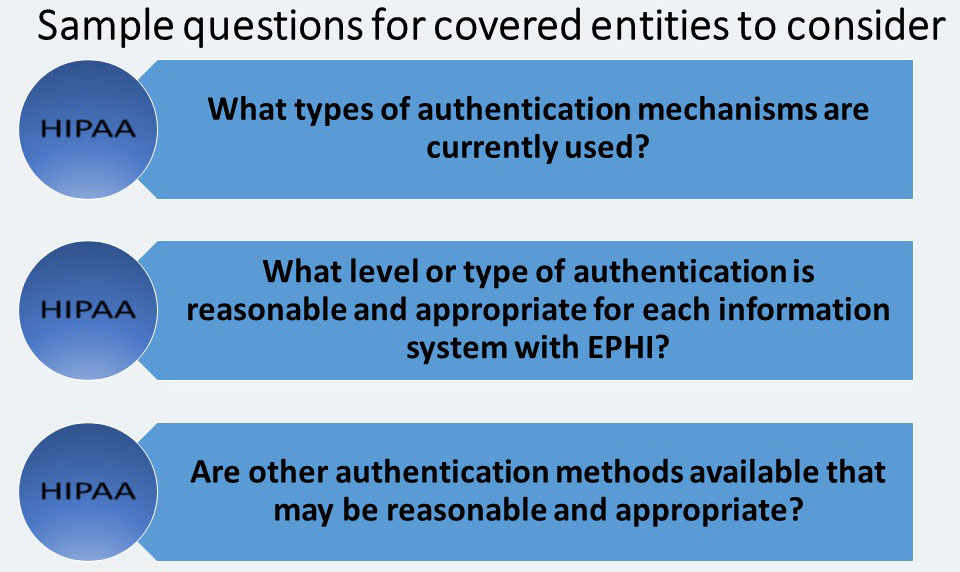
Person or Entity Authentication – STANDARD § 164.312(d)
This standard has no implementation specifications. This standard requires a covered entity to: “Implement procedures to verify that a person or entity seeking access to electronic protected health information is the one claimed.” Authentication accomplished by providing proof of identity.
Authentication can be Single-Factor or Multi-Factor (MFA). If only one of following methods is used in authentication operation, then these operation is a Single-factor authentication.
There are three factor. A covered entity may:
- Require something known only to that individual, such as a password or PIN.
- Require something that individuals possess, such as a smart card, a token, or a key.
- Require something unique to the individual such as a biometric. Examples of biometrics include fingerprints, voice patterns, facial patterns or iris patterns.
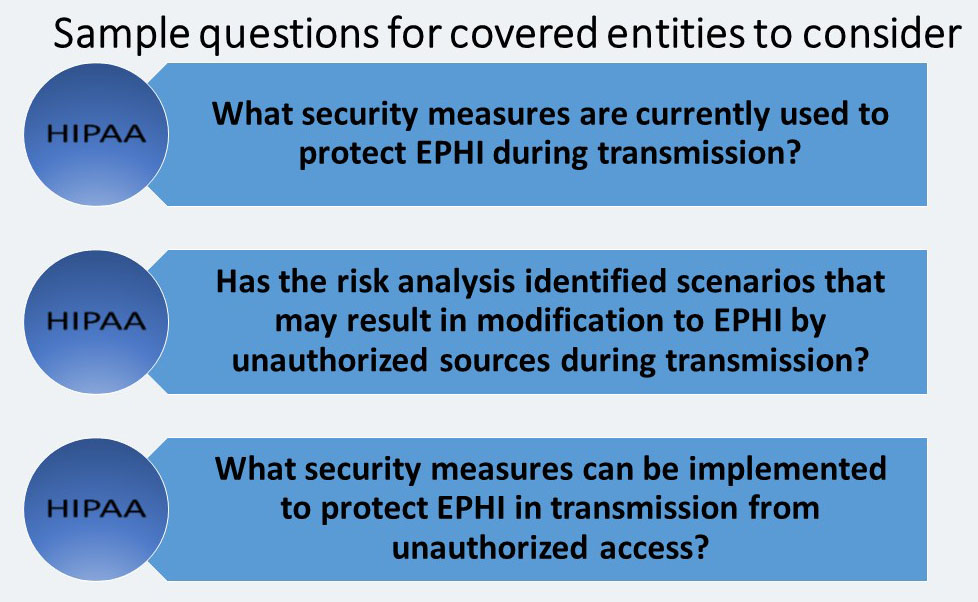
Transmission Security – STANDARD § 164.312(e) (1)
This standard requires a covered entity to: “Implement technical security measures to guard against unauthorized access to electronic protected health information that is being transmitted over an electronic communications network.”
For instance, is EPHI transmitted through email, over the Internet, or via some form of private or point-to-point network? The Security Rule allows for EPHI to be sent over an electronic open network as long as it is adequately protected. Finally, the covered entity must identify the available and appropriate means to protect EPHI as it is transmitted, select appropriate solutions, and document its decisions.
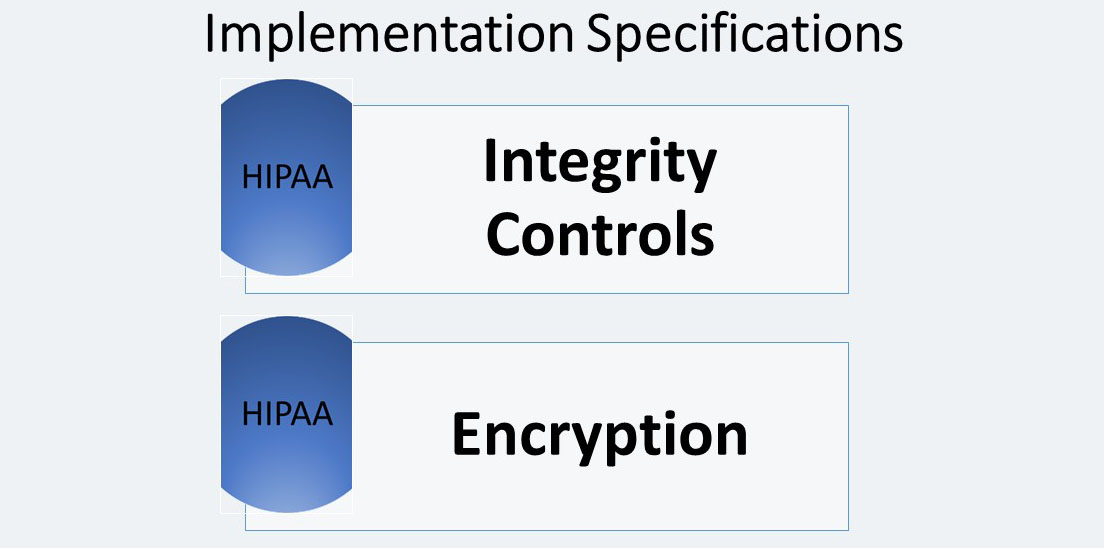
Integrity Controls (A)
A covered entity must: “Implement security measures to ensure that electronically transmitted electronic protected health information is not improperly modified without detection until disposed of.”
A primary method for protecting the integrity of EPHI being transmitted is through the use of network communications protocols. In general, these protocols, among other things, ensure that the data sent is the same as the data received.
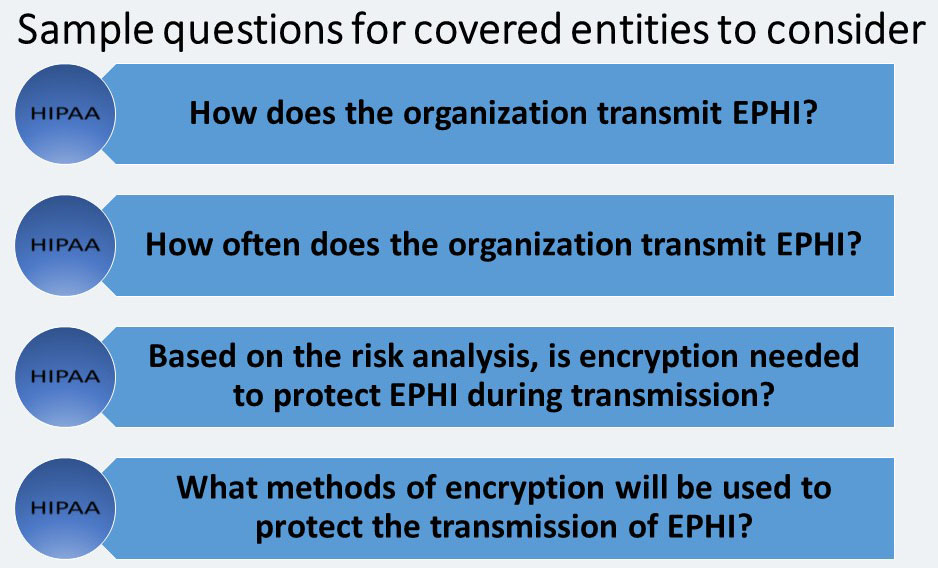
Encryption (A)
A covered entity, the covered entity must: “Implement a mechanism to encrypt electronic protected health information whenever deemed appropriate.”
Adopting a single industry-wide encryption standard in the Security Rule would likely have placed too high a financial and technical burden on many covered entities. The Security Rule allows covered entities the flexibility to determine when, with whom, and what method of encryption to use. Covered entities must consider the use of encryption for transmitting EPHI, particularly over the Internet. Where risk analysis shows such risk to be significant, a covered entity must encrypt those transmissions under the addressable implementation specification for encryption.
—————————–
Source:
This article is a summary from of the hhs.gov website. With the following link:
Security Standards: Technical Safeguards
For more info please refer to hhs.gov



















