Network & Data Security
Do you have an active security plan for your network? Are you required to comply with any compliance such as HIPAA and PCI rules? Have you ever asked your IT service provider about the security of your network? Do you need help with applying newest security strategies to your network?
ITperfection helps you with your network security needs
Our experts, with decades of experience, while holding industry-standard certifications and qualifications, are ready to help you with the security of your network. We at ITperfection, are here to help you from the easiest setups, installations, configurations of the networks; to the highest and most complicated implementations of security, System Vulnerability scans, Penetration tests, performance monitoring, Forensic discoveries and ….
Certifications
We are certified IT professionals with a wide variety of certifications from industry standard companies like, Microsoft, Cisco and …
ITPerfection Blog
Here you can find a wide variety of blogs relating to Computer Networking, IT security, IT Training, Cyber security, Backup and Disaster recovery, Data protection and ….
Microsoft 365
First of all, it should be noted that in preparing this article, we have used a lot of contents from the microsoft.com website. Sometimes we have copied and pasted the contents, in most cases we have summarized the contents, and sometimes, of course, we have written our own interpretation of that contents. We hope this post about Microsoft 365 is useful to you. Microsoft365 is the new name for [...]
Password Managers
Why is it recommended to use password managers? These days, every new website and application we sign up for is another password we have to remember. In fact, the number of passwords we need to remember is so high that we may forget all or part of them. If we write down passwords in a file or on paper, which is very dangerous in terms of security. Aside from [...]
Veeam Backup & Replication
First of all, it should be noted that in preparing this post, we have used a lot of contents from the veeam website help center. Sometimes we have copied and pasted the article, in most cases we have summarized the article, and sometimes, of course, we have written our own interpretation of that content. We hope this post about Veeam Backup & Replication is useful to you. Veeam Backup [...]
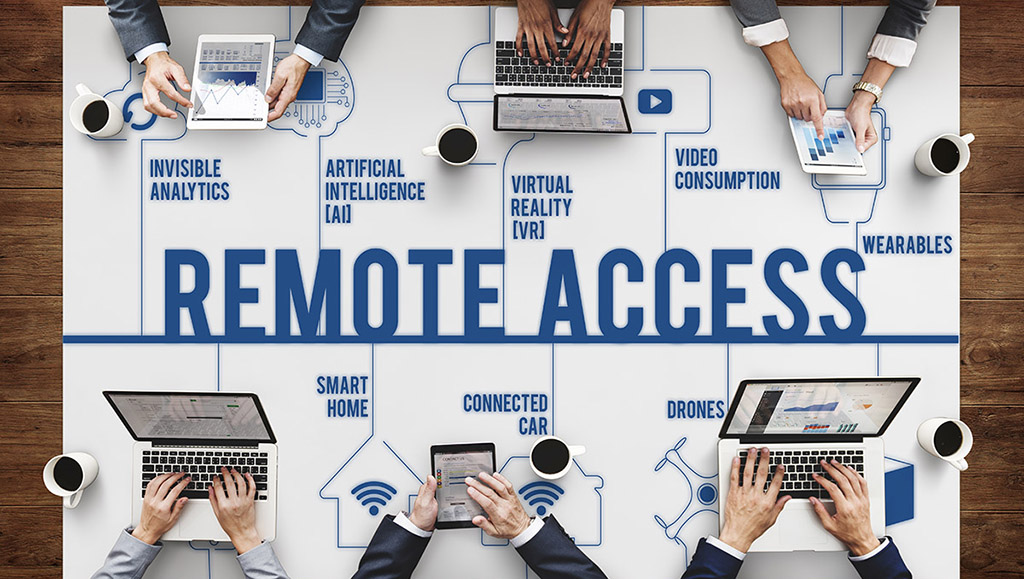
Secure Remote Access
Remote access is the ability to access your computer from a remote location. In fact, Remote access is simply the ability to access a computer or network, at home or in an office, from a remote location. Remote access connection allows users to access a network or computer remotely via an internet connection or telecommunications. This post is dedicated to secure remote access. You can use a local area [...]
Social Engineering Attacks
Social engineering attacks are more prevalent than most people think. The reason for their prevalence is that they are relatively easy to implement. Social engineering is the term used for a broad range of malicious activities accomplished through human interactions. People are weakest link in the security chain, and in recent years hackers have be increasingly using social engineering techniques to exploit the people. In fact, an attacker attempts to [...]
Information Security Concepts
This post provides some information on the concept of security, the concept of security in the network, the concept of security threats and their types. Security Risk A computer security risk is the potential for loss, damage or destruction of an asset as a result of a threat exploiting a vulnerability. In other words, a computer security risk is really anything on your computer that may damage [...]
Phishing Attacks
Phishing is a type of social engineering attack often used to steal user data, including login credentials and credit card numbers. There is another definition for this attack. We can say Phishing is the fraudulent use of electronic communications to deceive and take advantage of users. Phishing attacks attempt to gain sensitive, confidential information such as usernames, passwords, credit card information, network credentials, and more. In a phishing email attack, an [...]
All Things About Firewall
A network firewall is a network security device that monitors incoming and outgoing network traffic. Firewalls are a first line of defense in network security. Firewall purpose is to establish a barrier between your internal network and incoming traffic from external sources (such as the internet) in order to block malicious traffic like viruses and hackers. How Does A Firewall Work? Firewall uses many rules that they [...]
Malware and its variants
In this article, we want to introduce you to different types of malware. First we need to see what the word malware itself means. Malware is actually abbreviated to "malicious software", and it's actually a name used to refer to all viruses, all worms, all spyware, all Trojans, and any malicious computer program. So, Malware refers to any software that is designed specifically to disrupt, damage, steal, spy or in any [...]