Security Concepts
Asset: An asset is anything valuable to an organization. It may vary from tangible items (people, computers) to intangible items (as example Bank accounts, database information). Read more about tangible Items and intangible items
Valuable Information Assets: Security of these assets is an important aspect of information security environment. Greater value assets require more security and as a result, more expense.
CIA Triad: Information Security is based on three main factors (Also Called Information Security Triad). Confidentiality, Integrity and Availability, these are abbreviated as CIA.
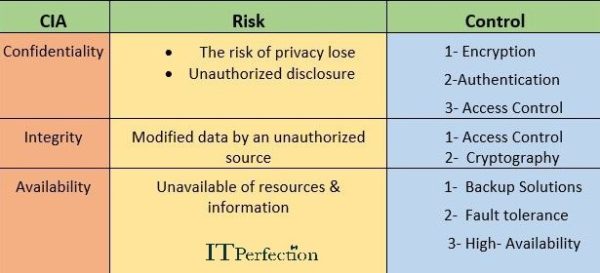
Confidentiality: Assures that data is secured and only authorized people will have access to the data. Confidentiality of data prevents unauthorized read access to data. Data Confidentiality assures that the data will not be disclosed to unauthorized people. Confidentiality, is closely related to privacy as well as personal data.
Personal data most commonly refers to personally identifiable information (PII) or personal health information (PHI). Read about PII and PHI.
The objective of privacy is the confidentiality and proper handling of personal data.
Integrity: If data integrity is maintained, the data will not be modifies by unauthorized people. This prevents unauthorized write access to data.
Availability: Ensures information is available when needed. The Availability assures that the network and data will be available to authorized personnel.
Implementation of Confidentiality: Confidentiality can be implemented using access control & cryptography. Access control has two aspects: Software control and physical control. Cryptography helps to protect from disclosure of information for unauthorized users. The encrypted form of data can only decrypt by the legitimate user to whom data is intended. Another way is to perform authentication operations correctly
Implementation of Integrity: It can be implemented with confidentiality to prevent any unauthorized access leading to access the data & modify. To securely deploy integrity, Hashing / Message digests are required.
Implementation of Availability: There are two main methods to implement this.
- Storing the information in multiple locations
- Configuring fault tolerance
