Computer Networking
We have been supporting tens of computer networks and businesses during decades of experience in computer networking realm. Our clients range from variety of business sectors, Medical offices, College camps, Factories, Small business and retail stores to enterprise businesses like car rentals and hospitals.
Computer Networking Solutions
ITperfection offers wide variety of solutions for your networking needs, if you have a small business, or your company has several sites and branch offices, covering thousands of client computers; we can help you with your networking needs.
Certifications
We are certified IT professionals with a wide variety of certifications from industry standard companies like, Microsoft, Cisco and …
ITPerfection Blog
Here you can find a wide variety of blogs relating to Computer Networking, IT security, IT Training, Cyber security, Backup and Disaster recovery, Data protection and ….
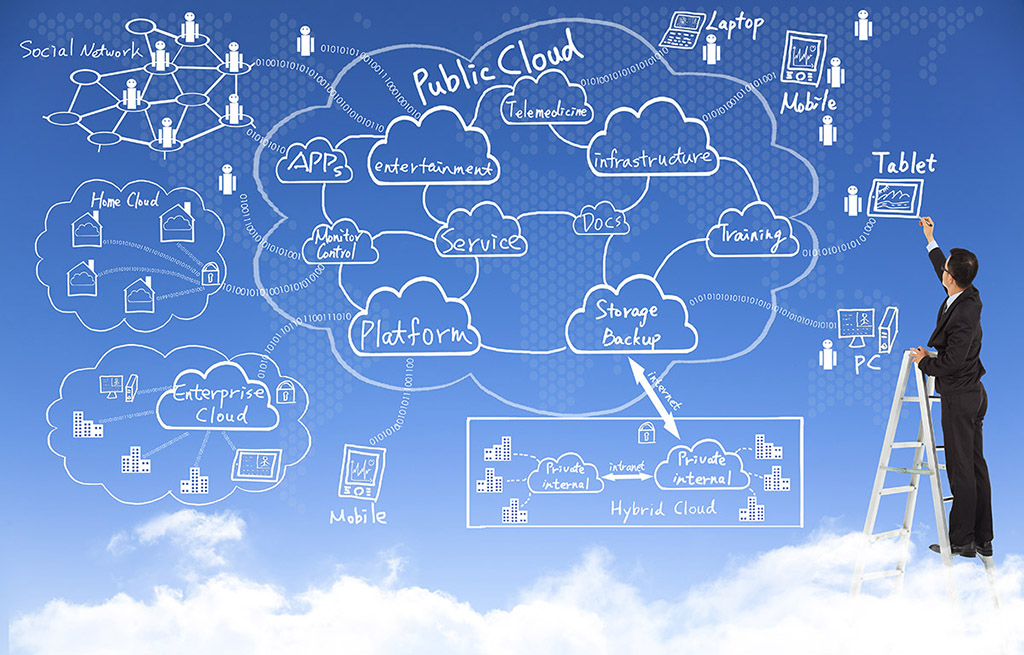
All Things About Public Cloud Services
First of all, we need to know a little bit about the concept of "public cloud services" or "as s service". The term "cloud services" refers to a wide range of services delivered on demand to companies and customers over the internet and in fact, it refers to a broad category that encompasses the myriad IT resources provided over the internet. What's "as a service"? "as a service" refers to [...]
Offsite Backup
No matter how efficient a computer system appears to be, there is always the possibility of a malfunction wiping out valuable data. For this reason, many companies have set up backup systems, designed to recover lost data. It is very important that an organization have at least two backup. a backup in local (onsite backup) and another in a remote location (offsite backup). Off-site backup is a method of [...]
Step by Step Malware Removal
This post is dedicated to malware removal. In this post we are going to tell you how you can find out that your computer has been the victim of malware. Then learn what to do if malware is on your computer. Finally, we have some important security solutions for you that if you use them, you will greatly reduce the chances of your computer being infected with malware. But [...]
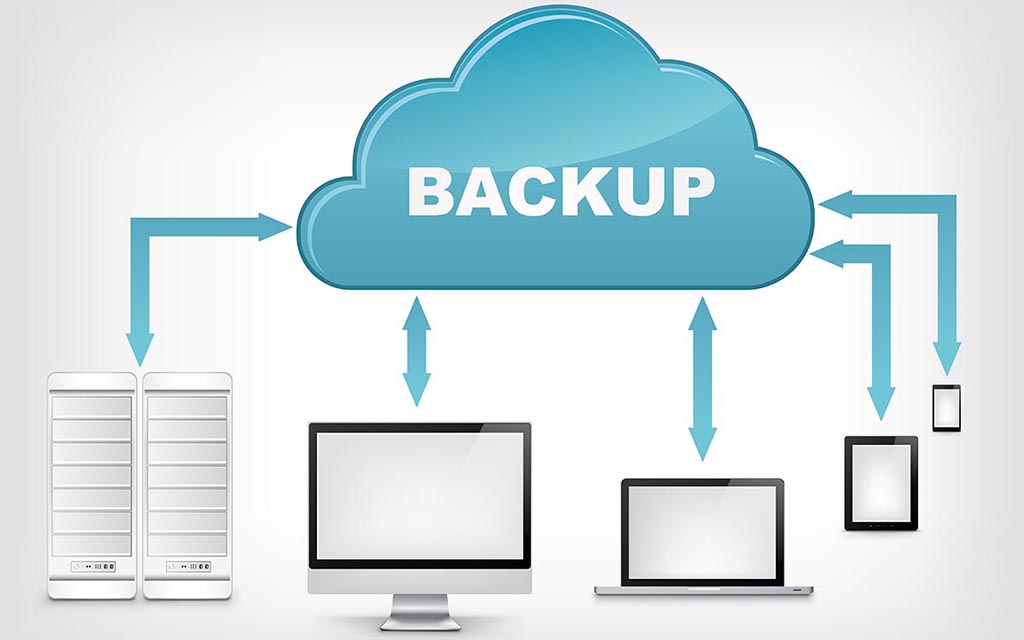
Cloud Backup Solutions
In this post, we'll talk a little bit about cloud backup solution. About how cloud backup works? How to restore data from cloud backup? What methods can cloud backup be used for? What are the benefits of using cloud backup? Also we'll talk a little bit about cloud backup solutions. What's Cloud Backup Solution? Cloud backup (or cloud computer backup, or online backup, or remote backup) refers [...]
How To Document BCP?
It is a good idea to read this post first about resuscitation as well as job continuity. As you can see, the process of business continuity involves several steps. In the fifth stage, called "BCP Implementation", one of important things that needs to be done is to document the business continuity plan (BCP). We discuss this topic in this post. BCP is a process that addresses the continuation of [...]
Hardware Firewalls
Previously; We wrote an article as “All Things about Firewalls" earlier. Now, we want to discuss more about hardware firewalls. A hardware firewall is a physical device similar to a server that filters traffic to a computer. Hardware firewall has processor, memory, and sophisticated software, powerful networking components (hardware and software) and force all traffic traversing that connection to be inspected by configurable rule sets which grant or deny [...]
What’s PCI DSS?
The Payment Card Industry Data Security Standard (PCI DSS) is a set of security standards for organizations that handle branded credit cards. The PCI DSS applies to ANY organization that accepts, transmits or stores any cardholder data. The PCI Standard is administered by the Payment Card Industry Security Standards Council. This Council’s mission is to enhance global payment account data security. PCI DSS was created to increase controls around cardholder [...]
Server virtualization
Computer network administrators usually dedicate each server to a specific application or task. In most cases each application / task needs its own dedicated machine. There are a couple of problems with this approach, though. One is that it doesn't take advantage of modern server computers' processing power. Many of these servers sit idle as the workload is distributed to only some of the servers on the network. Another problem [...]