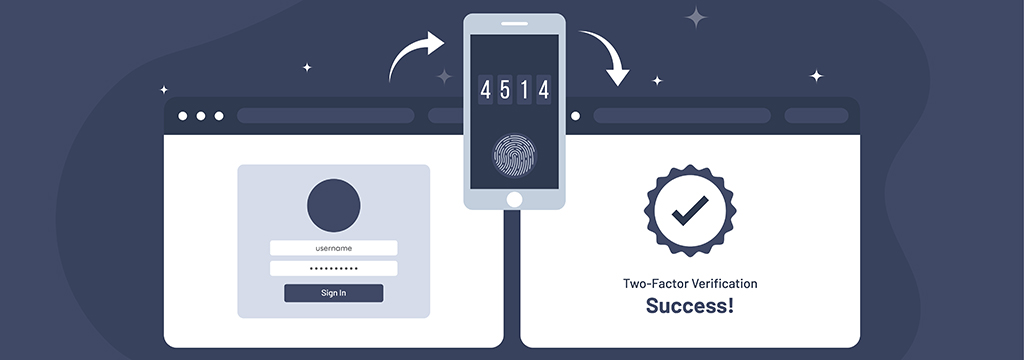
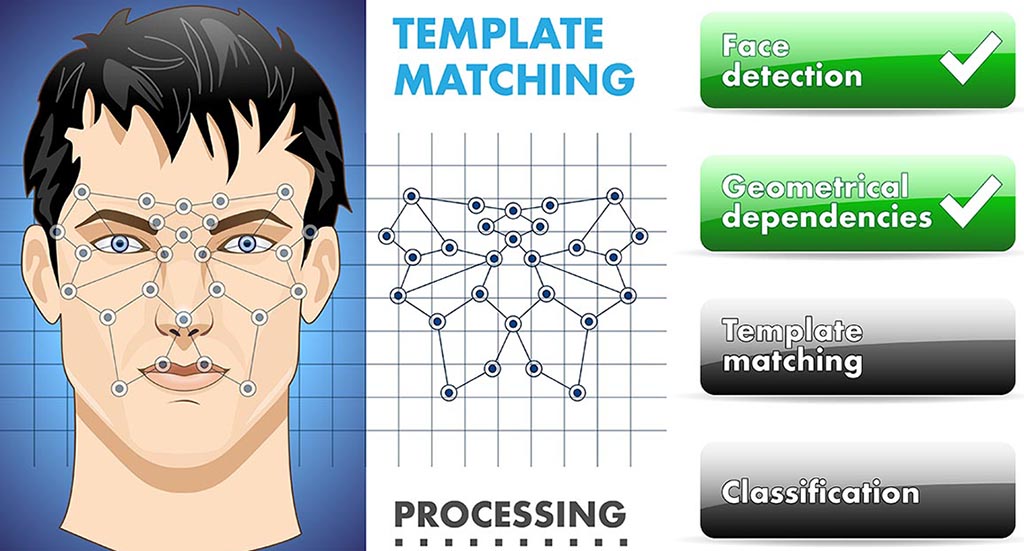
Authentication Methods
Authentication is the process of verifying the identity of a person or device. In fact, Authentication technology provides access control for systems by checking to see if a user's credentials match the credentials in a database of authorized users or in a data authentication server. The authentication process always runs at the start of the [...]