Network & Data Security
Do you have an active security plan for your network? Are you required to comply with any compliance such as HIPAA and PCI rules? Have you ever asked your IT service provider about the security of your network? Do you need help with applying newest security strategies to your network?
ITperfection helps you with your network security needs
Our experts, with decades of experience, while holding industry-standard certifications and qualifications, are ready to help you with the security of your network. We at ITperfection, are here to help you from the easiest setups, installations, configurations of the networks; to the highest and most complicated implementations of security, System Vulnerability scans, Penetration tests, performance monitoring, Forensic discoveries and ….
Certifications
We are certified IT professionals with a wide variety of certifications from industry standard companies like, Microsoft, Cisco and …
ITPerfection Blog
Here you can find a wide variety of blogs relating to Computer Networking, IT security, IT Training, Cyber security, Backup and Disaster recovery, Data protection and ….
Authentication Methods
Authentication is the process of verifying the identity of a person or device. In fact, Authentication technology provides access control for systems by checking to see if a user's credentials match the credentials in a database of authorized users or in a data authentication server. The authentication process always runs at the start of the application, before the permission and throttling checks occur, and before any other code is [...]
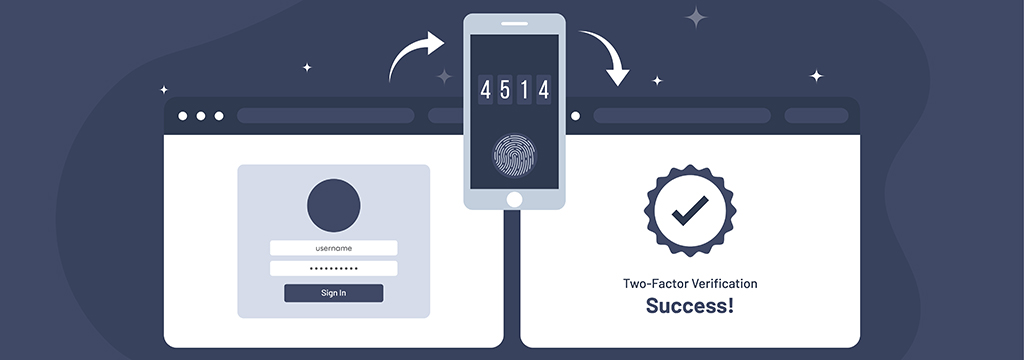
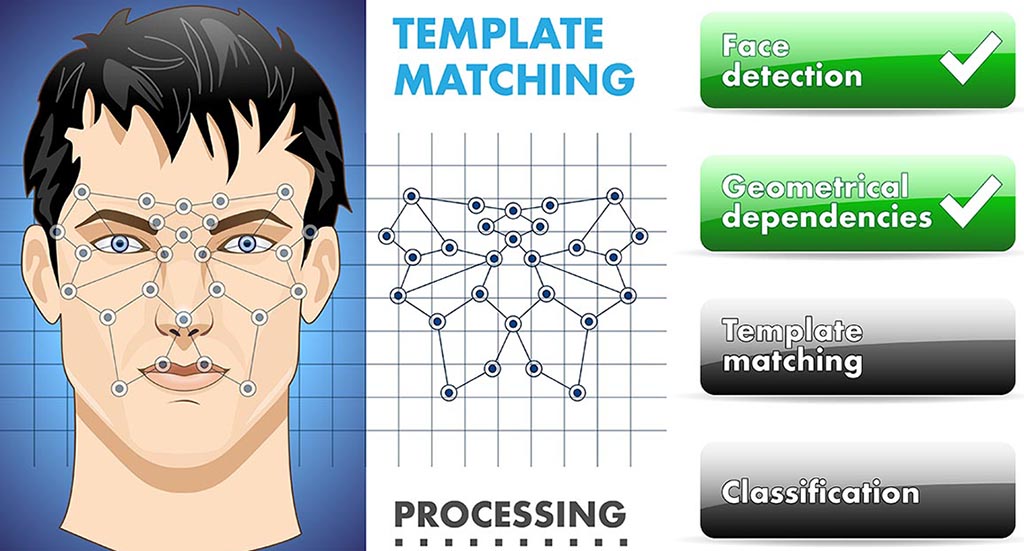
Biometric Authentication Methods
In recent years, issues such as Multi-Factor Authentication (MFA) and Biometric Authentication have become more common due to problems in traditional authentication methods. In fact, biometric methods can be considered a subset of MFA. In this post, we take a look at the most common methods used in biometric authentication. There are a number of advantages to this technology: Biometric identification can provide extremely accurate, secured access to information. [...]
HIPAA Compliance
The Health Insurance Portability And Accountability Act (HIPAA) a legislation which provides security provisions and data privacy, in order to keep patients’ medical information safe. The law has emerged into greater prominence in recent years with the proliferation of health data breaches caused by cyberattacks and ransomware attacks on health insurers and providers. It's good to know that HIPAA compliance has a close relationship with PCI DSS. So, companies [...]
E-mail Encryption
E-mail encryption is one of the most important aspects of security in organizational networks, personal use, and the Internet. By default, email messages are not secure. They are sent across the Internet in plain text. Hackers who gain unauthorized access to an email account can access attachments, content, and even hijack your entire email account. We have already written a post about data encryption. You might want to take [...]
Securely Transfer Files
We, as individuals or organizations, often need to securely transfer files over the Internet to another person or organization on the Internet. In this post, we will try to get acquainted with the common solutions for this purpose and examine these file transfer methods from a security point of view. Sending a file over the Internet also can be considered a kind of file sharing. File sharing is public [...]
What’s GDPR?
General Data Protection Regulation (GDPR) is a regulation that requires businesses to protect the personal data and privacy of EU citizens for transactions that occur within EU member states. This regulation aims to simplify the regulatory environment for business so both citizens and businesses in the European Union can fully benefit from the digital economy. This regulation agreed upon by the European Parliament and Council in April 2016. Source: [...]
Data Encryption
Data encryption translates data into another form, or code, so that only people with access to a decryption key or password can read it. Today, encryption is widely used on the internal networks and internet to ensure the sanctity of user information (such as payment data or personal information) that's sent between a browser and a server. Strong encryption solutions combined with effective key management protect sensitive data from unauthorized access, [...]
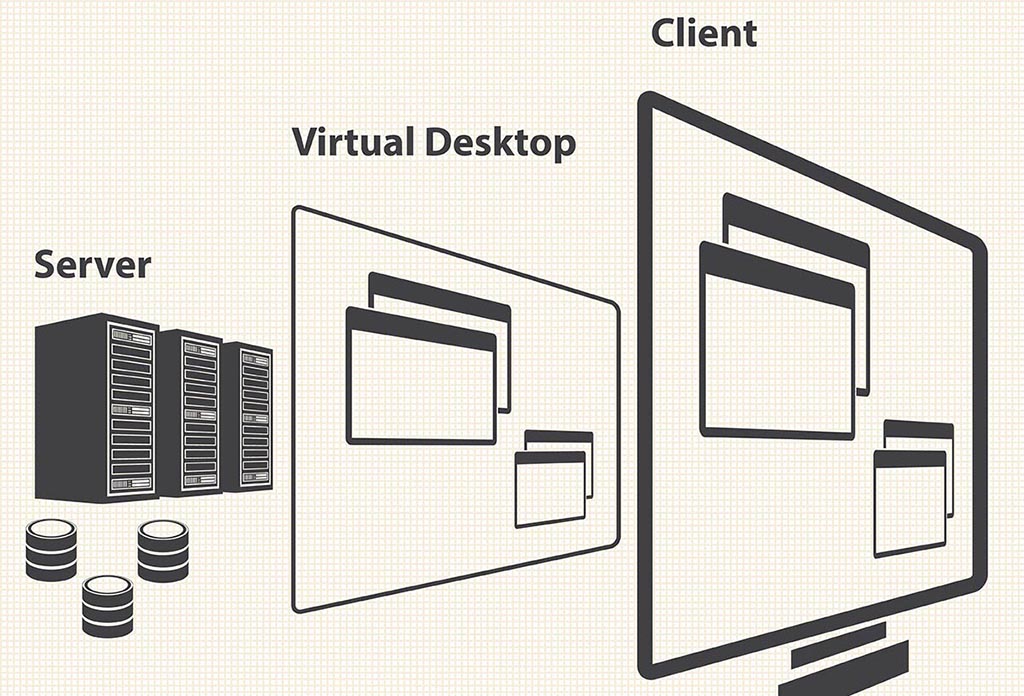
What’s VDI?
Virtual desktop infrastructure (VDI) is defined as the hosting of desktop environments on a central server. In fact, VDI is a desktop virtualization technology wherein a desktop operating system (OS) - typically Microsoft Windows - runs and is managed in an on-premises or cloud data center. The virtual desktop image is delivered over a network to an endpoint device, which may be a traditional PC, thin client device or [...]
IPS and IDS
Intrusion detection is the process of monitoring the events occurring in network and analyzing them for signs of possible incidents, violations, or imminent threats to security policies. These security measures are available as intrusion detection systems (IDS) and intrusion prevention systems (IPS). At result, IDS and IPS are both parts of the network infrastructure. IDS and IPS constantly monitor network, identifying possible incidents and logging information about them, stopping the [...]