Security Control Assessment
Security Control Assessment that ensures that the security policies enforced in an organization are meeting their goals and objectives.
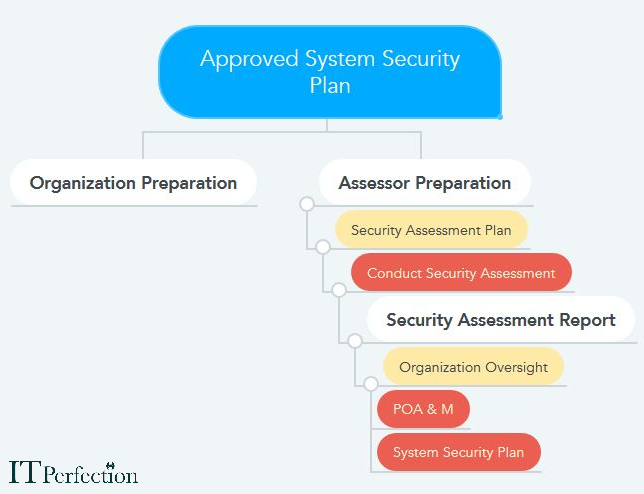
CSA also reports about the quality of risk management processes including incident response action plans.
A well-executed assessment process of security control provides inputs to enhance the running security control, identify the weakness and strength of controls.
Asset Valuation
The value of an asset is calculated in the form of cost or its perceived value to an organization either internally or externally.
Methods of Valuation There are two types of information valuation methods, which are as follows:
- Subjective Method: the value of an asset is determined by the important individual actions places on it. Subjective methods include the creation, dissemination, and collection of data from checklists or surveys.
- Objective Method: Objective valuation is a metric or statistical measure, which are based on specific quantitative measurements as opposed to qualitative.
Tangible Asset Valuation
Tangible assets are the physical assets; hence, these assets are valued by subtracting depreciation from the original cost.
Following parameters are considered to estimate the value of tangible assets:
- Actual Cost
- Depreciation
- Market Worth / Value
- Replacement cost comparison
- Cost of competing for an asset with respect to capabilities
Intangible Asset Valuation
- Definite Intangible Assets: Intangible assets have some expiry period. These assets lose their importance and value when the patent expires.
- Indefinite Intangible Assets: Assets have an indefinite expiration period.
For to approximate the value of an intangible asset, the following methods are considered generally acceptable
- The cost to create and to replace the asset
- Capitalization of Historic Profits
- Cost Avoidance or Savings
Reporting
A security professional must maintain proper documentation and reports of each event and incident. Reporting is an important part of information security as it helps to save time when the same conditions are met in the future. The report may be technical or non-technical.
Reports contain:
- Task did by each personnel
- Methods & tools used.
- Findings
- Recommendations
- Collected information from different phases
Risk Management Framework (RMF)
RMF is an information security framework. The goals of RMF are as follows:
- Improve information security
- To strengthen risk management processes
- Encourage reciprocity among federal agencies
RMF includes a six-step life cycle process:
- Categorization of information systems
- Selection of security controls
- Implementation of security controls
- Assessment of security controls
- Authorization of information systems
- Monitoring of security controls
