In this post we are going to talk about Implementation for the Small Provider. This post is the seventh post in the HIPAA series. This series of posts is called the HIPAA Series.
The series will contain seven post:
- Security 101 for Covered Entities
- Security Standards: Administrative Safeguards
- Security Standards: Physical Safeguards
- Security Standards: technical Safeguards
- Security Standards- Organizational, Policies and Procedures and Documentation Requirements
- Basics of Risk Analysis and Risk Management
- Implementation for the Small Provider
But this series also has two spin offs. We suggest that if you do not have basic information about HIPAA, before starting this series, first read the following two posts:
Note, In across of this post:
(R)= Required, (A)= Addressable
—————————–
Source:
This article is a summary from of the hhs.gov website. With the following link:
Security Standards: Implementation for the Small Provider
For more info please refer to hhs.gov
Implementation for the Small Provider
Identity theft, stolen computer disks, malfunctioning computers, hackers, and other preventable losses of information – these are just a few of the hazards facing all businesses that receive, store, and transmit data in electronic form. Many health care providers too face these same hazards. Providers face major problems if their patient’s sensitive information is stolen, misused, or unavailable.
Small providers that are covered entities have unique business and technical environments that provide both opportunities and challenges related to compliance with the Security Rule.
As such, this post provides general guidance to providers such as physicians and dentists in solo or small group practices, small clinics, independent pharmacies, and others who may be less likely to have IT staff and whose approach to compliance.
The objectives of this post are to:
- Help small providers understand the Security Rule standards, implementation specifications, and requirements as they relate to their organization.
- Provide sample questions and scenarios that small providers may want to consider when addressing the Security Rule requirements.
- Reference industry resources that provide additional information regarding compliance with the Security Rule.
To understand the requirements of the Security Rule, it is helpful to be familiar with the basic concepts that comprise the security standards and implementation specifications. The Security Rule is divided into six main sections – each representing a set of standards and implementation specifications that must be addressed by all covered entities. Each Security Rule standard is a requirement: a covered entity must comply with all of the standards of the Security Rule with respect to the EPHI it creates, transmits or maintains.
Many of the standards contain implementation specifications but where there is no implementation specification for a particular standard, compliance with the standard itself is required.
- A required implementation specification is similar to a standard, in that a covered entity must comply with it. For example, all covered entities including small providers must conduct a “Risk Analysis”.
- For addressable implementation specifications, covered entities must perform an assessment to determine whether the specification is a reasonable and appropriate safeguard in the covered entity’s environment. After performing the assessment, a covered entity decides if it will implement the addressable implementation specification;
- Factors that determine what is “reasonable” and “appropriate” include cost, size, technical infrastructure and resources. While cost is one factor entities must consider in determining whether to implement a particular security measure, some appropriate measure must be implemented. An addressable implementation specification is not optional.
- Administrative Safeguards: These provisions are defined in the Security Rule as the “administrative actions, policies, and procedures to manage the selection, development, implementation, and maintenance of security measures to protect electronic protected health information and to manage the conduct of the covered entity’s workforce in relation to the protection of that information.”
Standards Implementation for the Small Provider includes eleven standards. We discuss about all of them. These standards include:
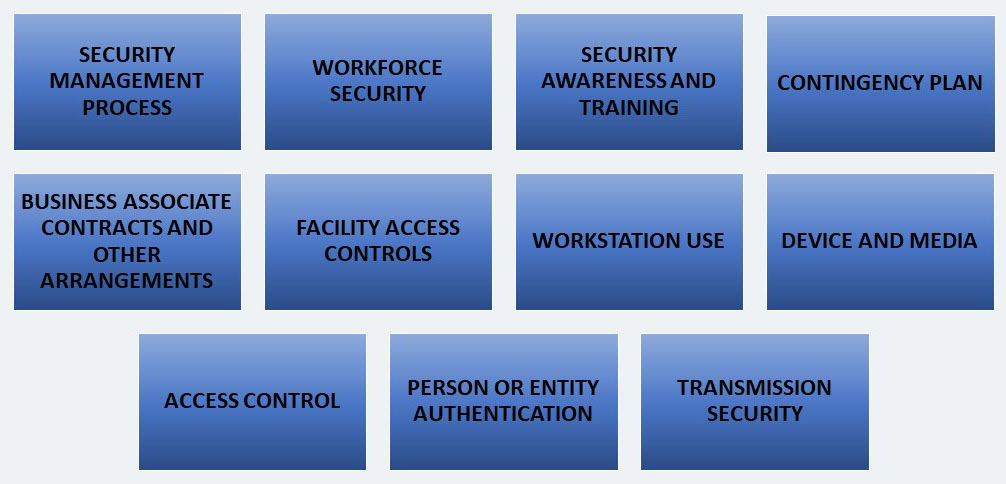
SECURITY MANAGEMENT PROCESS § 164.308(a) (1)
A small provider must “Implement policies and procedures to prevent, detect, contain and correct security violations.”
- Risk Analysis (R): A small provider must “Conduct an accurate and thorough assessment of the potential risks and vulnerabilities to the confidentiality, integrity, and availability of electronic protected health information held by the covered entity.”
- Risk Management (R): A small provider must “Implement security measures sufficient to reduce risks and vulnerabilities to a reasonable and appropriate level to comply with §164.306(a).”
- Sanction Policy (R): The small provider must “Apply appropriate sanctions against workforce members who fail to comply with the security policies and procedures of the covered entity.”

WORKFORCE SECURITY § 164.308(a) (3)(i)
A small provider must “Implement policies and procedures to ensure that all members of its workforce have appropriate access to electronic protected health information, and to prevent those workforce members who do not have access from obtaining access to electronic protected health information.”
- Authorization and/or Supervision (A): A small provider must “Implement procedures for the authorization and/or supervision of workforce members who work with electronic protected health information or in locations where it might be accessed.”

SECURITY AWARENESS AND TRAINING § 164.308(a) (5) (i)
A small provider must “Implement a security awareness and training program for all members of its workforce (including management).”
- Password Management (A): The Small provider must “Implement procedures for creating, changing, and safeguarding passwords.”

CONTINGENCY PLAN § 164.308(a) (7) (i)
A small provider must “Establish (and implement as needed) policies and procedures for responding to an emergency or other occurrence (for example, fire, vandalism, system failure, and natural disaster) that damages systems that contain electronic protected health information.”
- Data Backup Plan (R): The small provider must “Establish and implement procedures to create and maintain retrievable exact copies of electronic protected health information.”

BUSINESS ASSOCIATE CONTRACTS AND OTHER ARRANGEMENTS § 164.308(b) (1)
The small provider “A covered entity may permit a business associate to create, receive, maintain, or transmit electronic protected health information on the covered entity’s behalf only if the covered entity obtains satisfactory assurances that the business associate will appropriately safeguard the information.”
- Written Contract or Other Arrangements (R): A small provider “Document the satisfactory assurances required by this section through a written contract or other arrangement with the business associate that meets the applicable requirements of §164.314(a) [(the Business Associate Contracts or Other Arrangements Standard)].”

FACILITY ACCESS CONTROLS § 164.310(a) (1)
The small provider must “Implement policies and procedures to limit physical access to its electronic information systems and the facility or facilities in which they are housed, while ensuring that properly authorized access is allowed.”
- Facility Security Plan (A): A small provider “Implement policies and procedures to safeguard the facility and the equipment therein from unauthorized physical access, tampering, and theft.”
- Maintenance Records (A): A small provider must “Implement policies and procedures to document repairs and modifications to the physical components of a facility which are related to security (for example, hardware, walls, doors and locks).”

WORKSTATION USE § 164.310(b)
The small provider must “Implement policies and procedures that specify the proper functions to be performed, the manner in which those functions are to be performed, and the physical attributes of the surroundings of a specific workstation or class of workstation that can access electronic protected health information.”

DEVICE AND MEDIA CONTROLS § 164.310(d) (1)
The small provider must “Implement policies and procedures that govern the receipt and removal of hardware and electronic media that contain electronic protected health information into and out of a facility, and the movement of these items within the facility.”
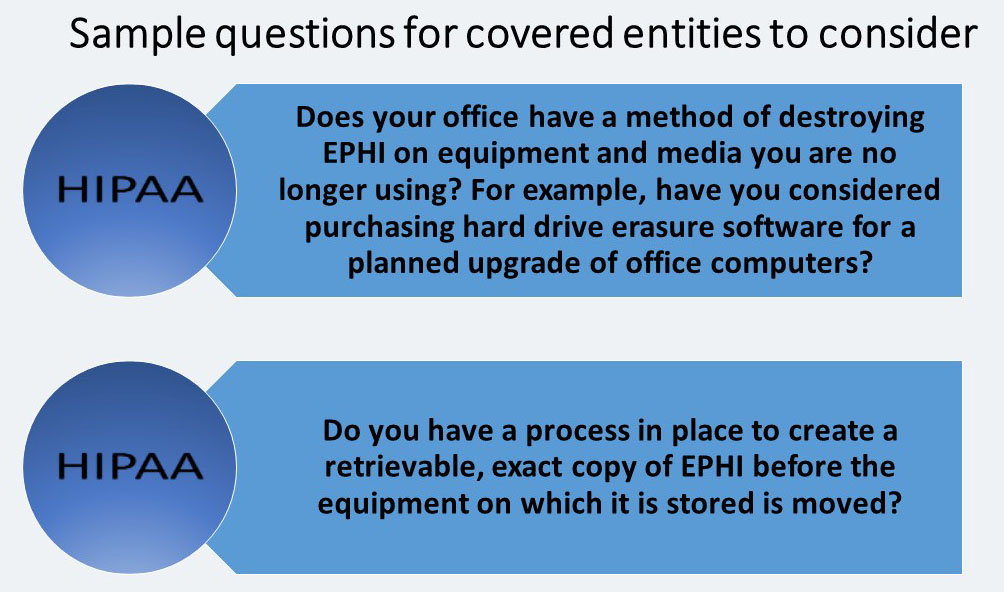
- Disposal (R): A small provider must “Implement policies and procedures to address the final disposition of electronic protected health information, and/or the hardware or electronic media on which it is stored.”
- Data Backup and Storage (A): A small provider must “Create a retrievable, exact copy of electronic protected health information, when needed, before movement of equipment.”
ACCESS CONTROL § 164.312(a) (1)
The small provider must “Implement technical policies and procedures for electronic information systems that maintain electronic protected health information to allow access only to those persons or software programs that have been granted access rights as specified in § 164.308(a)(4)) [(Information Access Management)].”
- Unique User Identification (R): A small provider must “Assign a unique name and/or number for identifying and tracking user identity.”
- Automatic Logoff (A): A small provider must “Implement electronic procedures that terminate an electronic session after a predetermined time of inactivity.”

PERSON OR ENTITY AUTHENTICATION § 164.312(d)
The small provider must “Implement procedures to verify that a person or entity seeking access to electronic protected health information is the one claimed.”

TRANSMISSION SECURITY § 164.312(e) (1)
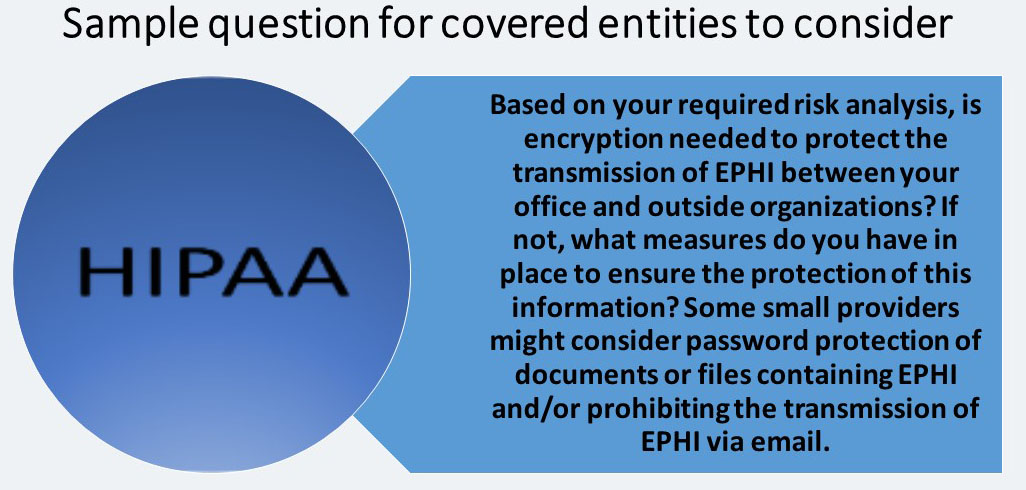
The small provider must “Implement technical security measures to guard against unauthorized access to electronic protected health information that is being transmitted over an electronic communications network.”
- Encryption (A): A small provider must “Implement a mechanism to encrypt electronic protected health information whenever deemed appropriate.”
—————————–
Source:
This article is a summary from of the hhs.gov website. With the following link:
Security Standards: Implementation for the Small Provider
For more info please refer to hhs.gov



















