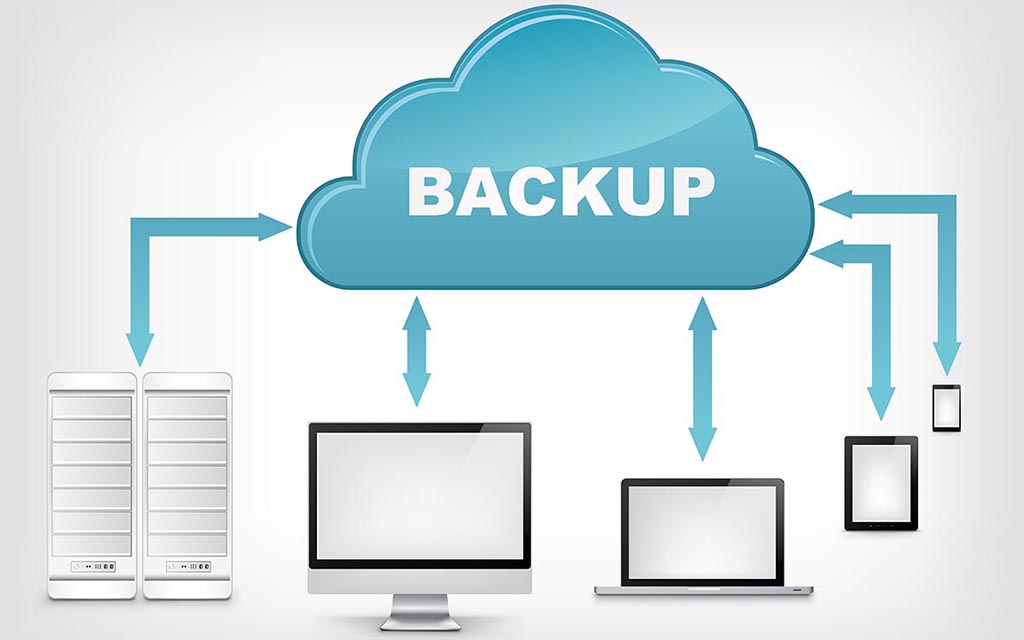
Cloud Backup Solutions
In this post, we'll talk a little bit about cloud backup solution. About how cloud backup works? How to restore data from cloud backup? What methods can cloud backup be used for? What are the benefits of using cloud backup? Also we'll talk a little bit about cloud backup solutions. What's Cloud Backup [...]