OSI Model
One of the most important topics in all networking courses is OSI model. Communication between computers over public or private networks is made possible by using different protocols. A protocol is a set of rules and limitations that define how data is transmitted over a medium such as a wired medium or a wireless transmission medium. Of course, in addition to OSI, there is another architectural model called TCP/IP.
Initially, each company used its own protocols, which caused many problems in the connection between the computers of different companies. As a result, the International Organization for Standardization (ISO) developed the Open Systems Interconnection (OSI) Reference Model for protocols in the 1984 year.
The OSI model is helpful for explaining complex networking topics. For this reason, much of the information you need to know for the Communication and Network Security domain is presented in this chapter in the context of the OSI model.
This model is actually a seven-layer architecture as described below. Layer number seven is at the top of this stack model, and layer number one is the lowest layer.
This model is actually a seven-layer architecture as described below. Layer number seven is at the top of this stack model, and layer number one is the lowest layer. In this model, each layer is responsible for performing specific tasks or operations for the ultimate goal of supporting network communication between two computers.
The figure below shows how this model works. In this scenario, suppose that a user on the source network, sends a packet of information for a user on the destination network. Assuming that this package belongs to a software, the above information package, starts moving from layer seven of the source network. According to the direction of the brown arrow, layer by layer comes down. In each layer, information is added to the header of this package. (According to the task of each layer). It finally reaches the physical layer, where everything is in the form of 0s and 1s signals. (Machine language) The physical layer is connected to the transmission medium. Therefore, the above package is placed on the transmission medium and reaches the physical layer (layer number one) of the destination network by the above medium. Here it starts moving from layer one. This time upwards. In each layer, Information in the header fields, is examined until it finally reaches layer seven (application layer) of the destination network and the destination user.
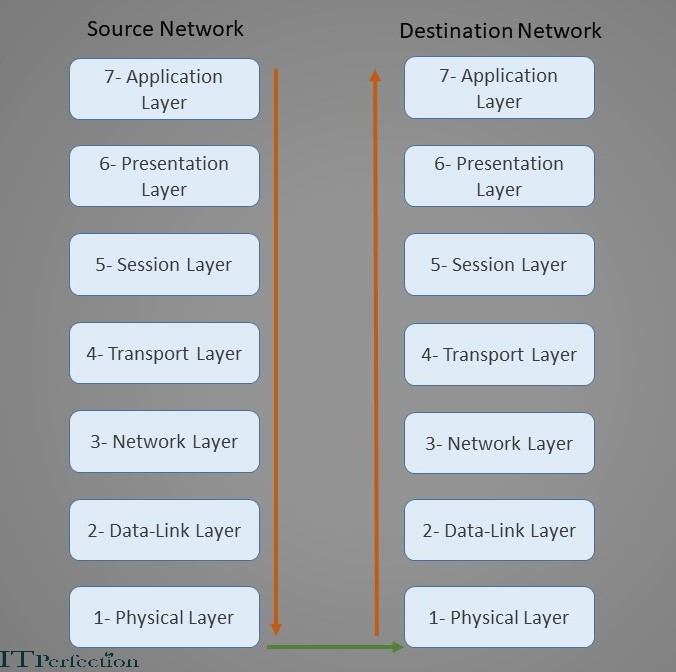
Now it’s time to look at what each layer does and how it does it. What mechanisms does it use? Each layer has its own protocols. We will examine the protocols of each layer. Let’s go!
Physical Layer (Layer-1)
The Physical Layer sends and receives bits across the network medium (cabling or wireless links) from one device to another.
In other words, the Physical layer of the OSI model is responsible for receiving bits from the physical medium and converting them into a frame to be used by the Data Link layer. It is also responsible for accepting frames from the Data Link layer and converting them into bits for transmission over the physical connection medium.
Various network topologies, made from copper or fiber-optic wires and cables, Interface Cards (NICs), repeaters, hubs, concentrators, and other physical materials, comprise the Physical Layer.
Data Link Layer (Layer-2)
Data-link Layer formats messages from layers above into frames for transmission, handles point-to-point synchronization and error control, and can perform link encryption.
This layer is responsible for formatting the packet from the Network layer into the proper format for transmission, and also defines the networking protocol (for example, Ethernet, and token ring).
The IEEE 802 standards and protocols divide the Data Link Layer into two sub-layers:
- Logical Link Control (LLC)
- Media Access Control (MAC)
The following list includes some of the protocols initiated within the Data Link layer:
- Point-to-Point Protocol (PPP)
- Address Resolution Protocol (ARP)
- Layer 2 Forwarding (L2F)
- Layer 2 Tunneling Protocol (L2TP)
- Point-to-Point Tunneling Protocol (PPTP)
- Integrated Services Digital Network (ISDN)
The function performed on the data within the Data Link layer includes adding the source and destination MAC addresses to the frame.
————————————————————–
The Media Access Control (MAC) address has a 48-bit (6-byte) hexadecimal representation, 24 bits represent the vendor or manufacturer of the physical network interface. The remaining 24 bit represent a unique number assigned to that interface by the manufacturer.
——————————————————-
Switches and bridges operate at the Data Link layer and these devices support MAC-based traffic routing. Switches receive a frame on one port and send it out from another port based on the destination MAC address. MAC address destinations are used to determine whether a frame is transferred over the bridge from one network to another.
Read More:
- Network Topologies
- Logical Link Control (LLC)
- Media Access Control (MAC)
- Ethernet
- Token Ring
- MAC Address
Network Layer (Layer-3)
The Network Layer provides routing and related functions that enable data to be transported between systems on the same network or on interconnected networks (or internetworks).
The Network layer accepts the segment from the Transport layer and adds information to it to create a packet. The packet includes the source and destination IP addresses.
This layer also manages error detection and data traffic control.
The routing protocols are placed at this layer and include the following:
- Internet Control Message Protocol (ICMP)
- Routing Information Protocol (RIP)
- Open Shortest Path First (OSPF)
- Border Gateway Protocol (BGP)
- Internet Group Management Protocol (IGMP)
- Internet Protocol (IP)
- Internet Protocol Security (IPSec)
- Inter-network Packet Exchange (IPX)
Network hardware devices that operate at the network layer include Router and Bridge routers (B-Routers). Routers determine the best logical path for the transmission of packets based on speed, hops, preference, and so on. Routers use the destination IP address to lead the transmission of packets.
Internet Protocol (IP) contains addressing information that enables packets to be routed. IP is part of the TCP/IP (Transmission Control Protocol/Internet Protocol) suite, which is the language of the Internet. IP has two primary responsibilities:
- Connectionless, best-effort (no guarantee of) delivery of datagrams.
- Fragmentation and reassembly of datagrams.
IP Version 4 (IPv4), which is currently the most commonly used version, uses a 32-bit logical IP address that’s divided into four 8-bit sections (octets) and consists of two main parts: the network number (Net ID) and the host number (Host ID). The first bit in the octet is referred to as the most significant bit, and the last bit in the octet is referred to as the least significant bit.
Each bit position represents its value. If the bit is “on” (1); otherwise, its value is zero (“off” or 0).
Each octet contains an 8-bit number with a value of 0 to 255.
Read More: IPv4 classes and subnetting
IP version 6 (IP v6) uses a 128-bit hexadecimal IP address and incorporates additional functionality to provide security, multimedia support and so on. The main reason for developing IPv6 was to provide infinitely more network addresses than are available with IPv4 addresses.
IPv6 addresses consist of eight blocks separated by a colon.
The basic format for an IPv6 address is:
xxxx:xxxx:xxxx:xxxx:xxxx:xxxx:xxxx:xxxx
Where x represents a hexadecimal digit (0–f).
The following is an example of an IPv6 address:
2001:0db8:1140:0000:0208:0800:200c:4c8a
Transport Layer (Layer-4)
This layer is responsible for managing the integrity of a connection and controlling the session. It accepts a PDU (a container of information or data passed between network layers) from the Session layer and converts it into a segment. The Transport Layer hides the details of the lower layer functions from the upper layers.
This layer includes mechanisms for segmentation, sequencing, error checking, controlling the flow of data, error correction, multiplexing, and network service optimization.
The following protocols operate within the Transport layer:
- Transmission Control Protocol (TCP): A full-duplex and connection-oriented protocol that provides reliable delivery of packets across a network. A connection-oriented protocol requires a direct connection between two communicating devices before any data transfer occurs. The following characteristics and features are associated with TCP: 1- TCP is Connection-oriented. 2- It’s Reliable. 3- TCP is slower than UDP.
- User Datagram Protocol (UDP): A connectionless protocol that provides fast best-effort delivery of datagrams across a network. A connectionless protocol doesn’t guarantee delivery of transmitted packets. Best example of applications that use UDP is streaming audio or video. The following characteristics and features are associated with UDP: 1- It’s connectionless. 2- UDP isn’t reliable. 3- It’s Faster than TCP.
- Sequenced Packet Exchange (SPX): The protocol used to guarantee data delivery in older networks. (Like Novell NetWare).
- Secure Sockets Layer (SSL) / Transport Layer Security (TLS): The SSL/TLS protocol provides session-based encryption and authentication for secure communication between clients and servers.
Session Layer (Layer-5)
This Layer establishes, coordinates, and terminates communication sessions (service requests and service responses) between networked systems. It manages dialogue discipline or dialogue control such as simplex (One-way direction communication), half-duplex (Two-way communication, but can only send data in one direction at a time), full-duplex (Two-way communication, in which data can be sent in both directions simultaneously).
The following protocols operate within the Session layer:
- Network File System (NFS): Developed to facilitate transparent user access to remote resources on a UNIX-based TCP/IP network.
- Session Initiation Protocol (SIP): A signaling protocol for establishing, managing and terminating real-time communications (like voice, video, text) over IP-based networks.
- Remote Procedure Call (RPC): A client-server network redirection tool.
- Network Basic Input/Output System (NetBIOS): It is a Microsoft protocol that allows applications to communicate over a LAN. Today, it can be said that Microsoft systems no longer use this protocol, and DNS has replaced this protocol.
Presentation Layer (Layer-6)
This layer provides coding and conversion functions that are applied to data being presented to the Application Layer. These functions ensure that data sent from the Application Layer of one system are compatible with the Application Layer of the receiving system. The Presentation layer is also responsible for encryption and compression.
In fact, this layer acts as an interface between the network and applications. Most file or data formats operate within this layer. This includes formats for images, videos, sounds, documents, e-mails, web pages ( Like ASCII code, JPEG, MPEG, TIFF),and so on.
Tasks associated with this layer include:
- Data compression: It enable compressed data to be properly decompressed at the destination.
- Data representation: Use of common data representation formats (standard image, sound, and video formats) enable application data to be exchanged between different types of computer systems.
- Data encryption: It enables encrypted data to be properly decrypted at the destination.
- Character conversion: Information is exchanged between different systems by using common character conversion schemes.
Application Layer (Layer-7)
This layer supports the components that deal with the communication aspects of an application that requires network access, and it provides an interface to the user. The Application layer determines whether a remote communication partner is available and accessible. It also ensures that sufficient resources are available to support the requested communications.
Protocols and services required to transmit files, exchange messages, connect to remote terminals, and so on are found here. Many application-specific protocols are found within this layer, such as the following:
Hypertext Transfer Protocol (HTTP)
Simple Network Management Protocol (SNMP)
